Two-Factor Authentication (2FA) for Jamf Connect
Jamf Connect 2FA (Two-Factor Authentication) or Multi-Factor Authentication (MFA) is an additional layer of security in which a user or an organizational employee have to provide two factors to gain access to the Jamf Connect account. With Jamf Connect TFA being enabled, anyone trying to login to your Jamf Connect account from an unrecognized computer/device must provide additional authorization. Authentication starts with a user submitting his traditional username and password. Once the user successfully gets authenticated with the 1st step verification, configured 2FA (OTP over SMS, Push Notifications, YubiKey, TOTP, Google Authenticator etc) method prompts for 2nd-step verification. After successfully authenticating with both of the steps a user is granted with the access to the Jamf Connect account. This extra layer prevents the unauthorized person from accessing the resources even if cyber attackers get to know your credentials.
miniorange provides 15+ authentication methods and solutions for various use cases. It allows users and organizations to set up certain authentication and settings which includes password restrictions, restricting sign-in methods, as well as other security settings. miniorange also makes way for authentication apps that support Time-Based One-Time Password (TOTP) Google Authenticator, Microsoft Authenticator, Authy 2-Factor authentication app and our own miniorange Authenticator app.
Connect with External Source of Users
miniOrange provides user authentication from various external sources, which can be Directories (like ADFS, Microsoft Active Directory, OpenLDAP, AWS etc), Identity Providers (like Microsoft Entra ID, Okta, AWS), and many more. You can configure your existing directory/user store or add users in miniOrange.

miniOrange
Authenticator App

Google
Authenticator App

Authy 2-Factor
Authentication App

Microsoft
Authenticator App
Prerequisites for enabling MFA on regular mac login:
- JAMF Connect Login
- JAMF Connect Configuration
Follow the Step-by-Step Guide for setting up MFA with JAMF connect configuration.
1. Create an OIDC application in miniOrange
- Go to miniOrange dashboard and login with your admin account.
- Select Apps and click on add application.
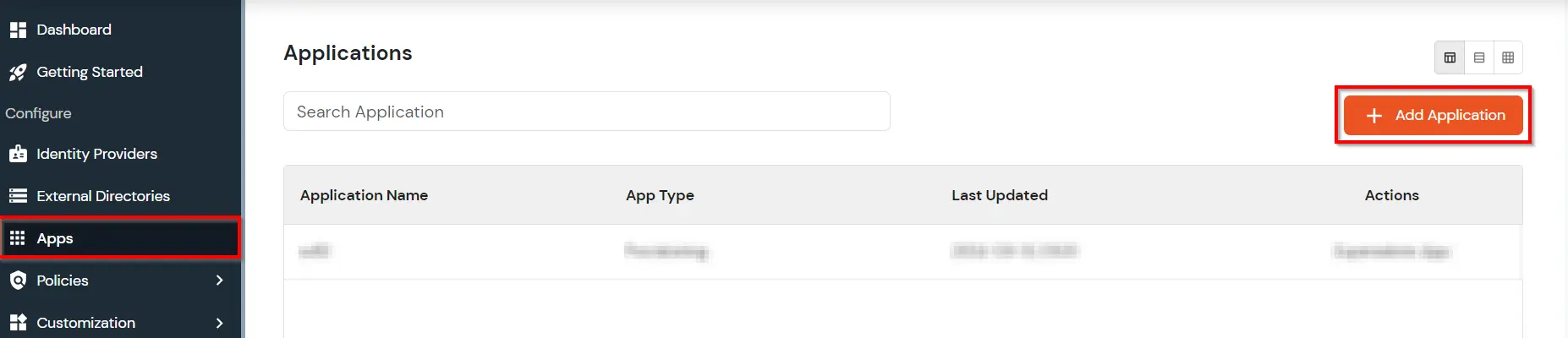
- In Choose Application Type click on OAUTH/ODIC application type.
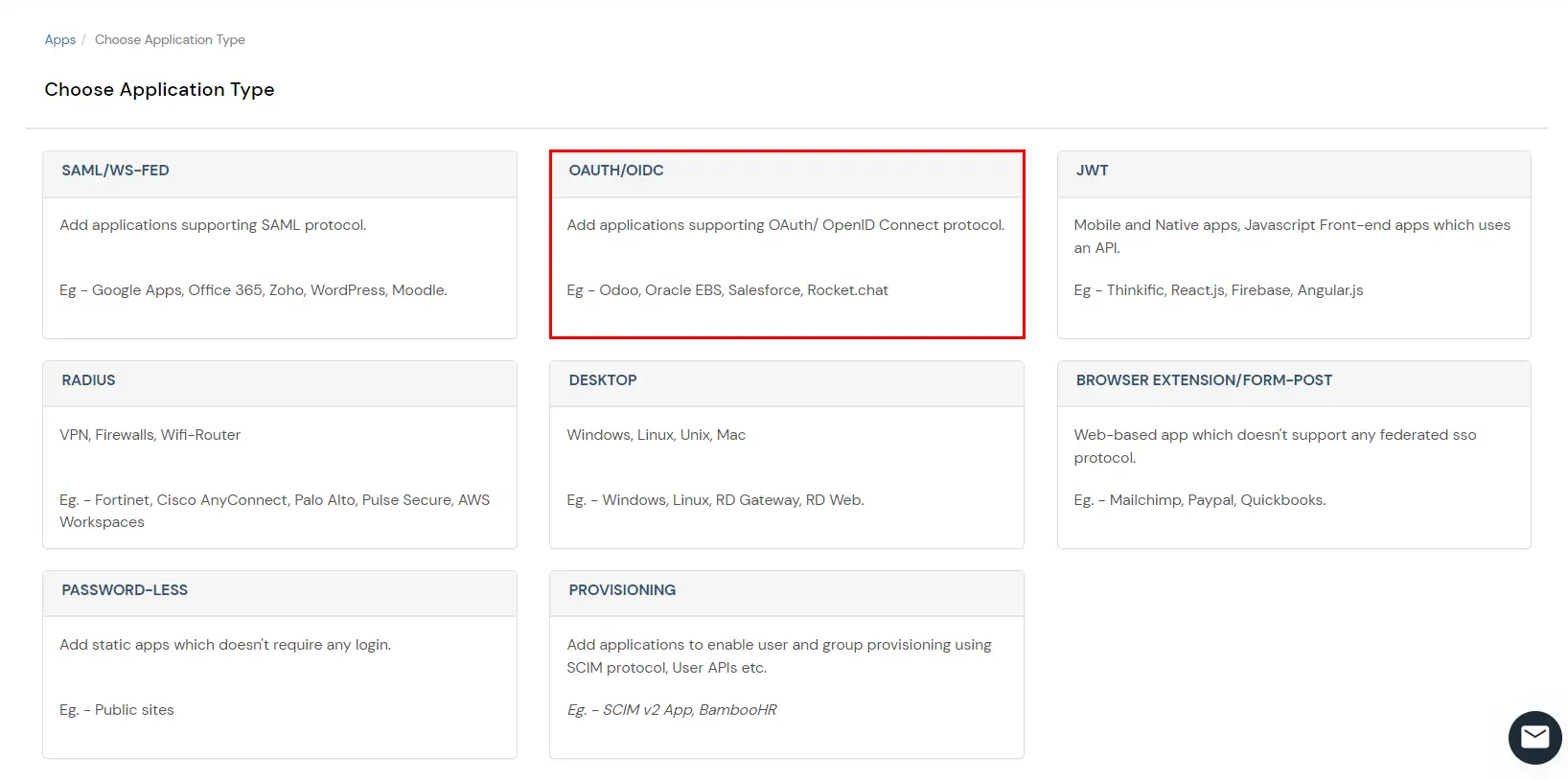
- In OAUTH/OIDC Protocol and click on OAuth2/OpenID Connect app.

- On the Basic settings tab add the following details and Click on Save.
|
Client Name:
|
Jamf Connect |
|
Redirect URL:
|
https://127.0.0.1/jamfconnect |
- Click on the select button in the left and click on edit button of the recently created application.
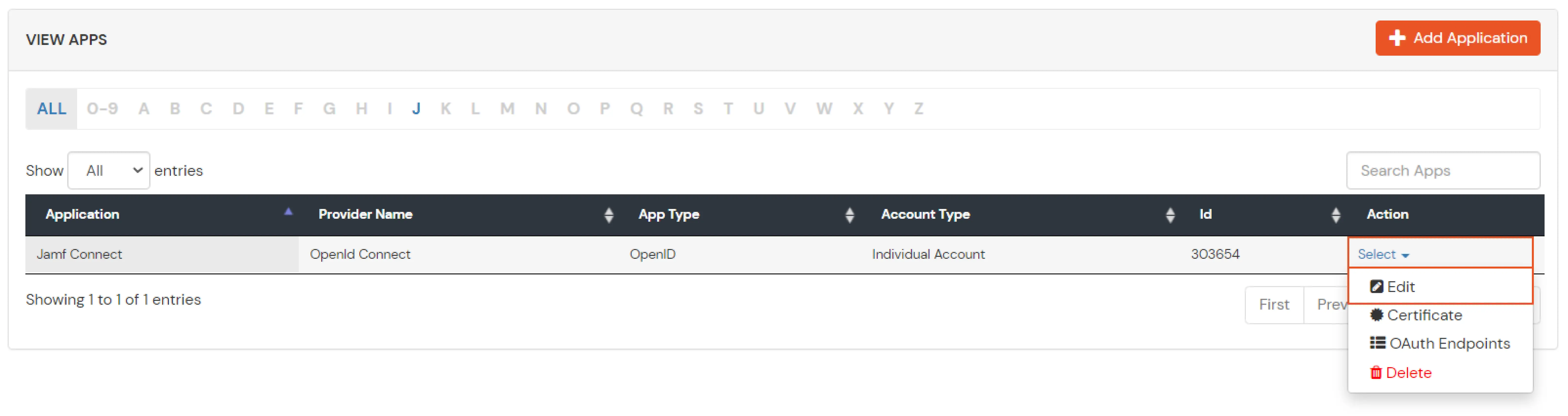
- Copy the Client ID and Client Secret for later Use.
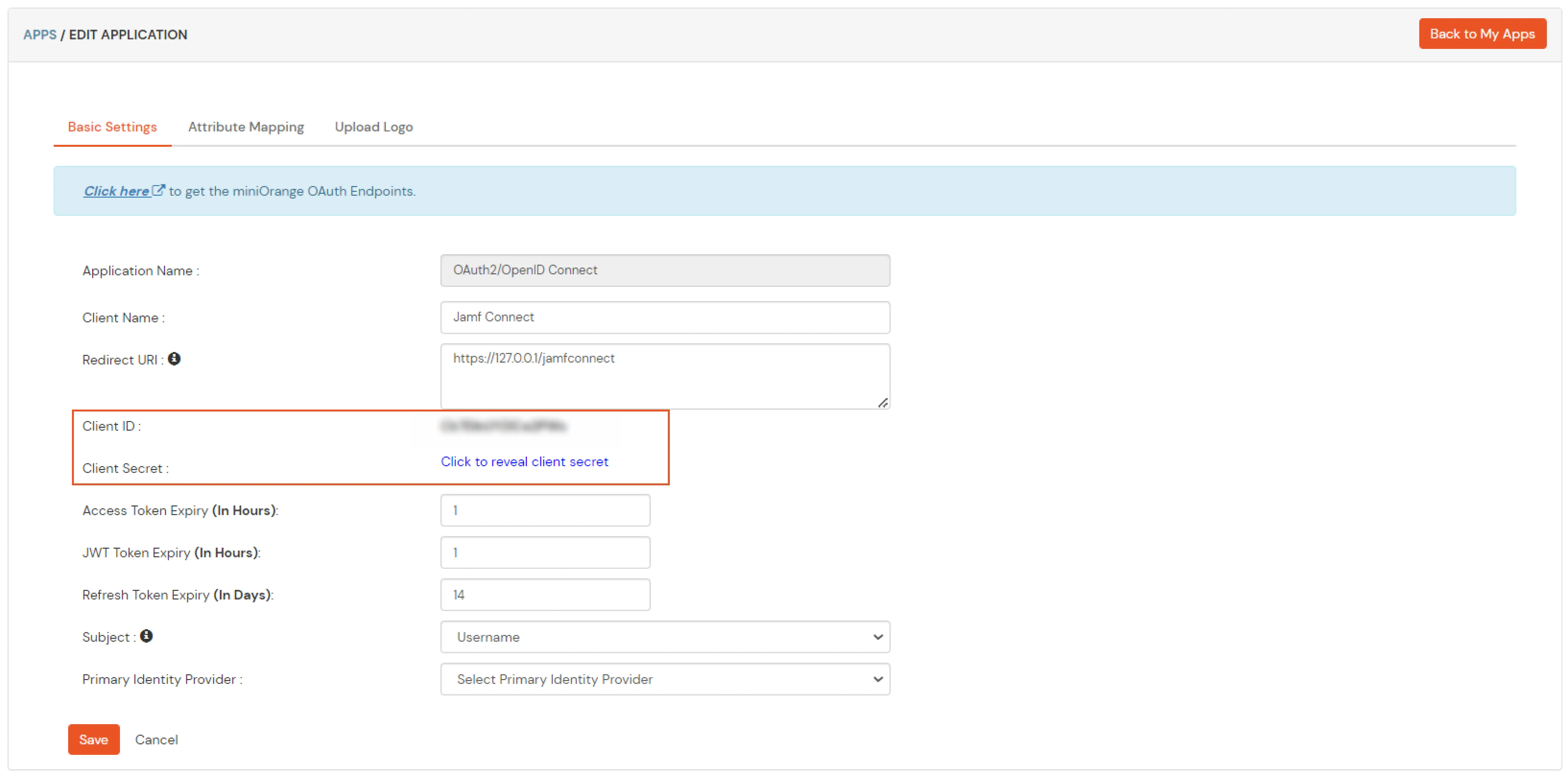
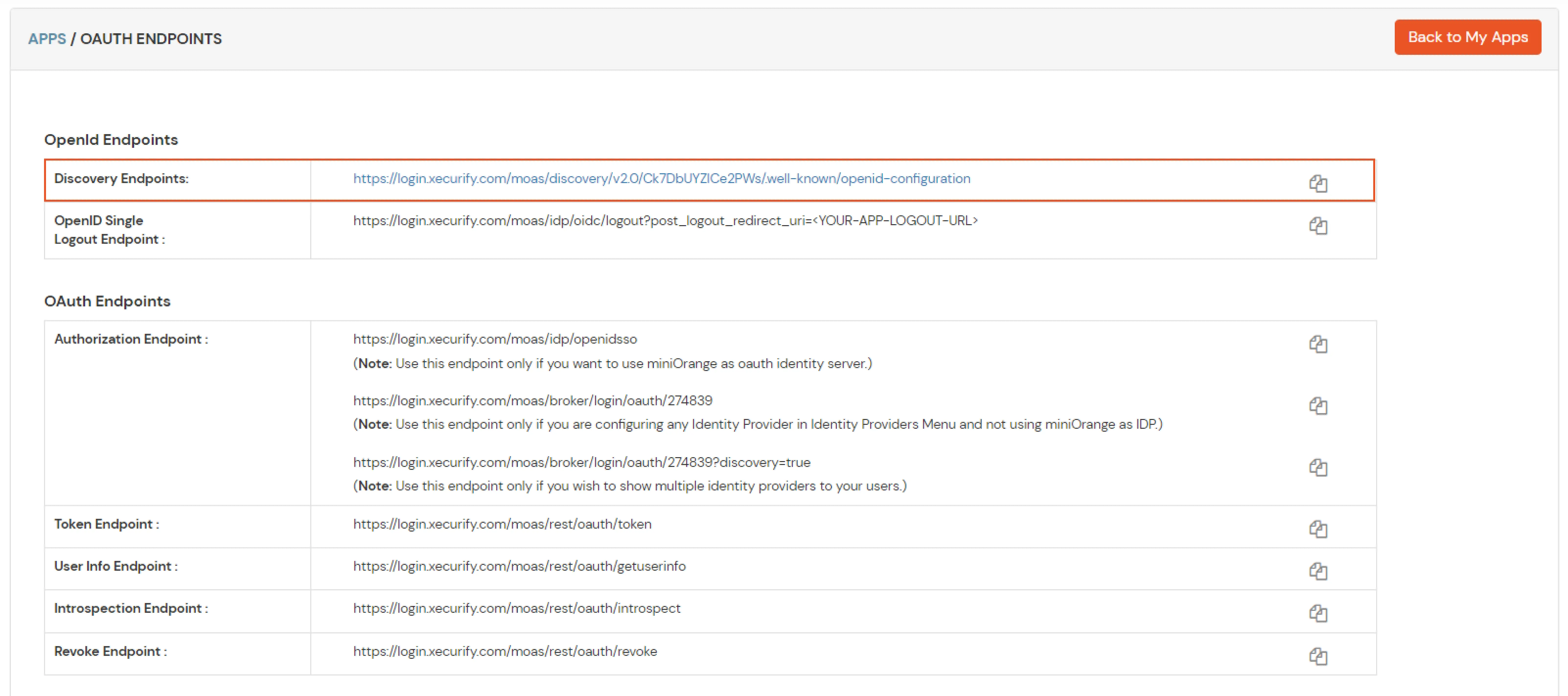
- Copy the discovery URL from the applications menu and click on OAuth Endpoints.
- Example Discover URL: https://branding.xecurify.com/moas/discovery/v2.0/lXDwTpNI6ymPcRI/.well-known/openid-configuration
2. Configure JAMF connect
- Open JAMF Connect application in the Applications for creating a configuration profile (A configuration profile contains details of your identity provider from where your user authentication needs to be done)
- Choose Custom in the identity provider and paste the OIDC ID we got from the miniOrange settings.
- Enter the same value in the ROPG cliend ID.
- Enter the Client Secret we got from miniOrange.
- Enter the Discovery URL in the Discovery URL field.
- In the Redirect URL field enter https://127.0.0.1/jamfconnect
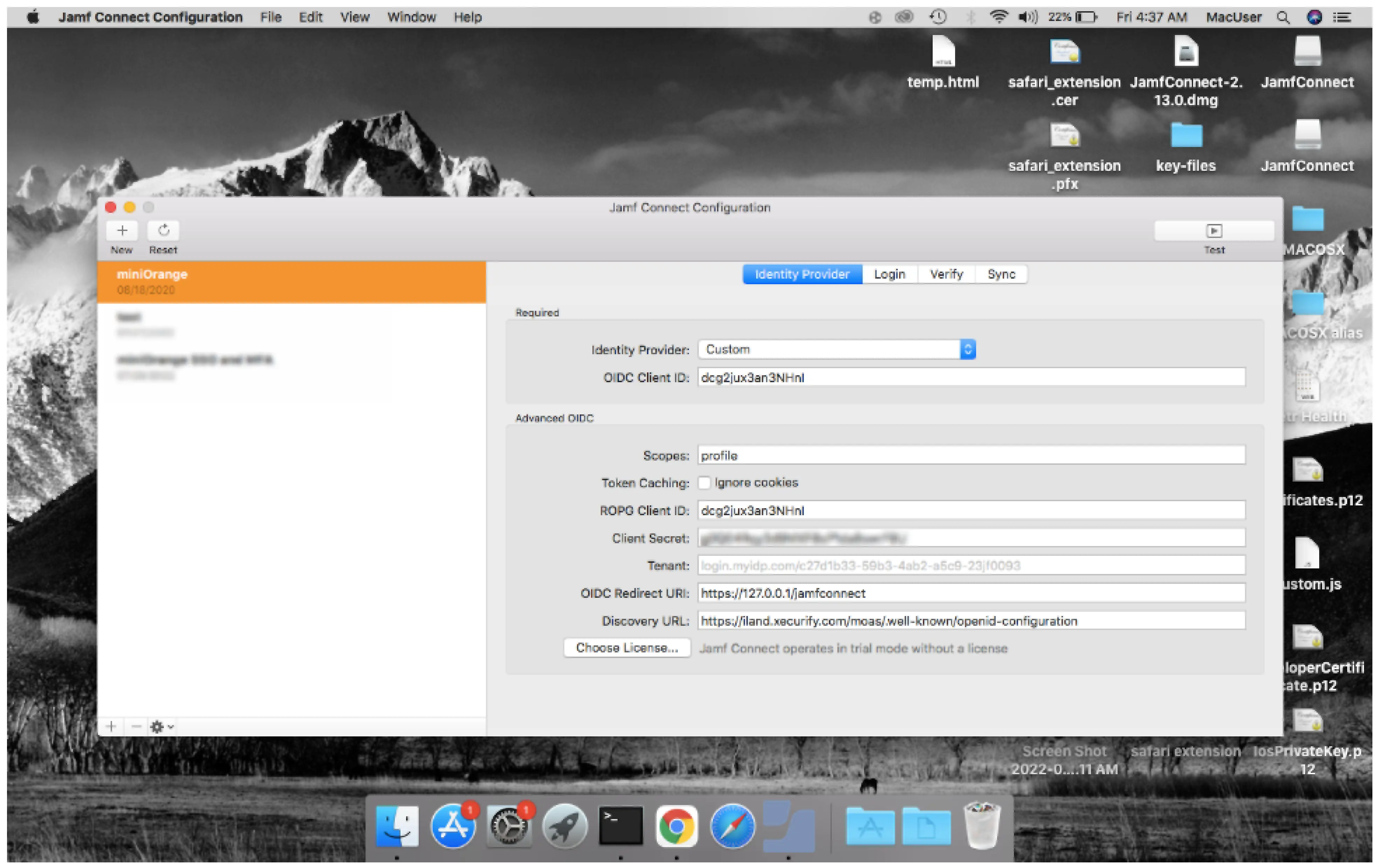
- Do not enter any values in the Scopes.
- In the Login tab, enable the Allow local authentication if a network unavailable, this will give you the local authentication option in case if the IDP is not reachable.
Test the configuration with the top right button if everything is working fine then save these configuration with mobileconfig extension. This configuration profile can be pushed in the machines in which you want to add the mfa/sso.
3. Install the configuration file and enable OIDC login:
- Open the configuration file you created with the above steps.
- Install the file by giving the permissions
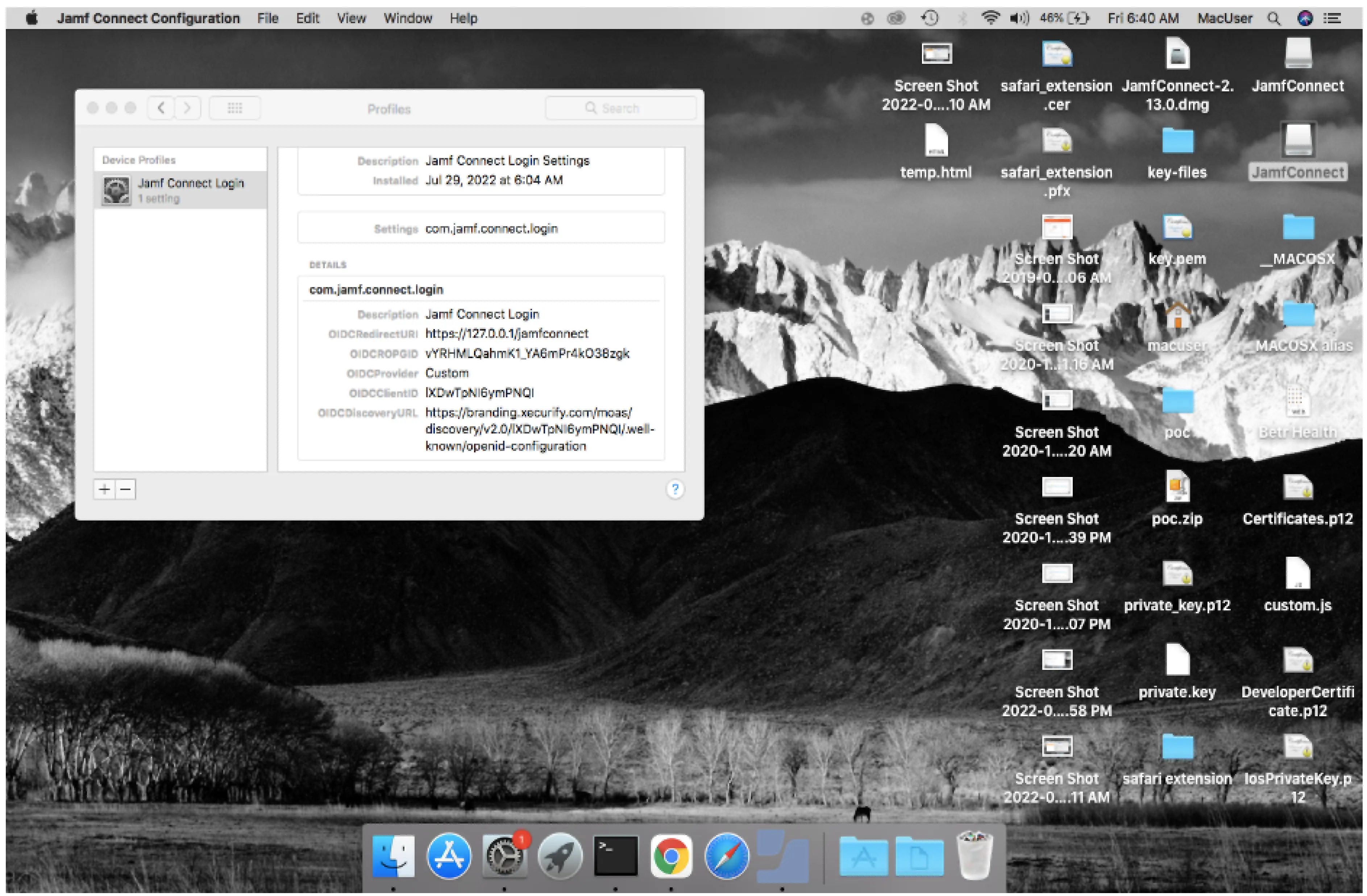
- Once the installation is done open the terminal.
- Go to /Library/Security/SecurityAgentPlugins/JamfConnectLogin.bundle/Contents/MacOS/ location for enabling the OIDC authentication with the regular authentication.
- Run the command authchanger -OIDC
4. Test the configuration:
- Logout and try to login again it will open a window like below which will forward you for authentication with miniOrange.
- Enter the IDP credentials to login.
Remove the OIDC authentication (If Required):
- Additional Steps are provided if the OIDC authentication needs to be Removed or Disabled.
- To diable the OIDC authentication and re-enable the local authentication go to /Library/Security/SecurityAgentPlugins/JamfConnectLogin.bundle/Contents/MacOS/
- Run the below command authchanger -reset
External References








