Need Help? We are right here!
Search Results:
×Vendor Privileged Access Management (VPAM) controls and monitors third-party vendor access, ensuring they have only the minimum access needed to perform tasks, reducing risks of unauthorized actions.
Tailored for external vendors, VPAM secures high-level accounts that may access sensitive data, like financial records or customer information, protecting against malicious activities or accidental leaks while allowing organizations to work securely with external partners.







Vendor Privileged Access Management (VPAM) functions in the following ways:
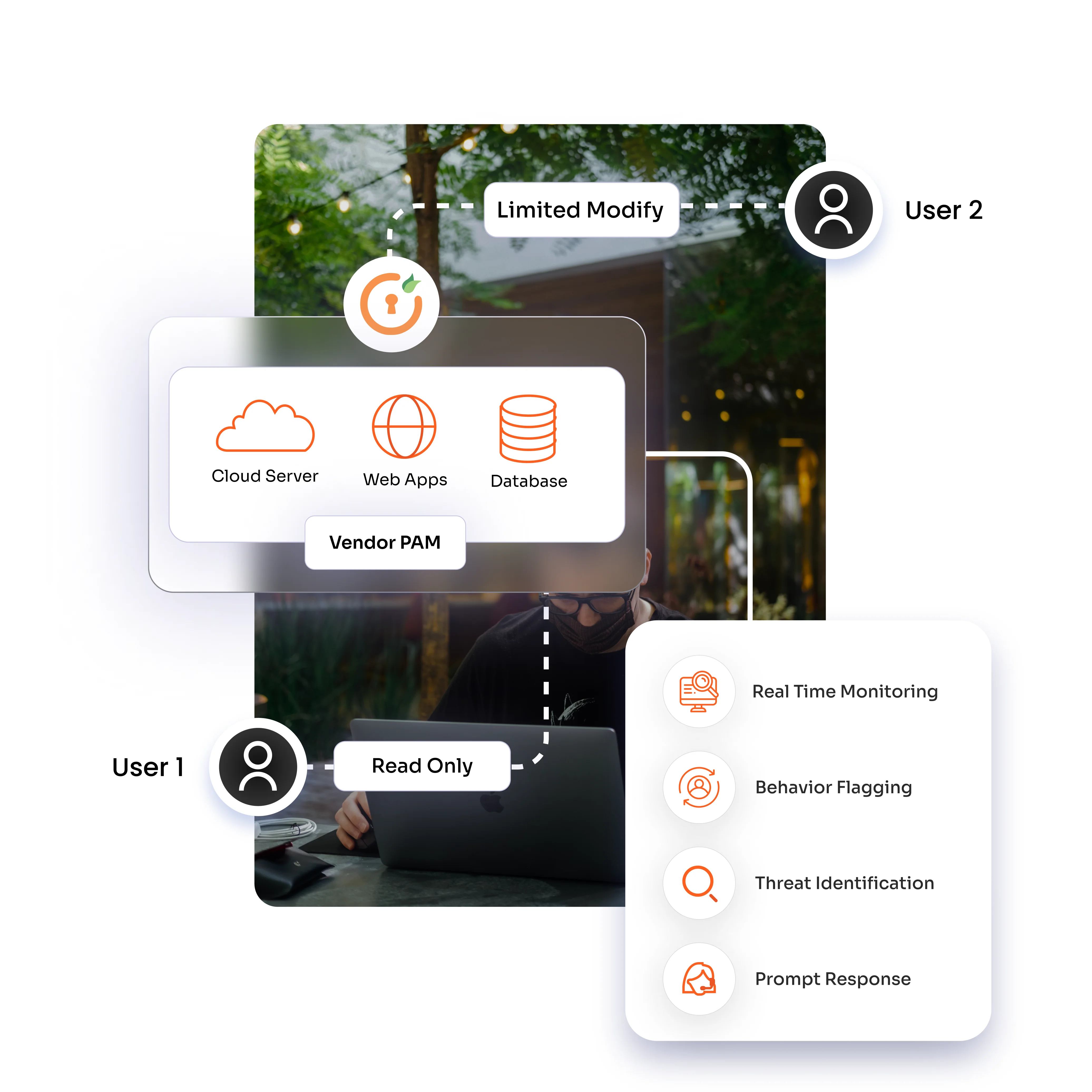
Set specific access policies for each vendor, determining which resources they can access and what actions they can perform (e.g., read-only or limited modifications).
Ensure vendors only interact with necessary resources, minimizing the risk of unauthorized actions.
Monitor all vendor activities in real-time, logging interactions and flagging suspicious behavior.
Identify potential security threats early and respond promptly to protect critical systems.
Vendor access management is optimized by limiting access to only necessary resources and providing just-in-time provisioning for enhanced security.
Implement Multi-factor authentication (MFA) and automate vendor credential rotation to ensure credentials are always secure and up-to-date.
Identity and access management vendors enable full session monitoring and logging, offering complete visibility into vendor activities for compliance and audit purposes.
Secure and monitor third-party remote access with solutions tailored for vendor remote access, ensuring safe connectivity for external partners.
Integrates with Zero Trust frameworks and enforces the Principle of Least Privilege (PolP), ensuring vendors have the minimal access required to perform their tasks.
Benefits of Vendor Privileged Access Management (VPAM)
VPAM allows password-less and VPN-less access for vendors, providing fast and secure access via biometric MFA.

Automatically isolate and monitor vendor sessions, securing privileged access to protect against potential threats.

Grant just-in-time access to vendors without adding their identities to Active Directory (AD), streamlining operations.

Our Other Identity & Access Management Products