How to Enable Multi-factor Authentication (MFA/2FA) for Remote Desktop (RDP)
RDP MFA solution is a crucial security measure to protect remote access to systems and servers. Implementing RDP MFA involves configuring Multi-Factor Authentication, integrating it with the RDP server, and configuring the authentication policies.After enabling RDP MFA, when a user attempts to connect to the remote system via RDP, they will be prompted to provide their regular username and password, as well as the additional factor of authentication, which could be a one-time code generated by a mobile app, Microsoft Authenticator, or a biometric scan. When both factors are successfully verified then only the user gains access to the remote system.
Enabling Multi-factor authentication (MFA) reduces the risk of unauthorized access even if credentials are compromised. Similarly, MFA can be Implemented for Windows Local logon.
miniOrange 2FA/MFA Credential Provider for Windows logon and Remote Desktop Protocol (RDP) access supports following Multi-Factor Authentication (MFA) Methods:-
| Authentication Type | Method | Supported |
|---|
| miniOrange Authenticator | Soft Token | |
| miniOrange Push Notification | |
| Mobile Token | Google Authenticator | |
| Microsoft Authenticator | |
| Authy Authenticator | |
| SMS | OTP Over SMS | |
| SMS with Link | |
| Email | OTP Over Email | |
| Email with Link | |
| Call Verification | OTP Over Call | |
| Hardware Token | YubiKey Hardware Token | |
| Display Hardware Token | |
System Requirements for miniOrange RDP Credential Provider to enable 2FA
miniOrange Credential Provider supports both client and server operating systems.
Supported Microsoft Windows Client versions:
- Windows 7 SP1
- Windows 8.1
- Windows 10
- Windows 11
Supported Windows Server versions (GUI and core installs):
- Windows Server 2008 R2 SP1
- Windows Server 2012
- Windows Server 2012 R2
- Windows Server 2016
- Windows Server 2019
- Windows Server 2022
Apart from the Windows operating system, miniOrange supports 2FA for MAC and Linux operating systems.
Get Free Installation Help - Book a Slot
miniOrange offers free help through a consultation call with our System Engineers to Install or Setup Two-Factor/Multi-Factor Authentication (MFA) for Remote Desktop Protocol (RDP) solution in your environment with 30 days trial.
For this, you need to just send us an email at idpsupport@xecurify.com to book a slot and we'll help you setting it up in no time.
Prerequisites to setup Windows & RDP MFA
- .NET Framework 4.8
- miniOrange Cloud Account or On-premise Setup.
- Enroll Users in miniOrange before Configuration:
- The username of the user in miniOrange should be the same as in Windows Username.
- This is required so that the service can prompt the appropriate 2FA for the customer based on the defined policy and provide secure access to machine/RDP.
- There are multiple methods to add users in miniOrange.
- Admin can add end users
- Setup user provisioning from your existing identity source or Active directory.
miniOrange Two-Factor Authentication (2FA/MFA) Credential Provider for Remote Desktop (RDP) Protocol and Windows logon also requires .NET Framework 4.5 or later. If the correct .NET version is not present on your system then miniOrange Credential Provider setup prompts you to install the .NET Framework and can also be installed via group policy software publishing and Group policy administrative templates.
Step by Step guide to setup Two-Factor Authentication (2FA/MFA) for RDP and Windows Logon
1. Download 2FA Module
2. Setup your miniOrange dashboard for Windows 2FA
In this step, we are going to setup your 2FA preferences, such as:
- Which users should be asked for 2FA during windows logon.
- What 2FA methods can they use.
2.1 Adding app and policy for 2FA
- Login into miniOrange Admin Console.
- Go to Apps and click on Add Application button.
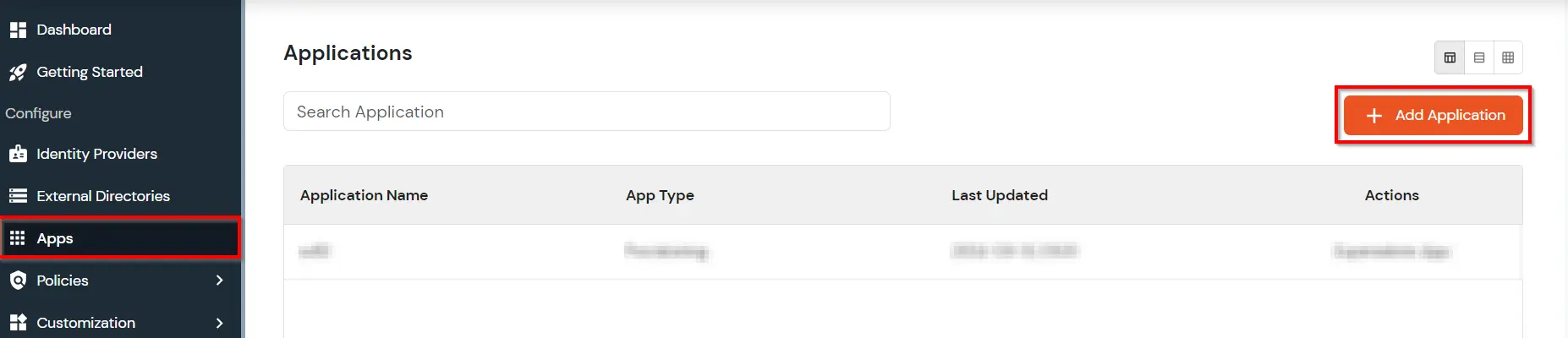
- In Choose Application Type click on Create App button in Desktop application type.
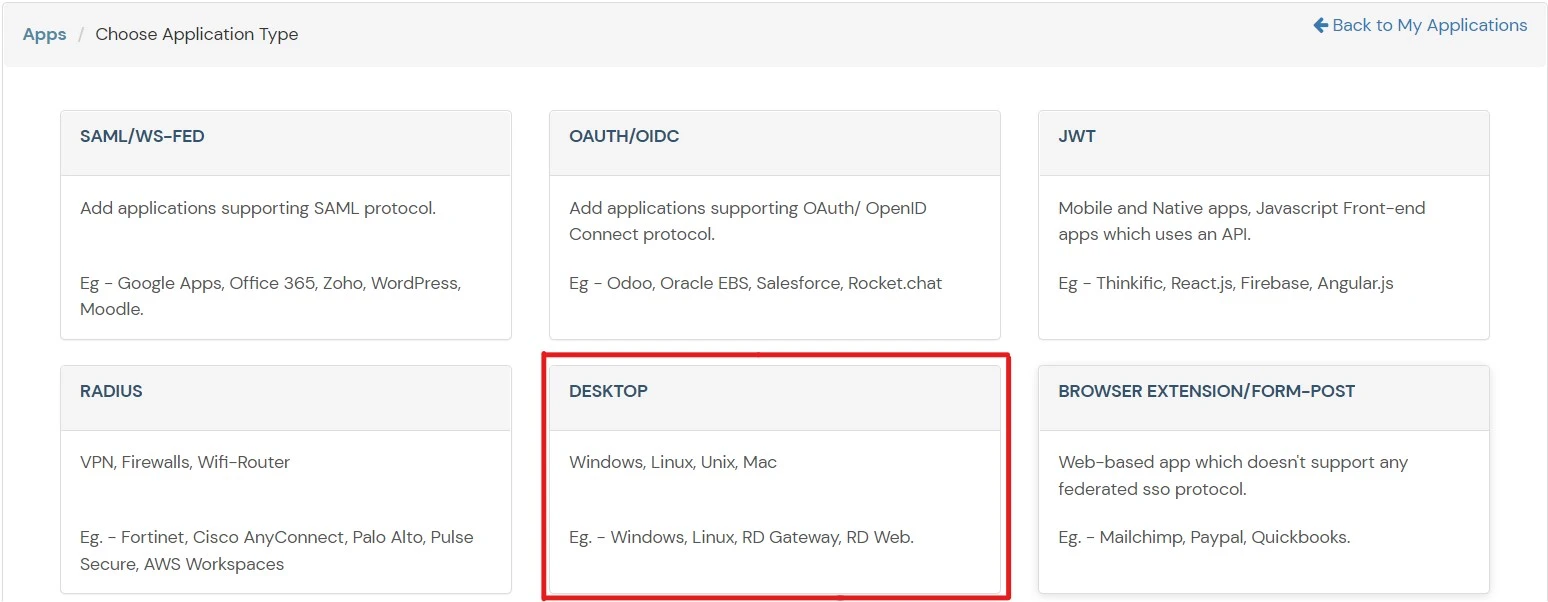
- Add Windows app on miniOrange.

- Add App Name.
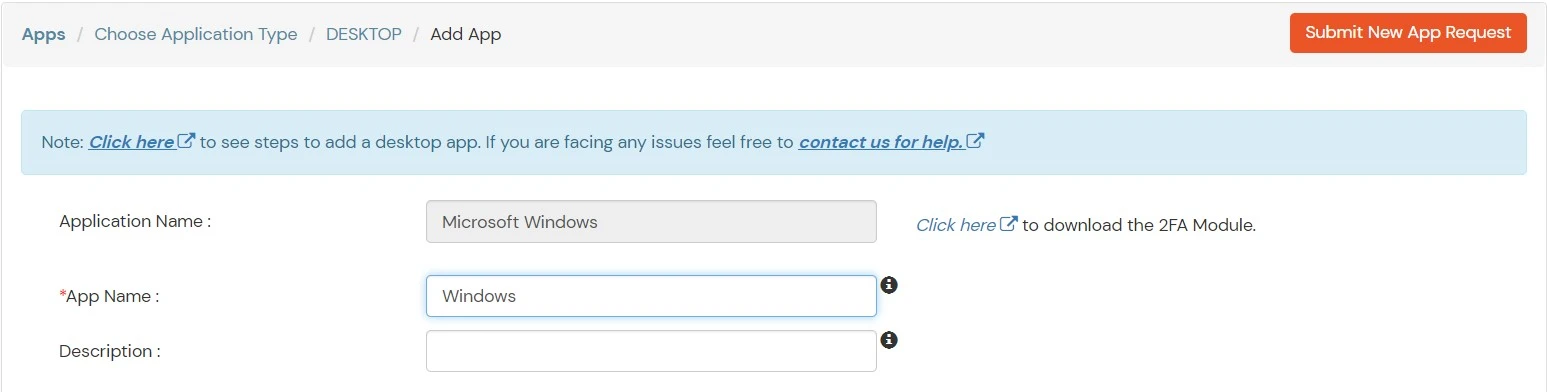
- Select Login Method as Password and Enable 2-Factor Authentication (2FA).
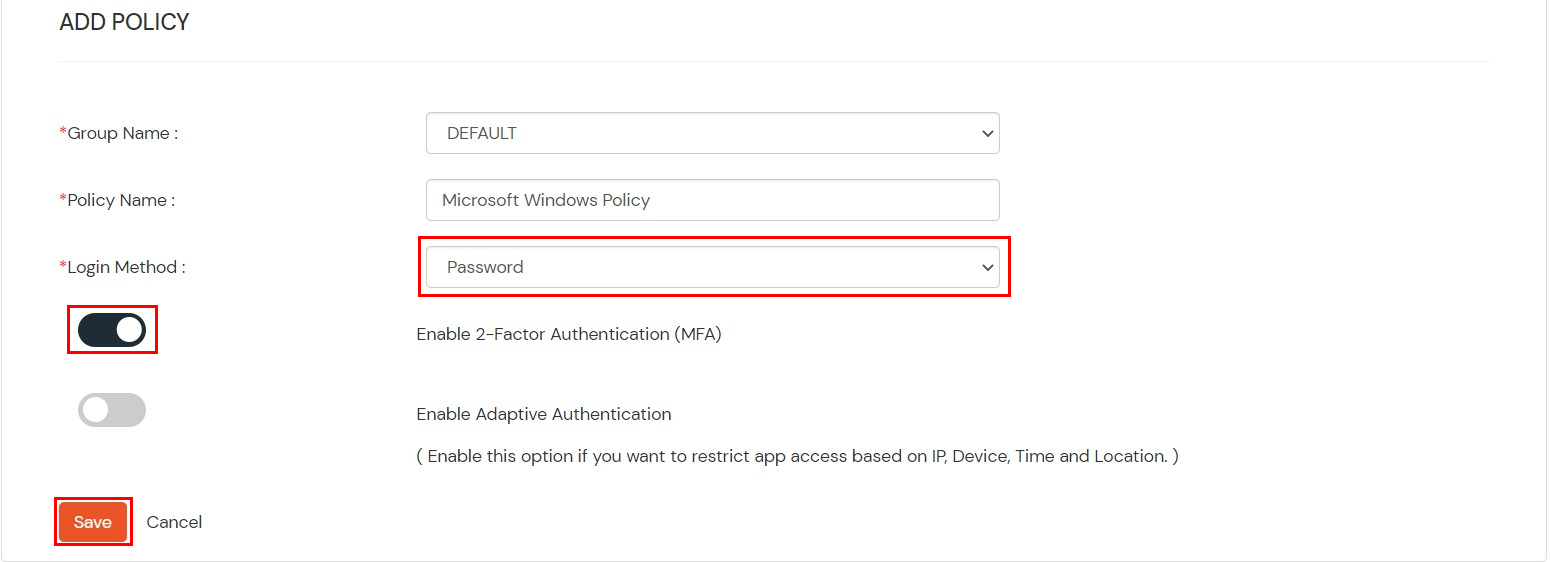
- Click on Save.
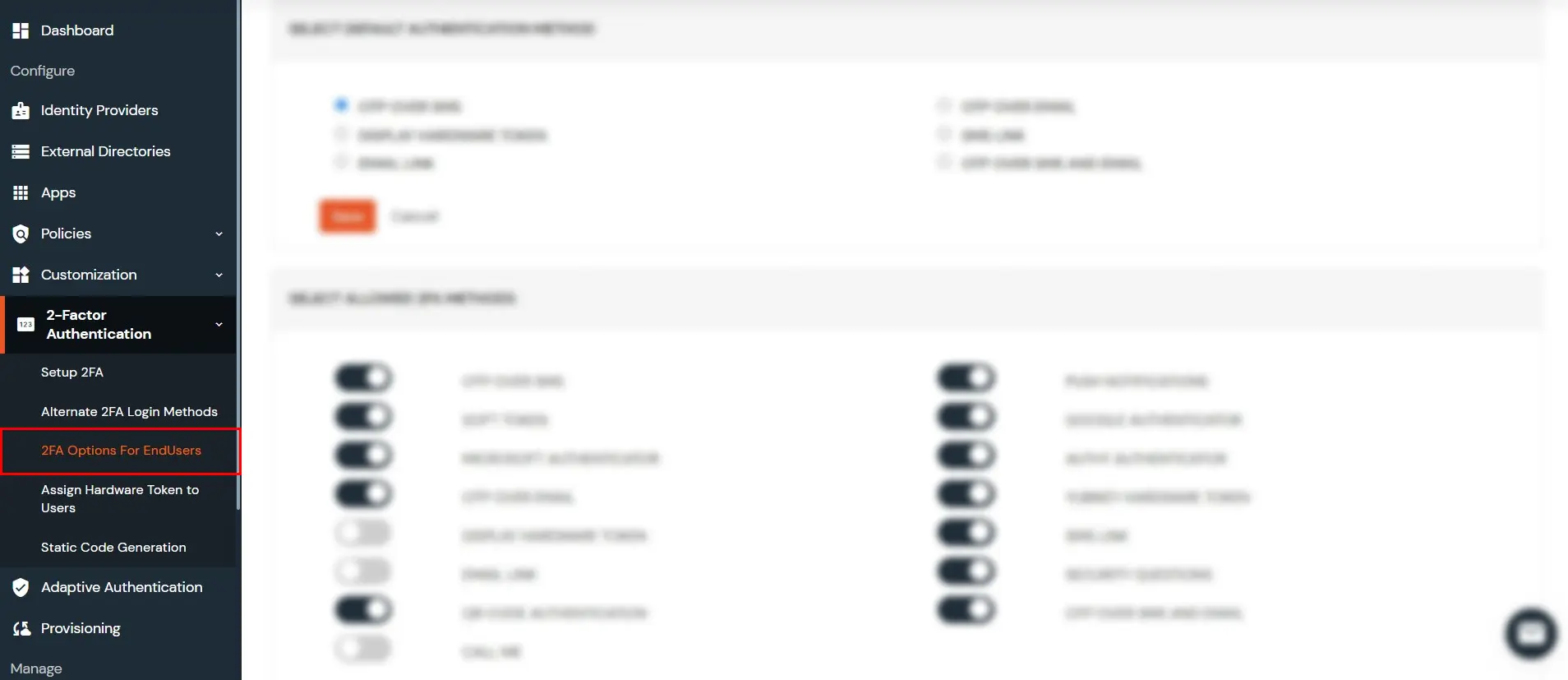
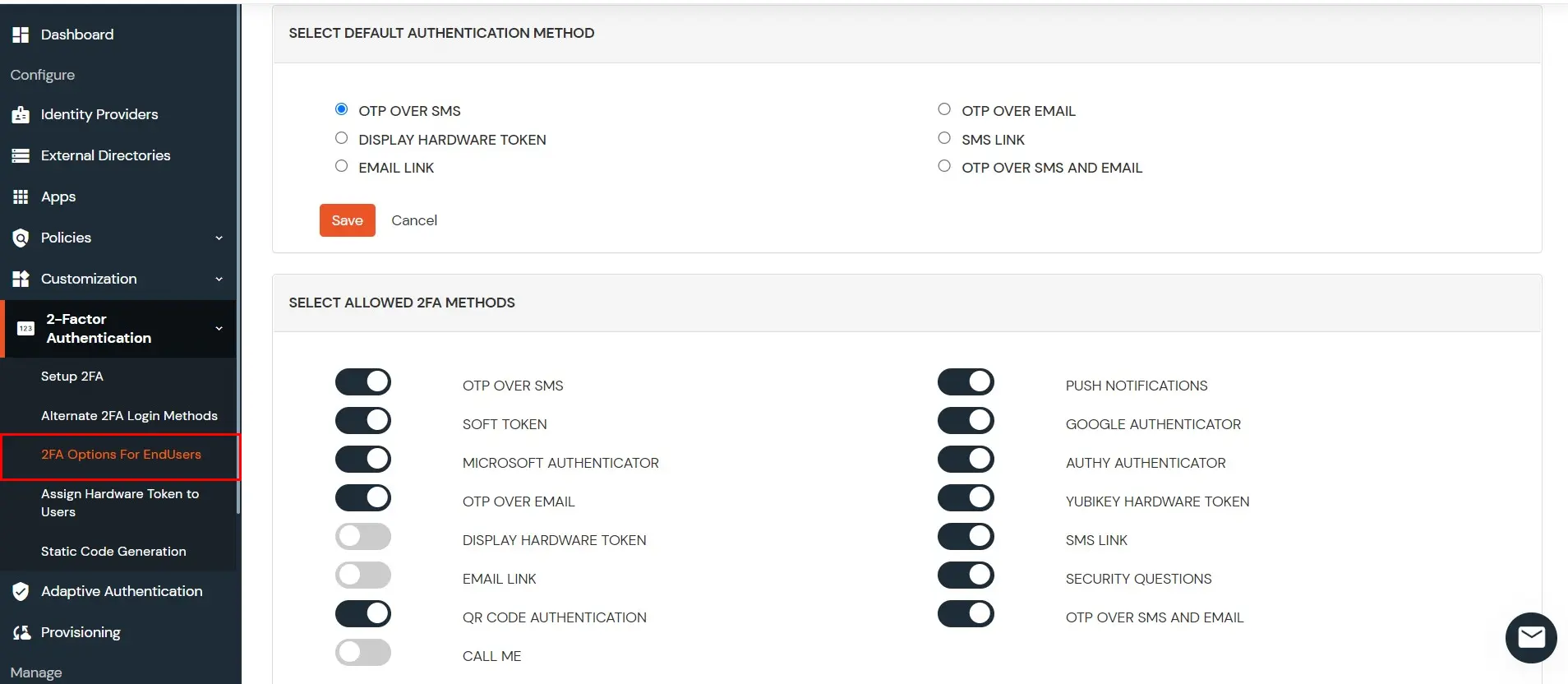
2.2 Choose which 2FA options the users can use
3. Setup miniOrange Two-Factor Authentication (2FA/MFA) Credential Provider for RDP Logon
- Open miniOrange 2FA Configuration in Start Menu
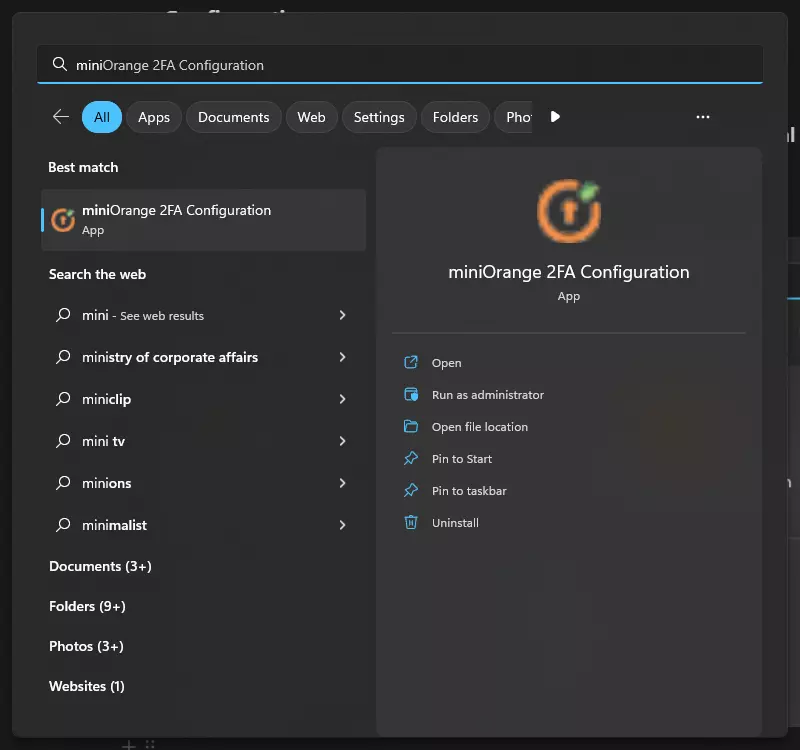
- Make sure "miniOrange service" status is running and in the "Credential Provider/GINA status" section the "Registered" and "Enabled" are "Yes". If any of these are not as intended, see this FAQ to fix it
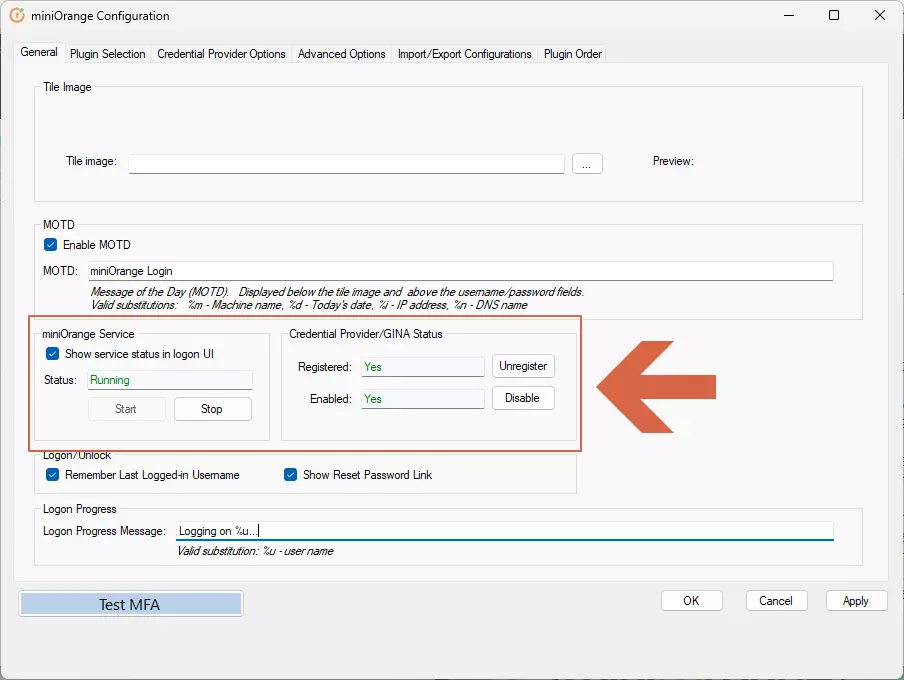
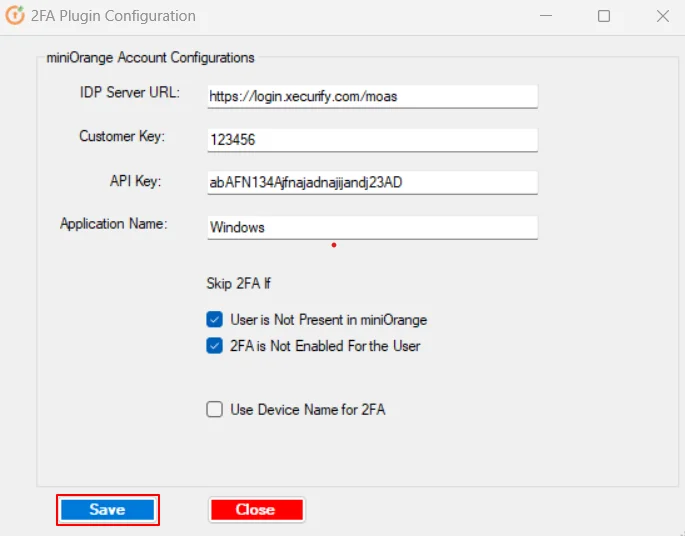
3a : Integrate the module to miniOrange account.
- Click on Plugin Selection, Double Click on miniOrange under plugin Name.
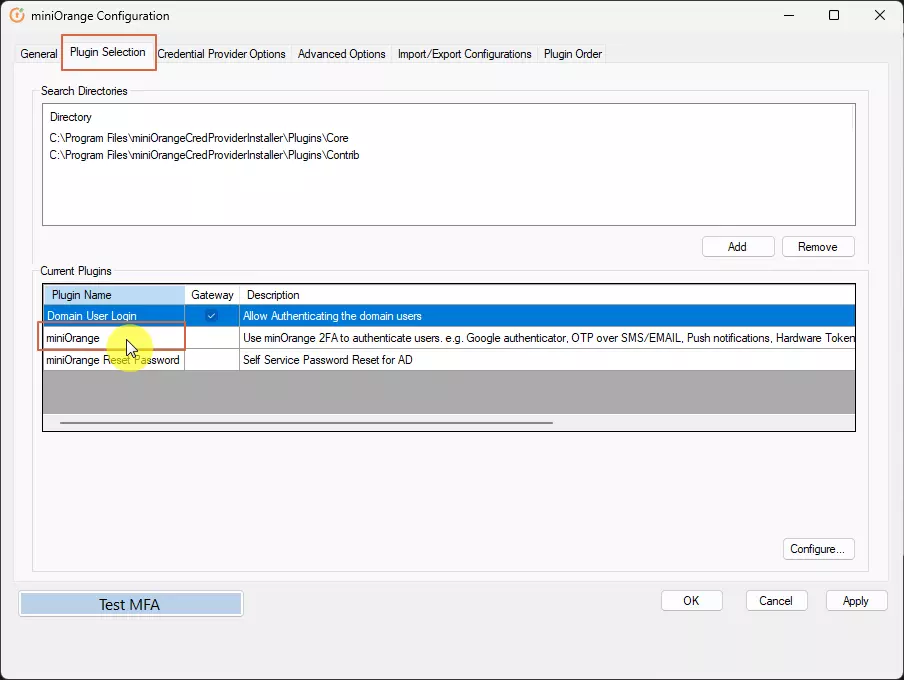
- A 2FA Configuration form will open up
Note:
If you’re using On-premise IDP application, please replace the IDP Server URL with base URL of your On-premise IDP application and make sure that URL is accessible from this machine. You can also use the IP of the server where the IDP application is hosted.
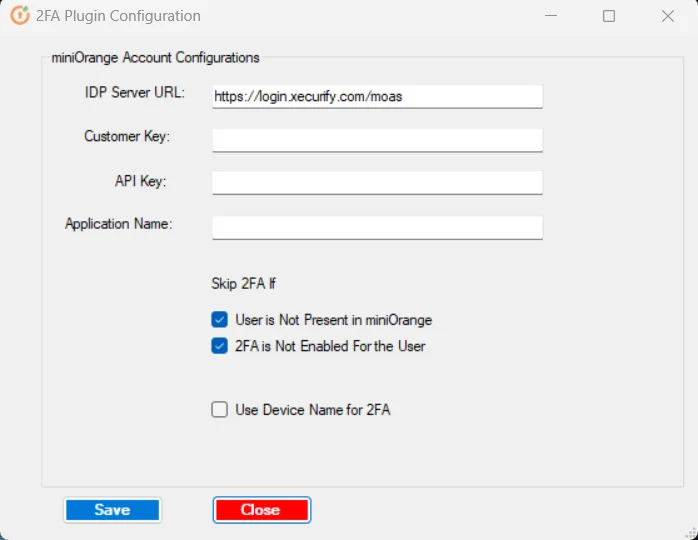
- To fill in these details, login to your miniOrange admin account on Cloud or On-premise.
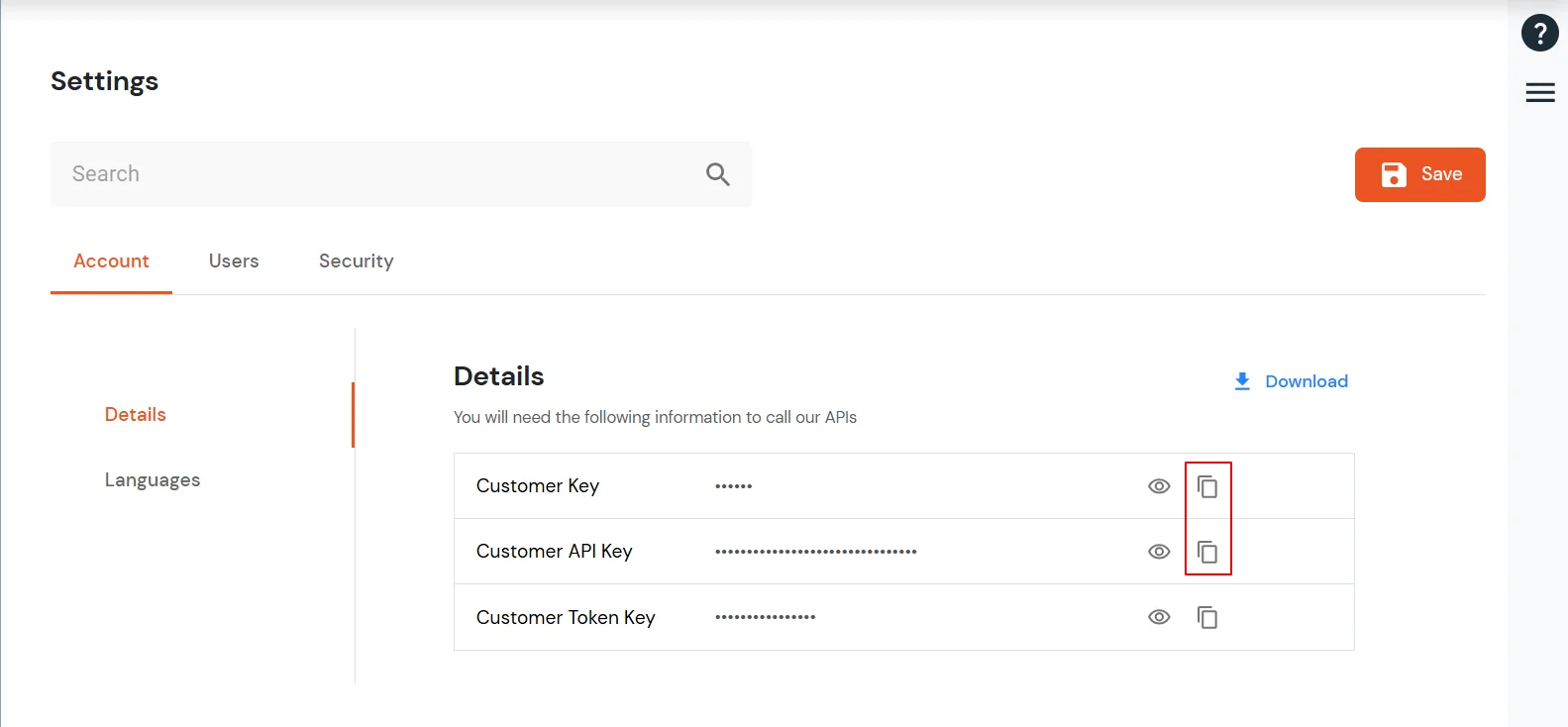
- Click on the Settings cog on top right corner.
- Copy the Customer Key and Customer API key.
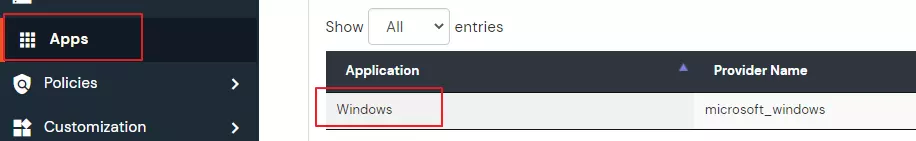
- Now, Go to Apps and copy the name of the Windows application created in step 2.
- Paste all these details in the form and click on Save. Leave the checkboxes as it is. More about them later.
3b. Configure Domain
Note:
Skip this step if you’re not configuring this on a domain joined machine
- In Plugin Selection tab, Double click on Domain User Login.
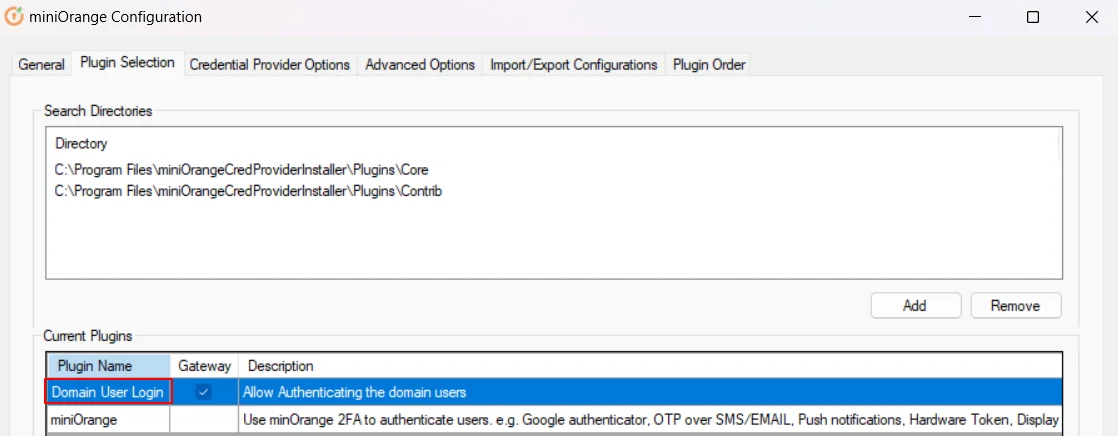
- Replace the domain name with your AD domain used before the username.
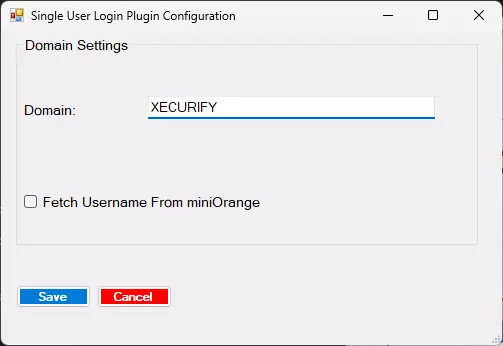
- To check your domain name, you can also use the command: SET USERDOMAIN
- Click on Save.
3c. Test MFA
Note:
Please make sure that at this point the user with same username as windows exists in miniOrange and has 2FA set up.
For instructions on setting up 2FA from Self Service Console, see this link .
- Click on Test MFA button
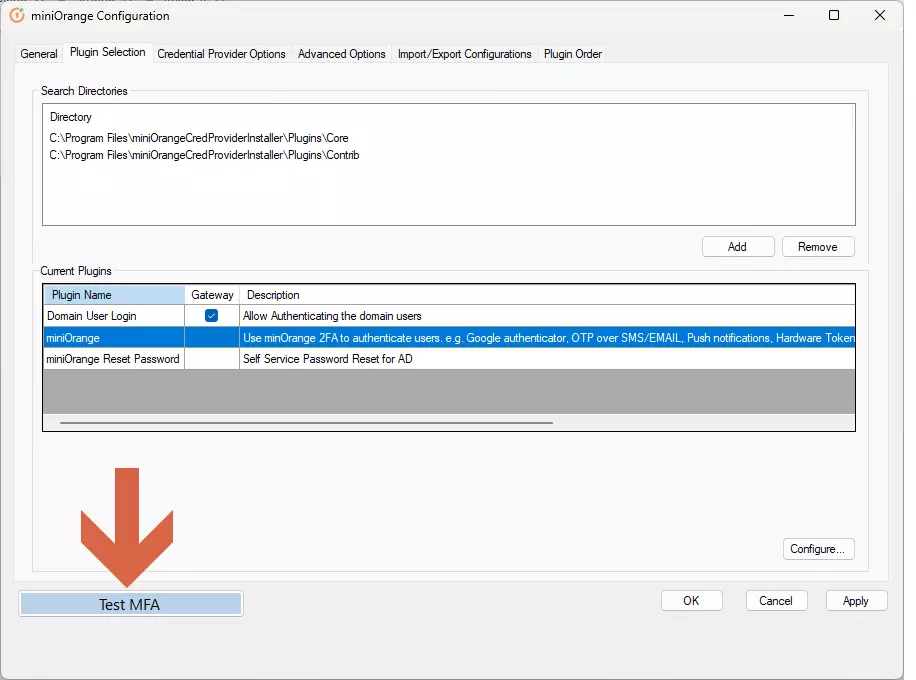
- Enter your machine username which is also present in miniOrange and click on Test MFA
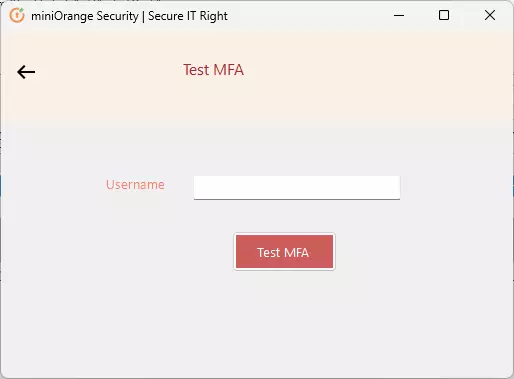
- You will be prompted to select one of the 2FA methods you’ve configured. Select one method and click on Next
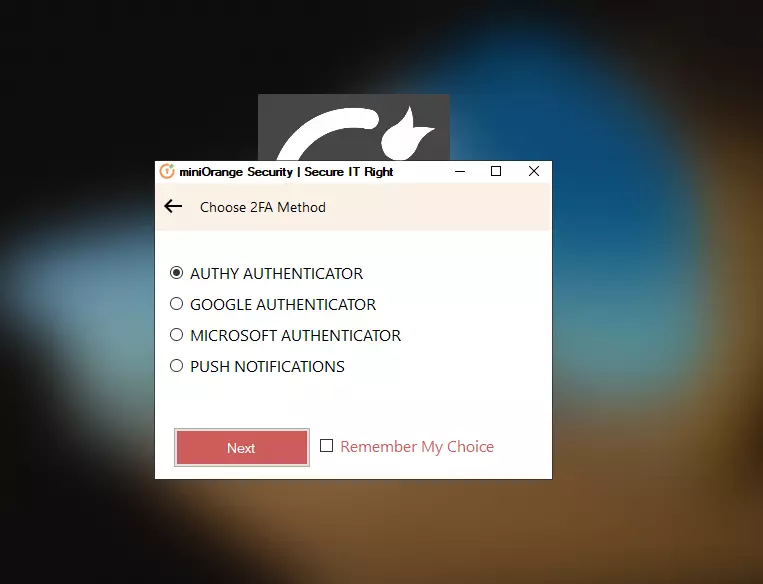
- Provide validation,
- If asked for OTP, enter OTP and click on Login.
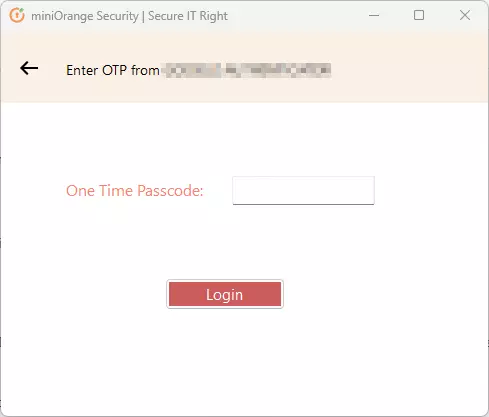
OR
- If asked for approval through Push notification, Accept the Push notification on your phone
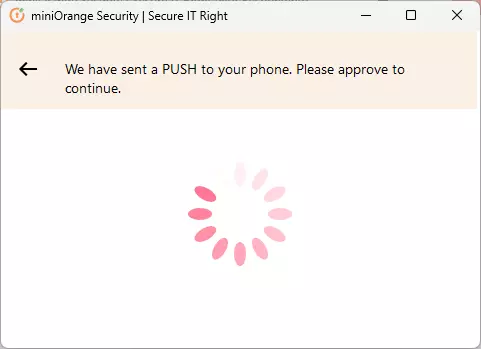
- After Successful Validation, you’ll see a Test Successful message
4. Use miniOrange MFA during login
- You should see the miniOrange login page after locking the computer or signing Enter your username and password.
Note: The logo and Message on login page can be customized from the General tab in miniOrange configuration
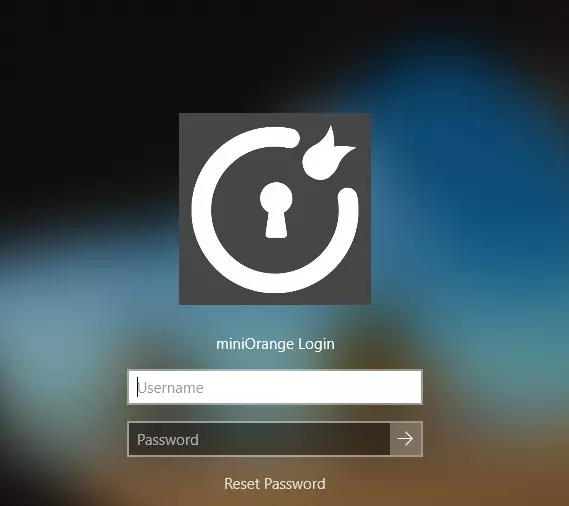
- If you’re using RDP, make an RDP connection using username and password
- You’ll see the 2FA prompt. Proceed with selecting a 2FA option and validating it.
- You will be logged into your account.
a. Disable other login methods (Optional):
- Go to Credential Provider Options tab.
- Check the box “Force miniOrange 2FA on Logon”
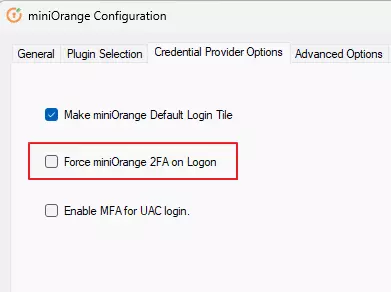
- Click on Apply.
5. Deployment using Group Policy
For Deployment and Configuration using Group Policy, please see our miniOrange 2FA for Windows Logon & RDP Group Policy Documentation.
Further References
miniOrange Credential Provider for Remote Desktop (RDP) and Windows Logon
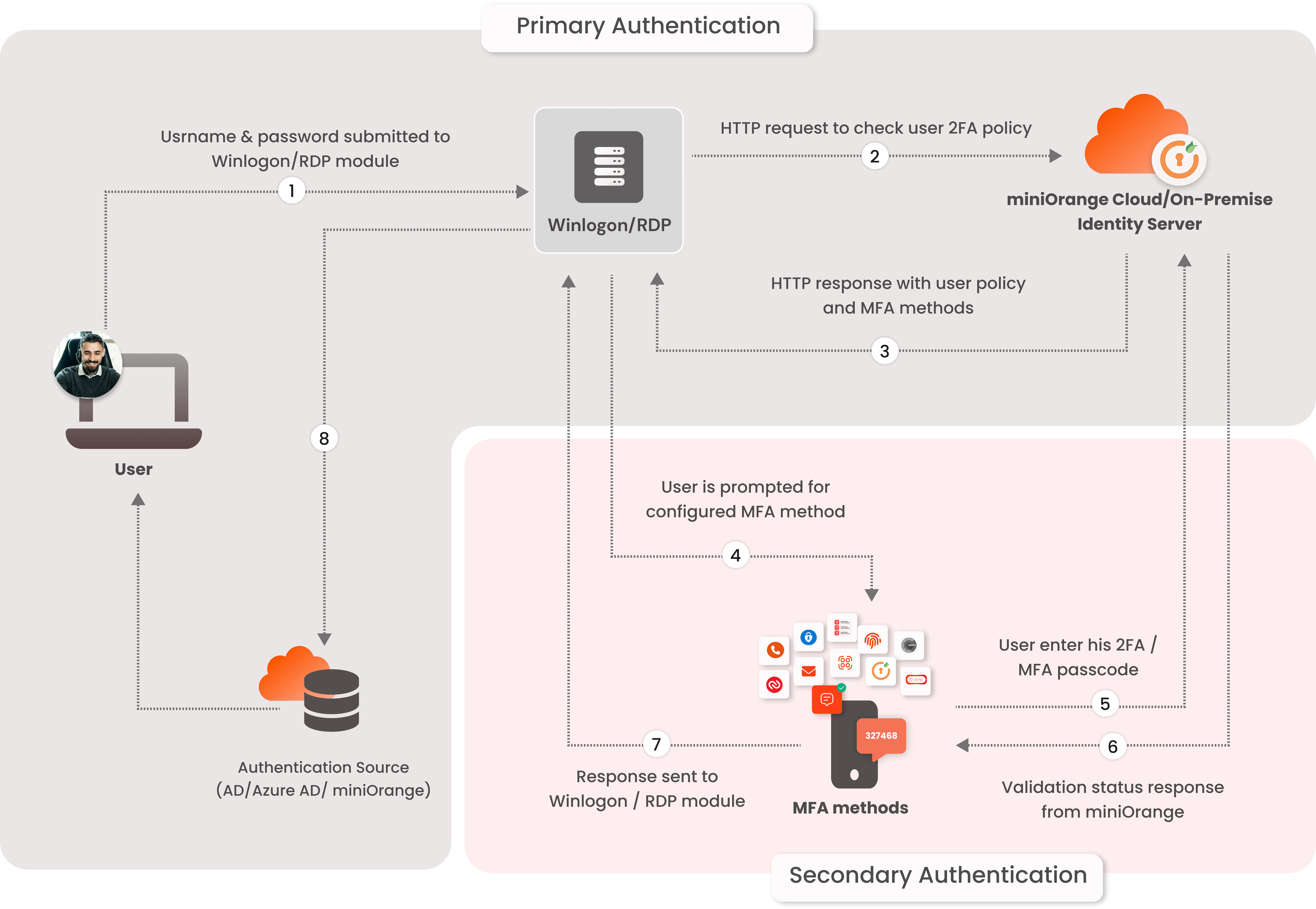
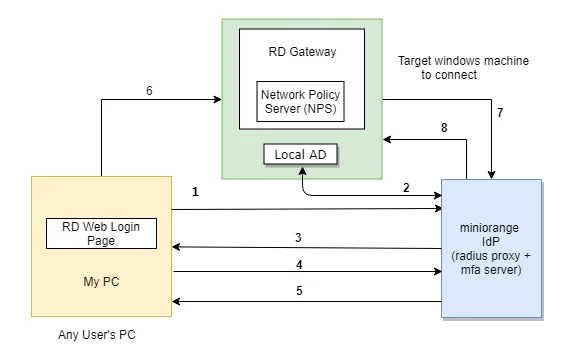
The user initiates the login to Windows or Remote Desktop Service either through a Remote Desktop Client or via the RD Web login page from his browser, after which the RADIUS request is sent from the miniOrange RD Web component installed on the target machine to the miniOrange RADIUS server, which authenticates the user via Local AD, and after successful authentication, two-factor authentication (2FA) of the user is invoked. After the user validates himself, he is granted access to the Remote Desktop Service (RDP).
A user can try to connect to RDS (Remote Desktop Protocol (RDP)) via 3 ways :
- RDC - Remote Desktop Client: If the RemoteApp is launched through a Remote Desktop client application, the users validate their two-factor authentication (2FA) while they enter the Username and Password to get access to the resources. (as this method doesn't support access-challenge response, only out of band authentication methods are supported ).
- RD Web Access - RD login page via browser: If the desktop or RemoteApp is launched through a RD Web Login page, the initial user authentication is done from the machine's AD, after which miniOrange challenges the user for two-factor authentication (2FA) via a RADIUS challenge request. After the users correctly authenticate themselves, they get connected to their resources.
- RD Gateway: If the organizations resources or server are protected by a Remote Desktop Gateway, you can setup 2FA/MFA on top of that as well. First level authentication will be done using the AD credentials and then miniOrange will prompt for the configured 2FA/MFA.
Check the guide to setup Remote desktop Gateway MFA (RD Gateway MFA/2FA)
Two-Factor Authentication (2FA/MFA) for RDS via RD Web
- In this case, the user goes to RD Web login page from his browser to connect to the Remote Desktop Service (RDS). He enters his Username and Password, and on submission, the RADIUS request from RD Web component installed on target machine is sent to the miniOrange RADIUS server which authenticates the user via local AD in the target machine.
- Once authenticated, it sends a RADIUS challenge to RD Web, and the RD Web shows OTP screen on browser now. Once the user enters the One Time Passcode, the miniOrange IdP verifies it and grants/denies access to the RDS.
- With this, after the user is connected to the Remote Desktop Service, the user can also gain access to published remote app icons on his browser screen, since the session has already been created for the user. Know more about Remote Desktop (RD) Web 2FA/MFA
Frequently Asked Questions (FAQs)
What is Windows RDP Two-Factor Authentication (2FA)?
Windows RDP Two-Factor Authentication (2FA) is a security measure that enhances the login process for Remote Desktop Protocol (RDP) connections by requiring two forms of identification. This ensures that users provide both their standard credentials and an additional verification code, significantly increasing the security of remote access to Windows systems.
Why is 2FA necessary for Windows RDP logins in my organization?
Implementing 2FA for Windows RDP logins is crucial because it adds an extra layer of security. Relying solely on a username and password can leave your system vulnerable to attacks. By using 2FA, you protect your remote access points against unauthorized access, ensuring that only verified users can connect to your Windows servers.
Which 2FA solutions are best for securing Windows RDP connections?
To secure Windows RDP connections, consider using solutions like miniOrange, which offers robust RDP two-factor authentication features. Their solutions include:
- Machine-based 2FA
- 2FA for Windows User Access Control (UAC)
- Offline 2FA
miniOrange provides comprehensive security for local and remote logins, enhancing the protection of your organization's network. You can explore our offerings through a free 30-Day trial or schedule a demo with our experts.
How does 2FA for Windows RDP work?
- Initial Login: Users enter their Active Directory (AD) domain credentials or use miniOrange to verify their identity.
- Second Factor: Users receive a time-sensitive authentication code via SMS, email, or a third-party authentication provider. They must enter this code to proceed.
- Access Granted: After successfully entering the code, users are logged in to their Windows machines.
This process ensures that even if a user's primary credentials are compromised, unauthorized access to the RDP session is prevented by the second authentication factor.
External References