Need Help? We are right here!
Search Results:
×Risk-based authentication is an authentication method in which a security mechanism uses contextual data to determine the level of risk associated with a particular authentication request. It is a form of adaptive authentication or step-up authentication that enables organizations to assess the potential risk of a given authentication attempt based on factors such as the user's location, device, behavior, and past history.
By using risk-based authentication services, organizations can reduce the risk of unauthorized access to their systems while minimizing the inconvenience to legitimate users. This approach can also help organizations meet regulatory requirements for stronger authentication measures without imposing unnecessary burdens on users.







Users are presented with appropriate Multi-Factor Authentication (MFA) challenges based on risk profile. This forces the user to authenticate using the configured MFA method with enhanced security.
Any device that supports a Web browser can use Risk-Based Adaptive MFA. In addition, we also provide the same functionality via APIs.
Admin can track all the user activities, manage access, and add security policies for users on a granular level.
Eliminates the need for frequent authentication through a fixed approach. For the calculation of the threats and decisions, the session attributes of the user are fetched during runtime.
Our centralized management console allows you to deploy, monitor, and manage MFA across all your Linux systems from a single location. Easily set policies, manage users, and ensure compliance with security standards.
Users can be grouped together and given access to specific applications according to their roles based on different access policies.
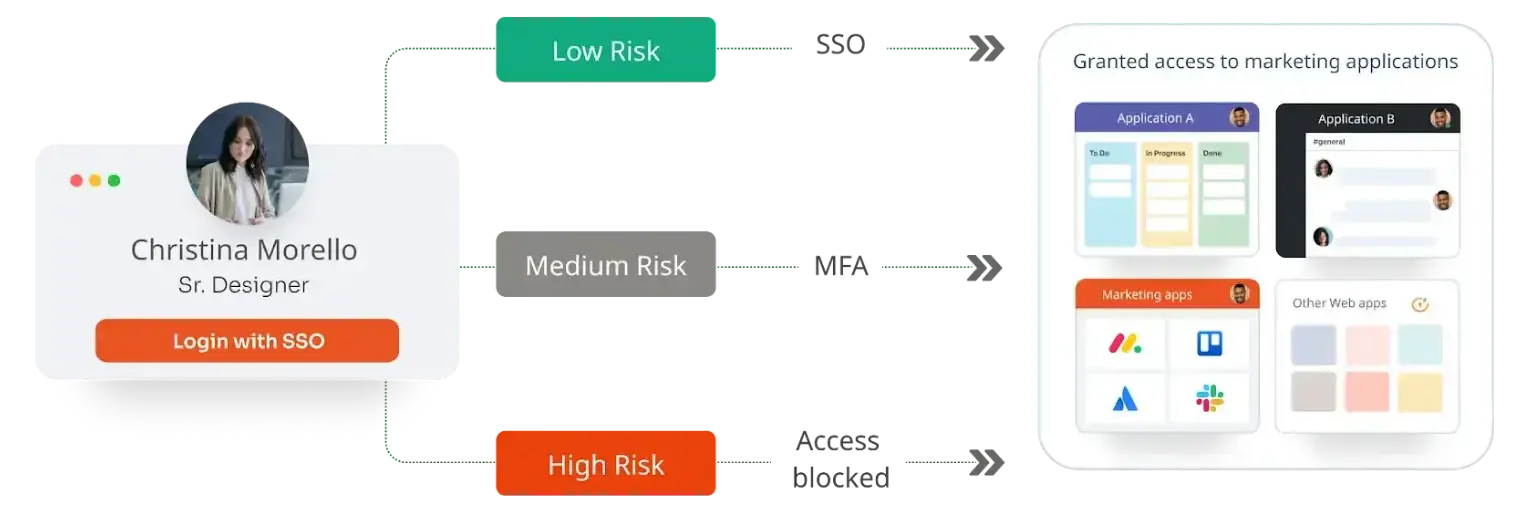
The score, which is generated in real-time, is used to categorize connections as low, medium, or high risk. The user is presented with a different authentication requirement based on their estimated level of risk.
If risk-based authentication detects a target that may pose a significant risk, the system may ask for more MFA techniques or refuse access completely. For example, When a consumer of Internet banking asks for a significant transfer of funds to an external account, a high-risk RBA score is generated. Such a sensitive transaction would prompt additional MFA methods, even if typical risk indications such as the IP address and user behavior check out.
When using IP Restriction as risk-based authentication, IP addresses are configured and enlisted by the admin, and access is either allowed or denied accordingly. When a user attempts to log into one of the risk-based authentication-enabled apps, his IP address is checked against the preset IP list, and appropriate action is taken (i.e. Allow, Deny or Challenge).
In Location-based Risk-Based Authentication restriction, the admin shortlists and configures a list of Geo-locations. Based on the location restrictions set by the admin, end-users are either allowed or denied the login. When a user tries to login with Risk-Based Authentication enabled, his location attributes such as are verified against the location list configured by the admin, and based on this user will be either allowed, challenged, or denied access to resources.
Using Device-based Risk-Based Authentication, the admin allows end-users to add a set number of trusted devices (A device refers to a Browser Session). A registered device allows a person to log in without restriction once it has been registered. An administrator will challenge or deny a person's registration if their registered device exceeds their total limit.
Risk-Based Authentication also includes a time restriction, which starts with an admin setting up a time zone with a Start and End Time. Users are permitted, refused, or challenged based on the defined timezone and policies. As soon as an end-user attempts to log in with risk-based authentication enabled, his time zone parameters, such as time zone and system time, are compared to the list defined by the admin, and the user is either granted access, rejected access, or challenged access, depending on his configuration.
*Please contact us to get volume discounts for higher user tiers.
RBA improves data and system security and makes advanced authentication mechanisms simple to install, which assists enterprises in meeting regulatory compliance requirements.
Risk-based authentication streamlines the authentication process by minimizing steps, thus reducing user inconvenience and enhancing the overall user experience compared to traditional methods.
Risk-based authentication, combined with cloud-based services, offers a cost-effective alternative to traditional methods. It's advantageous for smaller organizations lacking resources for complex authentication measures.
Two-factor authentication is a security measure that requires two forms of identification to access an account or system.
An advanced level of authentication with two or more levels of security factors such as OTP over SMS, TOTP tokens, OTP over Email, hardware tokens etc.
It provides an additional layer of MFA security based on risk and access provided by the security admin to control user access.
The team at miniOrange has been great with supporting our needs for MFA within our organization. The support staff are knowledgeable and very easy to communicate with if an issue or question arises.
— IT Security, Healthcare and Biotech Industry
With miniOrange, we could easily enforce MFA across all our Linux desktops, significantly reducing the risk of unauthorized access. The centralized management makes it easy to maintain and monitor our security policies
— Security Administrator, Global Enterprise
