Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×
miniOrange Outlook SSO (Single Sign-on) product provides ready integrations and a seamless SSO experience to Outlook, Office 365, Sharepoint, other microsoft apps, and all other web and SaaS applications for all your users. Single Sign-On (SSO) for Microsoft Outlook provides you secure auto-login to your apps. It allows enterprises to quickly increase security of information and resources without worrying about time for initial set up or future upgrades.
Microsoft Outlook Single Sign-on (SSO) solution by miniOrange identity platform provides an option to integrate with multiple third-party Identity Providers which supports standard protocols like SAML, OAuth, etc. IDP here means (Okta, Auth0, Ping, Onelogin, etc) or Active Directory (AD) where your existing users are managed. Once your Outlook Single sign-on (SSO) is enabled with your IDP / Directory successfully, your employees or end users will be able to authenticate and login into their Outlook account and other integrated applications with the use of existing username password. They won't need to create or manage credentials differently to operate Outlook account or any other app account. Given below is the setup guide to configure SAML SSO for your Outlook.
In this flow, the user tries to access to the Serivce Provider (Outlook) organization directly. The request is redirected to the third-party Identity Provider by miniOrange Identity platform for authenitcation. On sucessfull authentication from the third-party Identity provider, the user is given access to the application (service provider).
In this flow, the user logs in or access to the miniOrange Identity platform using his credentials. Now the user can access any of the organization's configured Service Providers (Outlook, other Microsoft apps, etc.) through the Identity Provider admin console without having to enter the credentials agian.
miniOrange provides user authentication from various external sources, which can be Directories (like ADFS, Microsoft Active Directory, OpenLDAP, AWS etc), Identity Providers (like Microsoft Entra ID, Okta, AWS), and many more. You can configure your existing directory/user store or add users in miniOrange.
1. Sync On-Premise Active Directory with Microsoft Entra ID
NOTE: If you want to use your On-Premise Active Directory as a user store to Single Sign-On into Microsoft Outlook then follow the below steps to sync your AD and Microsoft Entra ID.
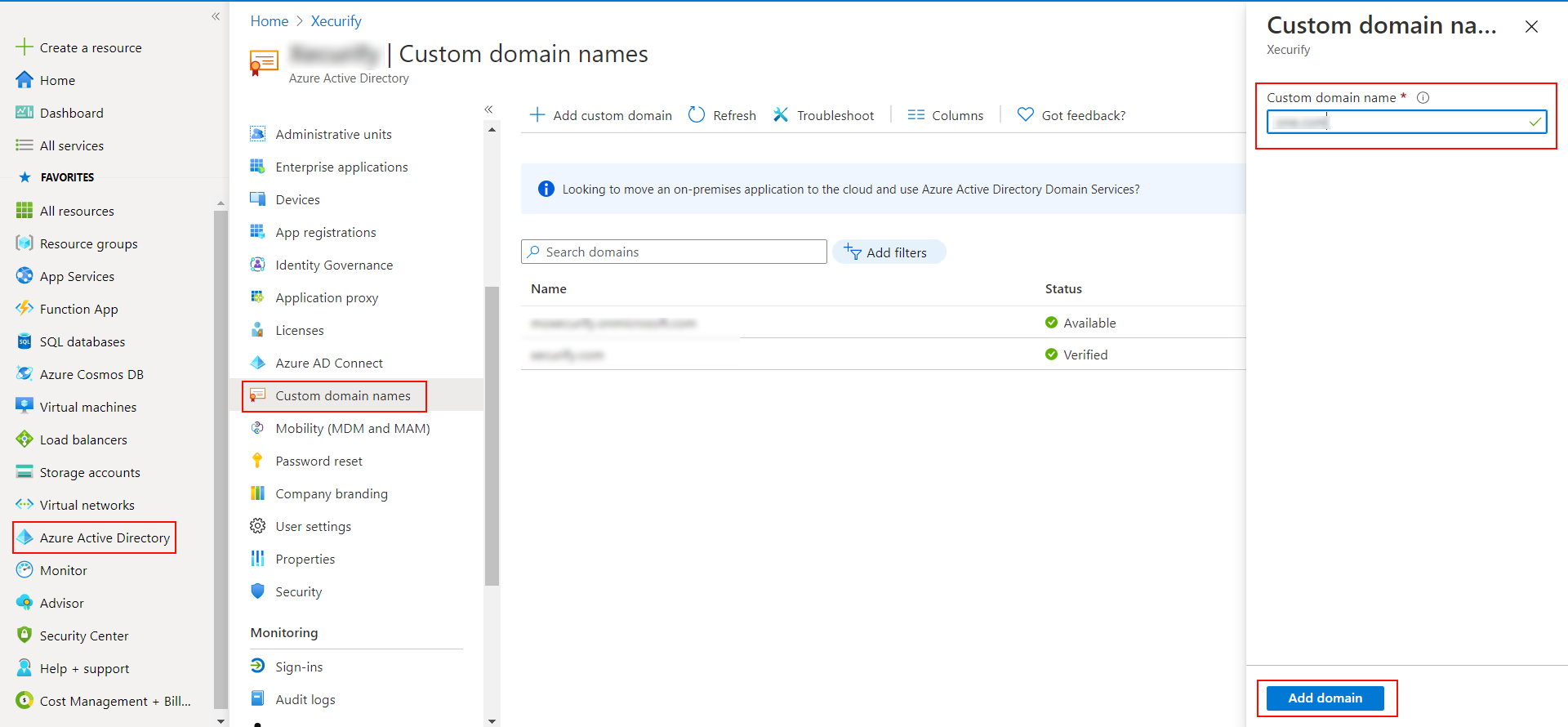
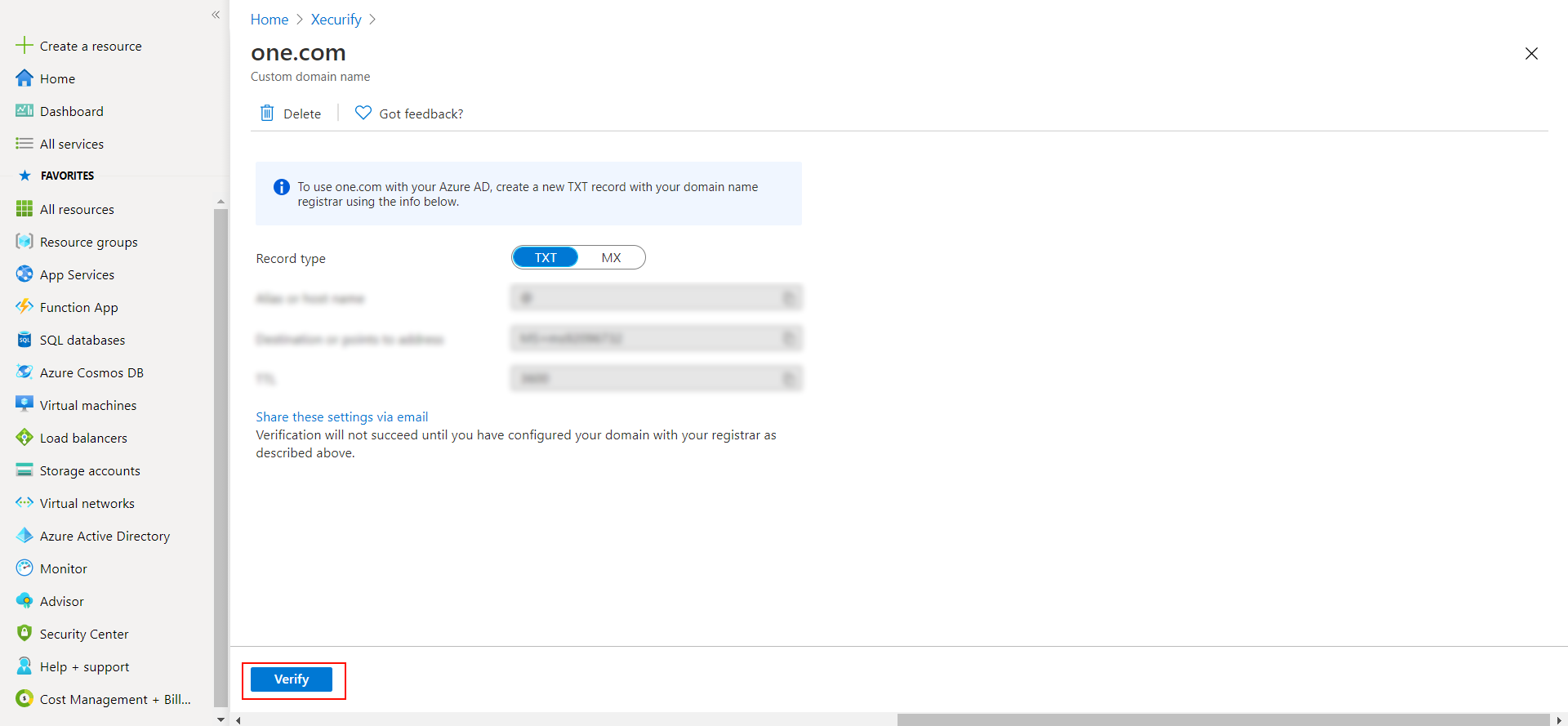
2. Verify your UPN Domain in Azure Portal
Please make sure your organisation branding is already set under Customization >> Login and Registration Branding in the left menu of the dashboard.

urn:federation:MicrosoftOnlinehttps://login.microsoftonline.com/login.srf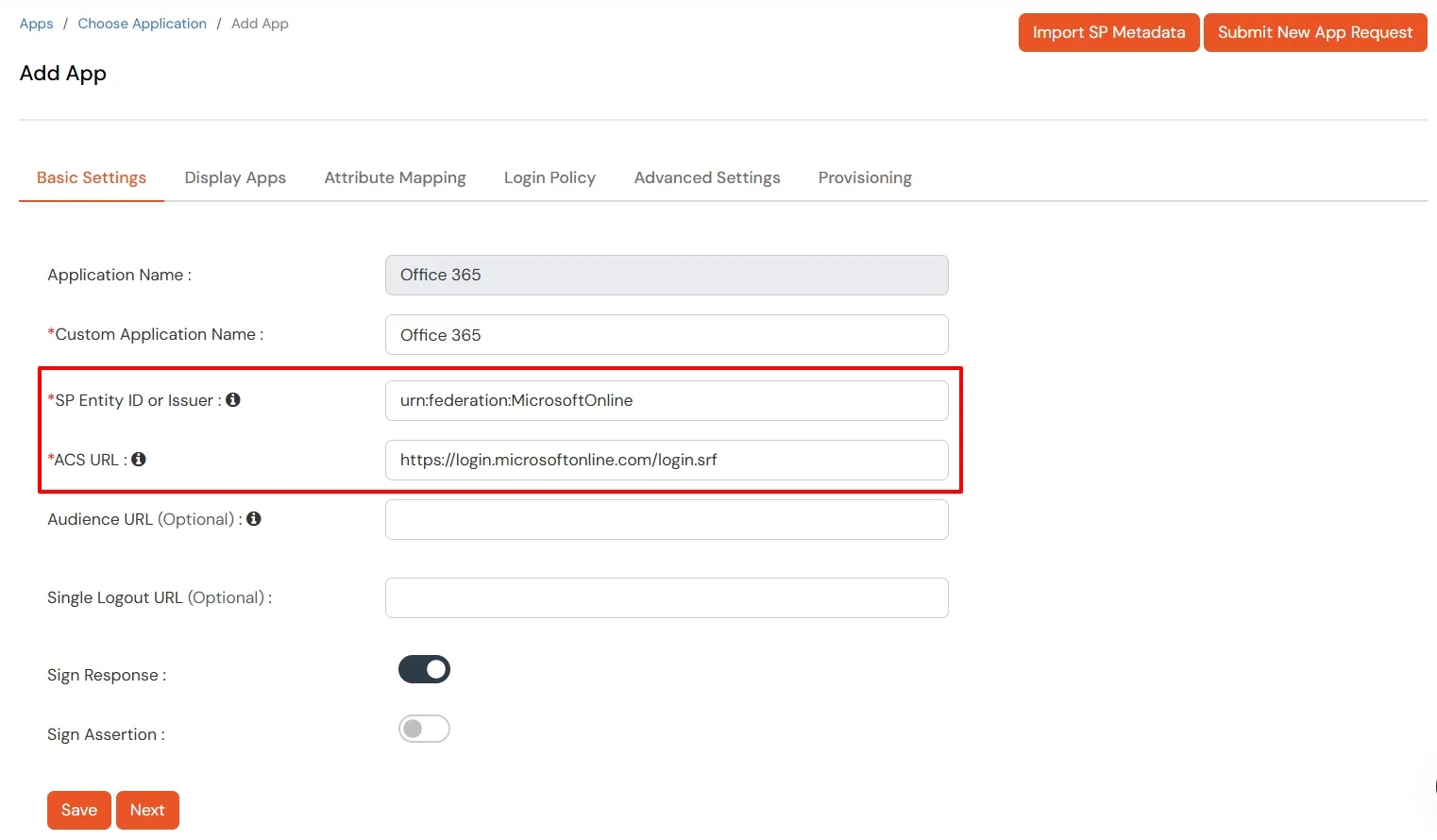
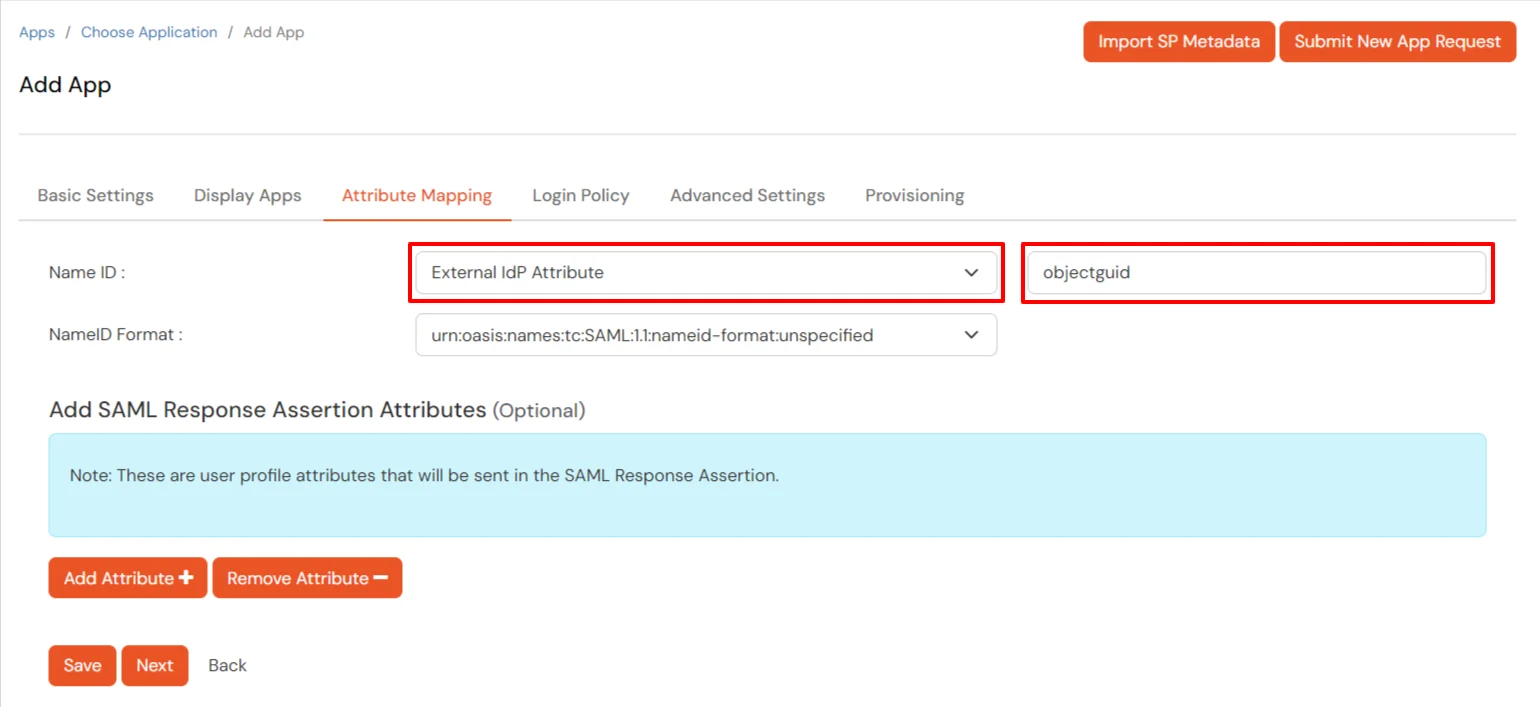
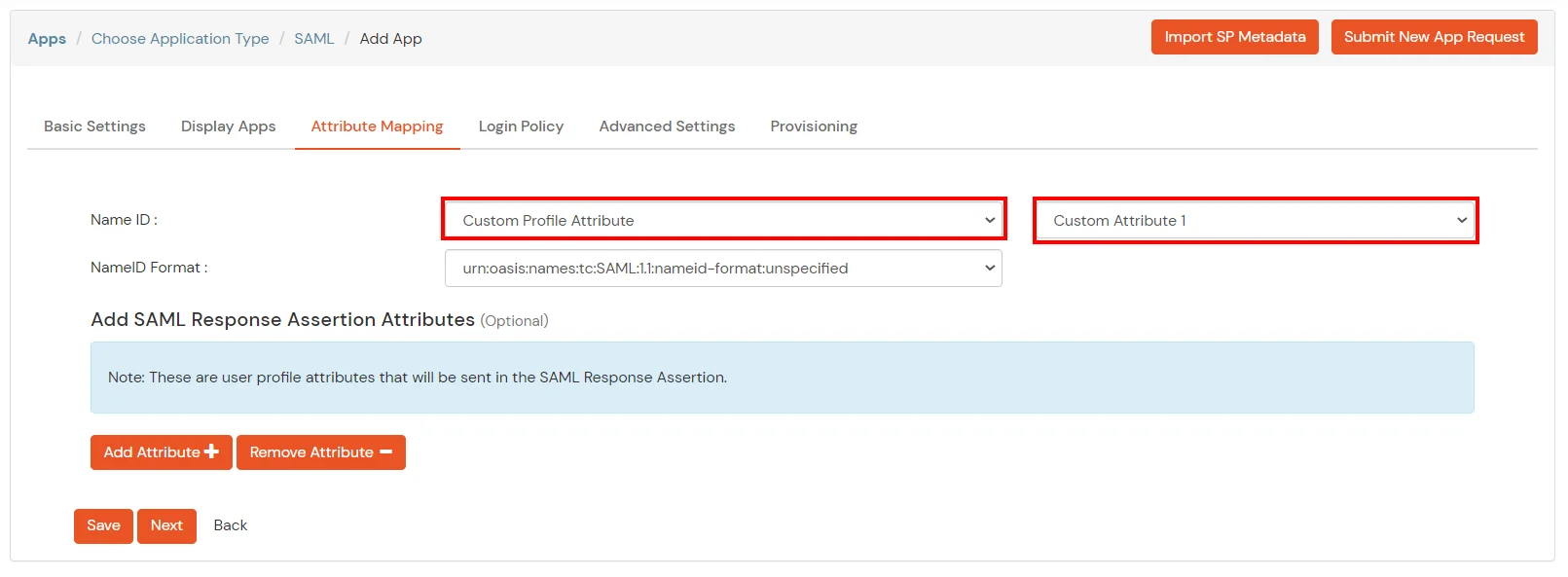
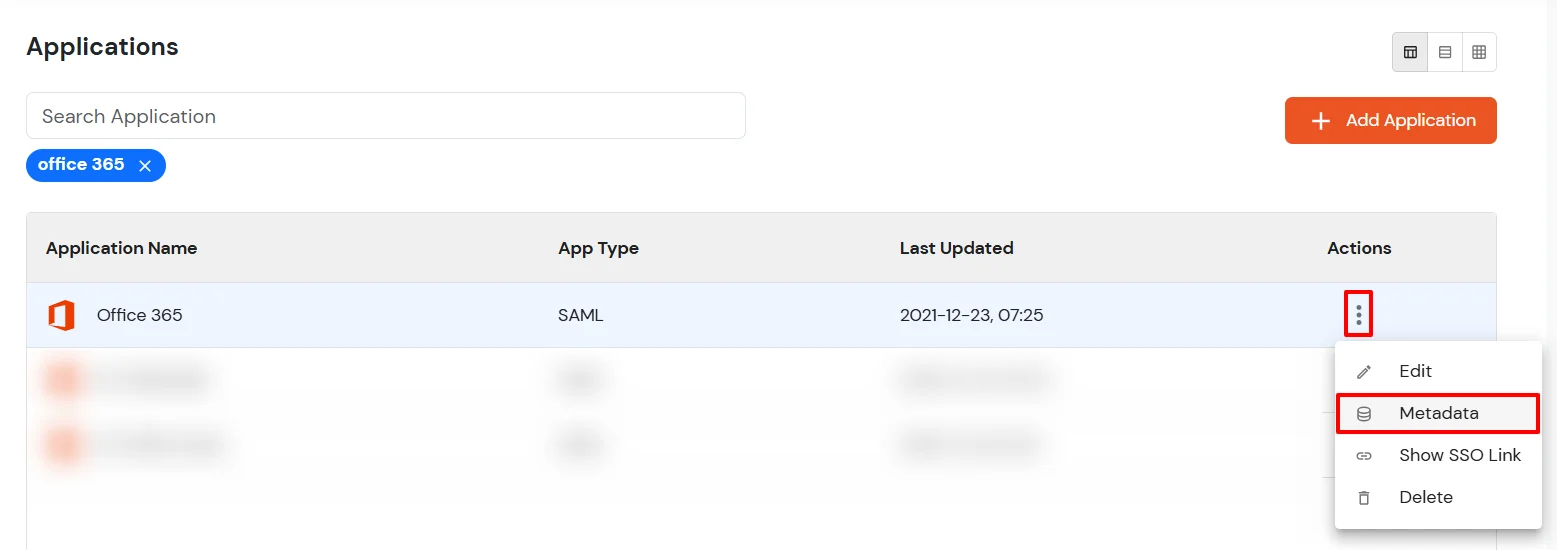
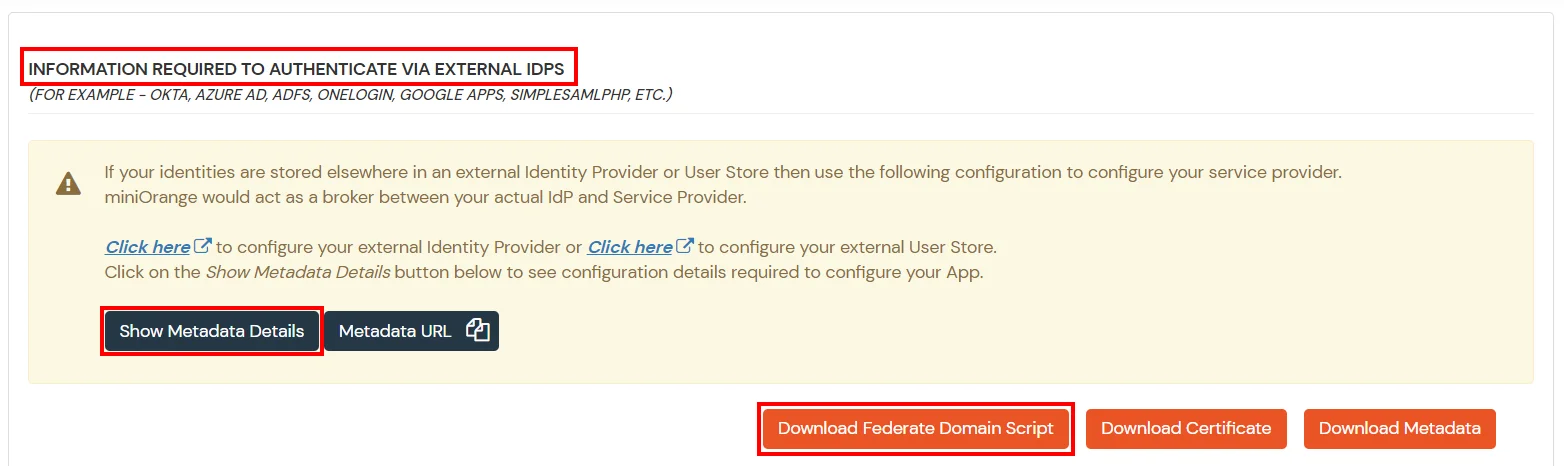
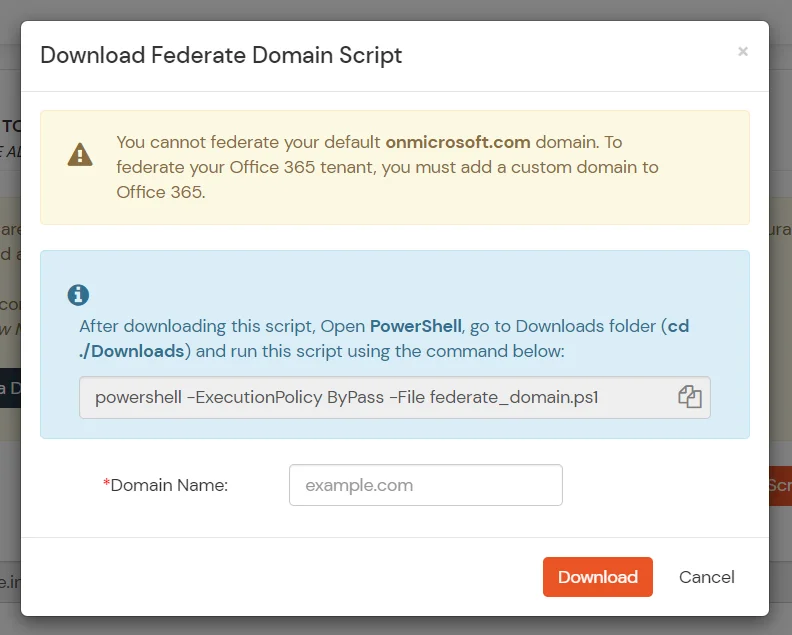
cd ./Downloads
powershell -ExecutionPolicy ByPass -File federate_domain.ps1
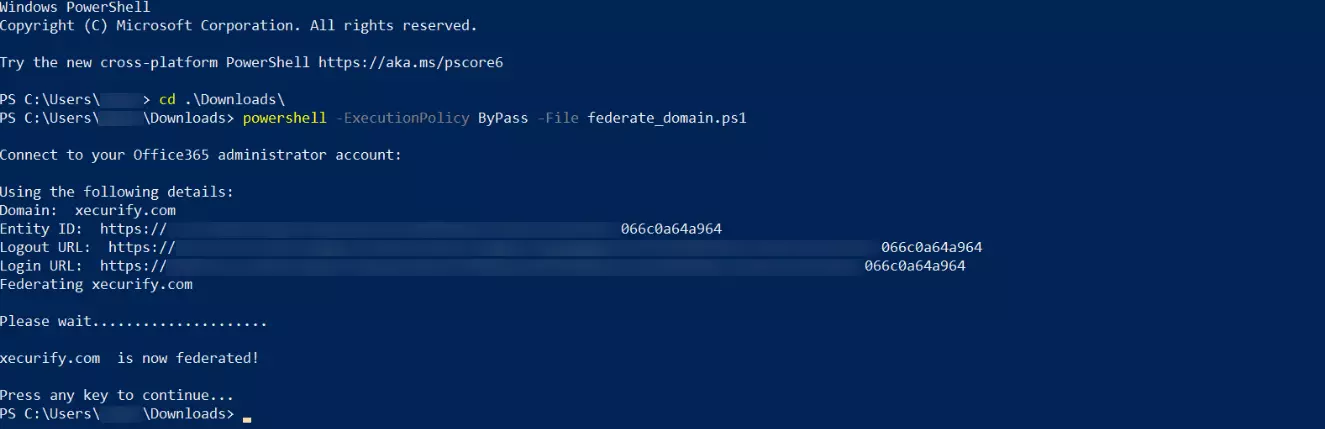
Get-MgDomain -DomainId "<domain>" | Select-Object Id, AuthenticationType
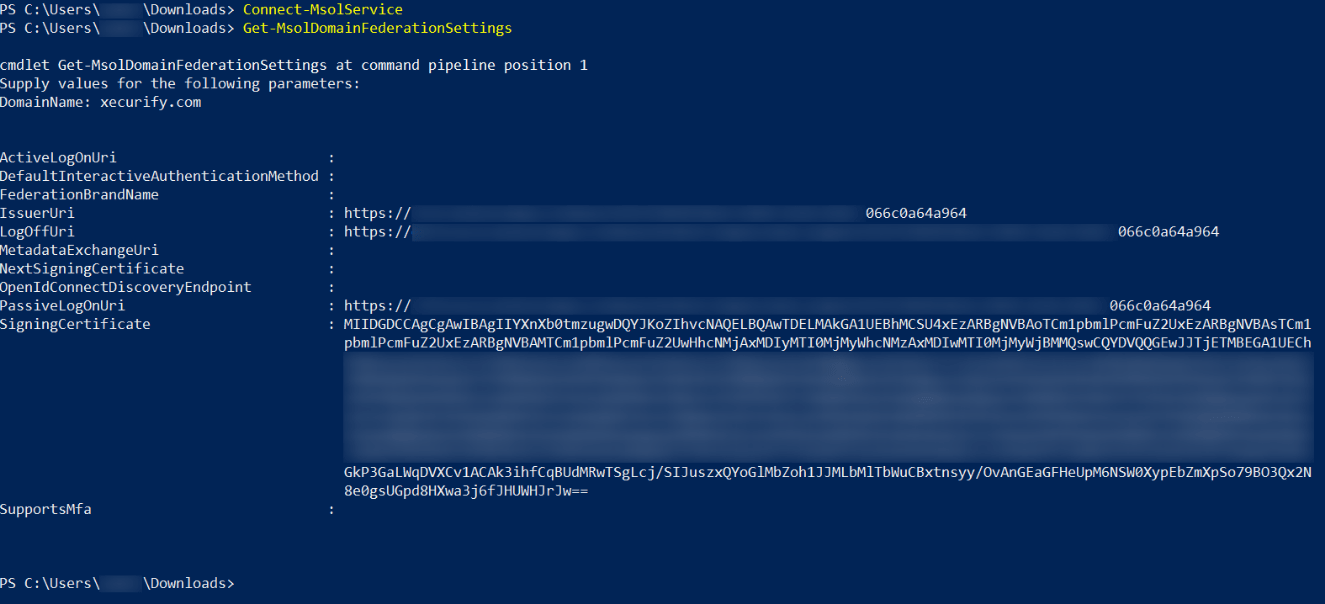
1. Using SP initiated login :-
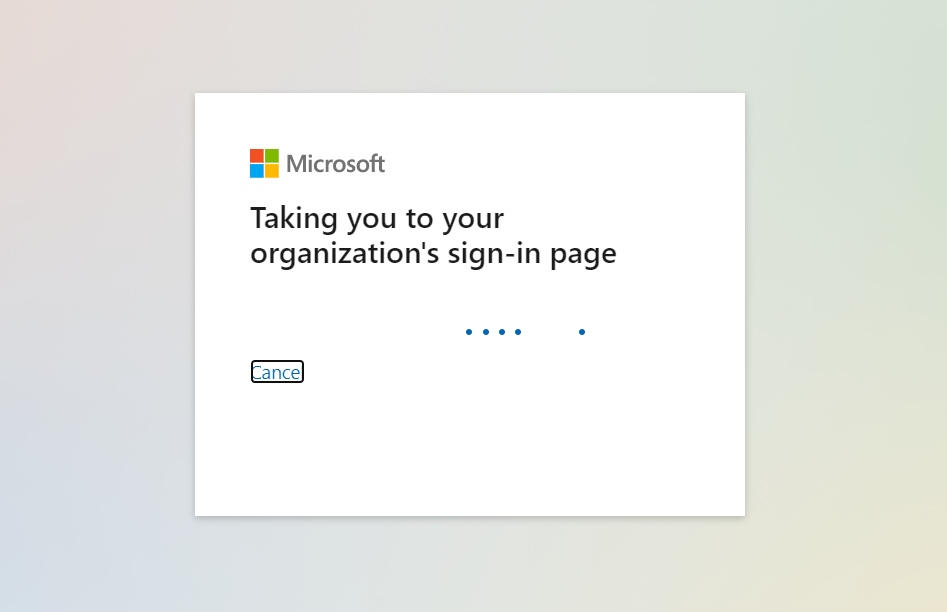

2. Using IdP initiated login :-

Our Other Identity & Access Management Products