Need Help? We are right here!
Search Results:
×
Watch the video below to learn more about using Google Cloud Identity Access to restrict permissions to Google Workspace app files over your office networks and enable Google workspace security.
Secure Google Drive with IP whitelisting for top notch workspace security and data protection. You can set security standards for your Google Drive files and folders.
Prevent all unauthorized users from hijacking your Google Meet App sessions (similar to Zoom Bombings) with advanced security for Google meet video conferencing and calendar invites.
Prevent unauthorized users' access to your Docs, Sheets, and Slides by enabling file protection with the best Google workspace security and cloud identity data protection.
Set custom user roles and permissions to set access control policies for different Google Workspace apps for smoother user handling. You can also configure your Google workspace admin console for advanced security.
Monitor the traffic and each user’s activity to mitigate any threat attempts directed towards your company sensitive information stored in your Google workspace Cloud apps.
Whitelist specific IPs, or an entire range of IPs for Google Drive, Gmail Workspace security, and for other Google Cloud app protection.
Set individual Google Cloud and workspace security for various Google services for flexibility and covering security gaps.
Set User Restrictions based on the time, country, devices in use, and IP ranges working at runtime, so the security restrictions kick in dynamically as the authorization conditions changes for any user.
Easily add further security integrations like SSO, MFA, and advanced Adaptive Authentication methods for your Google account’s advanced security.

All Google Cloud app services can be secured for advanced security from each user group in an organization for all user scenarios.
You can monitor the traffic and user activity for each Google Cloud service they interact with and keep logs and prevent data breaches.
Easy configuration for user roles and permissions using our highly customizable role-based access control Google Cloud solution.
Block users not on your company network by blacklisting those IPs from accessing Google Cloud security for data protection.
Google Cloud workspace proxy has you covered from any data breaches, so you don’t need to look for any other 3rd party service on the market for Google data protection.
Easily integrate Google workspace security features and updates for a seamless experience and stay protected against the latest threats and data breaches enterprises are facing.
Set custom rules for each user group before they can even access any of the Google Cloud workspace apps.
Simple User Authentication for each Google Cloud workspace app (like Google Drive) to provide advanced data security and threat protection.
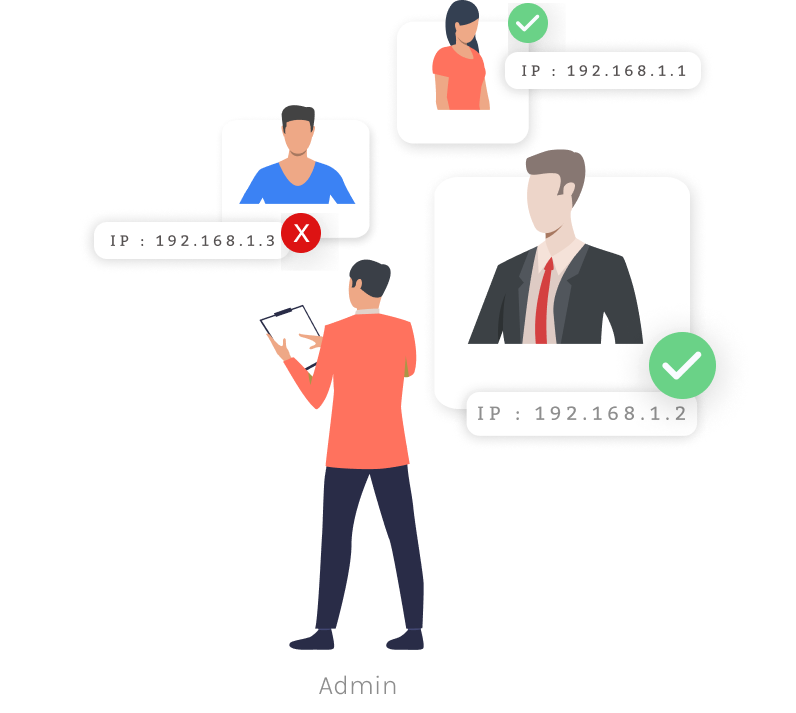
Rick is an admin user who has set up IP restrictions for accessing different Google Cloud apps and assigned permissions for each individual user. Joe is a user who has a defined group role in the organization, and he will be granted access accordingly.
Step
1
Joe tries to access Google Drive, the request will go to the reverse proxy first.
Step
2
Joe's access to Google Drive is checked by the reverse proxy in the rules set.
Step
3
If Joe’s access request passes all the conditions, then he can securely access Google Drive.
Step
4
Else, if Joe does not satisfy all the conditions then he will be denied access to Google Drive.
Google context-aware access provides well-defined access policies that determine whether users can retrieve Google Cloud workspace apps like Google Drive, Docs, Sheets, Slides, PDFs, Gmail, Google Meet, and many more, holding company secret data. Furthermore, you can set custom rules by creating a combination of security policies, such as authorized IPs, authorized locations, authorized devices, and time-based restrictions, before anyone can fetch your sensitive files stored on workspace.
Whether you need Google Cloud security for education or Google workspace security for business needs, miniOrange has you covered with the best enterprise level support at the most pocket-friendly price. Contact us at proxysupport@xecurify.com for any queries, sales, and support.
Choose User Tier
|
Basic
$3
The price is for (1-200) user tiers |
Premium
$5
The price is for (1-200) user tiers |
|
|---|---|---|

|

|
|

|

|
|

|

|
|

|

|
|
|
SSO Authentication with ANY SAML provider |

|

|
|

|
|

|

|
|

|

|
|
|
(Email + Video call + 12x5 Support) |
(Email + Video call + 24x7 Support) |
A reverse proxy server is a special kind of proxy server. In contrast to a forward proxy server, which protects clients [...]
Role based access control (RBAC) means allowing access to users to a stack based on the set user roles and [...]
Ever felt concerned about the images that you added to your online folders, might be downloaded by users (who aren’t logged in) [...]
Google Workspace holds the entire collection of data that a company generates by storing [...]