What is Rate Limiting?
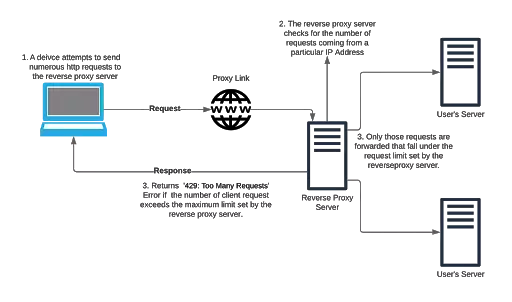
Rate limiting feature is quintessentially used to prevent the server from getting DoS attack, DDoS attack or Slowloris attack. It limits the number of requests a particular IP address can send in a specified amount of time. The reverse proxy server that sits right in front of the user’s server(s) receives all the requests. When in use, it doesn’t let any IP address make requests more than the permitted number.
How Rate Limiting Works?
Let us consider a scenario where a specific IP address keeps sending requests to one of the servers of a user masked by the reverse proxy server:
- The requests are received by the reverse proxy server.
- The reverse proxy server keeps a tab of the IP address and the number of requests it makes in unit time.
- If this number exceeds the permitted number of requests set for the proxy server, then the client making those requests is responded with a 429: Too Many Requests Error.
Use-Case Scenario: Reverse Proxy Server under DDoS attack
- Let’s take the example of one of our customers who configured a reverse proxy server onto his machine using our product. The client configured the feature of rate limiting by setting the number of requests permitted in a specified amount of time.
- Suppose the client receives lots of requests from an IP address to the proxy links he configured. The reverse proxy server intercepts those requests, and keeps a track of the count of the requests made by that IP address. If the count exceeds the request limit in a given amount of time, the server throws 429: Too Many Requests error.