Oracle BI Enterprise Single Sign-On (SSO)
Oracle Business Intelligence (BI) Enterprise Edition is Oracle Corporation's set of business intelligence tools. It enables customers to uncover new insights and make informed business decisions by offering agile visual analytics and self-service discovery.
miniOrange SSO connector enables the Single Sign-On (SSO) integration between any Oracle application and IdPs (Identity Providers) like miniOrange, ADFS, Active Directory, Azure AD, Google, Okta, Onelogin, Ping Idenity, Centrify and many more. It also provide SSO support for web applications which do not provide support for federated Single Sign-On (SSO) protocol such as SAML or OAuth 2.0. SSO connector gives you the flexibility of extending your existing SSO integration to Oracle BI Enterprise as well. This is possible due to its capability to act as a broker between multiple IdP's & your configured applications. This states that you can perform seamless SSO integration for Oracle BI Enterprise with your existing authentication platform.
"miniOrange SSO connector enables Single Sign-On (SSO) between Oracle BI and any IdPs without the need to purchase and install Oracle Access Manager (OAM) and Oracle Internet Directory (OID) license."
This short tutorial walks you through starting up the sso connector in standalone mode, setting up the initial admin account, and logging into the miniOrange admin dashboard.
Authentication Flow for miniOrange Oracle BI SSO Solution:

Connect with External Source of Users
miniOrange provides user authentication from various external sources, which can be Directories (like ADFS, Microsoft Active Directory, OpenLDAP, AWS etc), Identity Providers (like Microsoft Entra ID, Okta, AWS), and many more. You can configure your existing directory/user store or add users in miniOrange.
Get Free Installation Help - Book a Slot
You can request a trial version of the connector and miniOrange offers 1 hour free help through a consultation call with our System Engineers to Install or Setup Oracle BI Enterprise SSO solution in your environment with 30 days trial.
For this, you need to just send us an email at idpsupport@xecurify.com to book a slot and we'll help you setting it up in no time.
Follow the Step-by-Step Guide given below for Oracle BI Enterprise Single Sign-On (SSO)
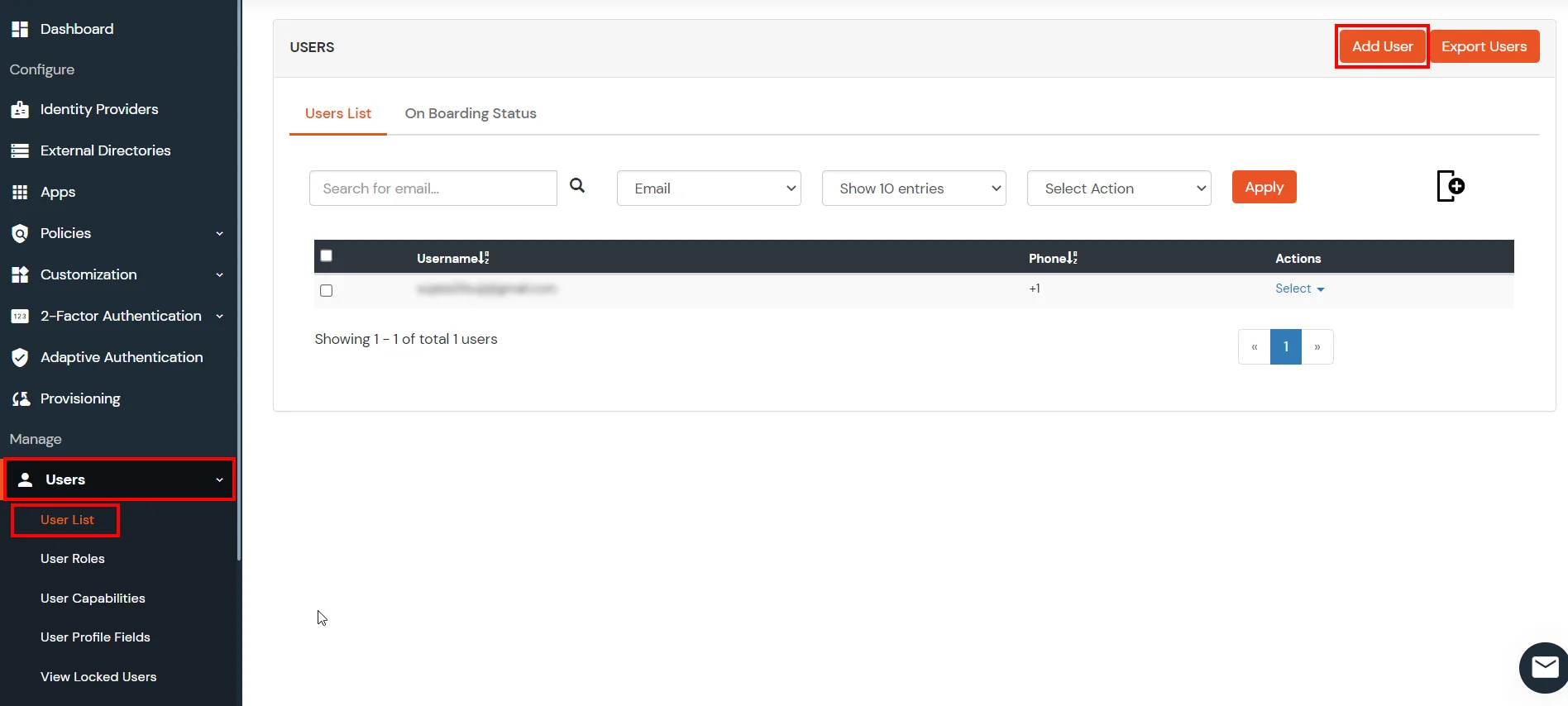
1. Download and Install miniOrange SSO Connector
Prerequisites:
Java 8 (JDK 1.8): When you install JAVA 8, only JRE 1.8 would be present.
Note
Tomcat is already included in this distribution (zip file), you don’t have to install it separately.
Installation of JDK 1.8 requires login through the oracle account. If you don't have the oracle account, you can directly install JDK 1.8 from here.
If JAVA is already installed and Environment Variables are set correctly on your system, then you don't need to follow this step, you can directly go to step 1.2.
Note
Once the Java installation is complete, check that the JAVA_HOME environment variable has been set correctly.Open a command prompt and type echo %JAVA_HOME% and hit Enter. If you see a path to your Java installation directory, the JAVA_Home environment variable has been set correctly.If nothing is displayed, or only %JAVA_HOME% is returned, you'll need to set the JAVA_HOME environment variable manually.
Set Java environment variables i.e. JAVA_HOME and JRE_HOME and path variables. Lets say JDK software is installed on your computer, for example, at C:\Program Files\Java\jdk1.8.0_221 then JAVA_HOME and JRE_HOME paths can be as mentioned -
- JAVA_HOME - C:\Program Files\Java\jdk1.8.0_221
- JRE_HOME - C:\Program Files\Java\jdk1.8.0_221\jre
- To Save these variables, right click My Computer and select Properties > Advanced System Settings.Click the Environment Variables button.Under System Variables, click New.In the Variable Name field, enter:
- JAVA_HOME - C:\Program Files\Java\jdk1.8.0_221
- JRE_HOME - C:\Program Files\Java\jdk1.8.0_221\jre
- Also update the path variable set with path : path_to_JAVA_HOME/bin. You can Read more about java specific environment variables.
To install miniOrange SSO Connector:
- To start the miniOrange miniOrange SSO Connector, go to the bin/ directory of the miniOrange SSO Connector distribution (i.e. folder with name similar to miniorange-sso-connector-kit (version may vary)). Execute the startup file based on your environment.
> ...\bin\startup.bat
Prerequisites:
Java 8 (JDK 1.8): When you install JAVA 8, only JRE 1.8 would be present.
Note
Tomcat is already included in this distribution (zip file), you don’t have to install it separately.
- You can download OpenJDK8 package using
apt install openjdk-8-jdk for Debian, Ubuntu, etc. OR yum install java-1.8.0-openjdk for Fedora, Oracle Linux, Red Hat Enterprise Linux, etc.
- Linux users can use below commands to set JAVA_HOME and JRE_HOME variables using below commands -
export JAVA_HOME=/path/to/jdkexport JRE_HOME=/path/to/jre
- You can verify whether above environment variables are set correctly. Execute below commands to verify environment variables -
echo $JAVA_HOMEecho $JRE_HOME
To install miniOrange SSO Connector:
- To start the miniOrange miniOrange SSO Connector, go to the bin/ directory of the miniOrange SSO Connector distribution (i.e. folder with name similar to miniorange-sso-connector-kit (version may vary)). Execute the startup file based on your environment.
- Linux/Unix – Execute chmod +x startup.sh to give executable permission to this file. Set relevant permission of miniorange-sso-connector folder to allow the creation of new folder like temp or logs folder – chmod 755.
$ .../bin/startup.sh
1.1. Setup Database
- After tomcat startup, open http://localhost:8080 in browser. You will see a page to choose a database configuration for the miniOrange SSO Connector. You can choose where you would like to store its data.
- Oracle miniOrange SSO Connector gives you the flexibility to choose your database type. We support Embedded H2 Database which is a light weight database good for testing purposes. Later you can migrate to your production database type that is supported in the external database section. In External Database section, we support Postgresql (ideally 9.6), MySql and Oracle Databases.
Note
Before you proceed with Embedded H2 database, make sure your system has given write permission to the miniOrange SSO Connector folder i.e. miniorange-sso-connector-kit folder. If not then first assign the write permission to the miniOrange SSO Connector folder to avoid getting stuck in permission issues. Write permission is required because Embedded H2 database is created in miniOrange SSO Connector folder with the folder named data.
- Select embedded Database and click on proceed.
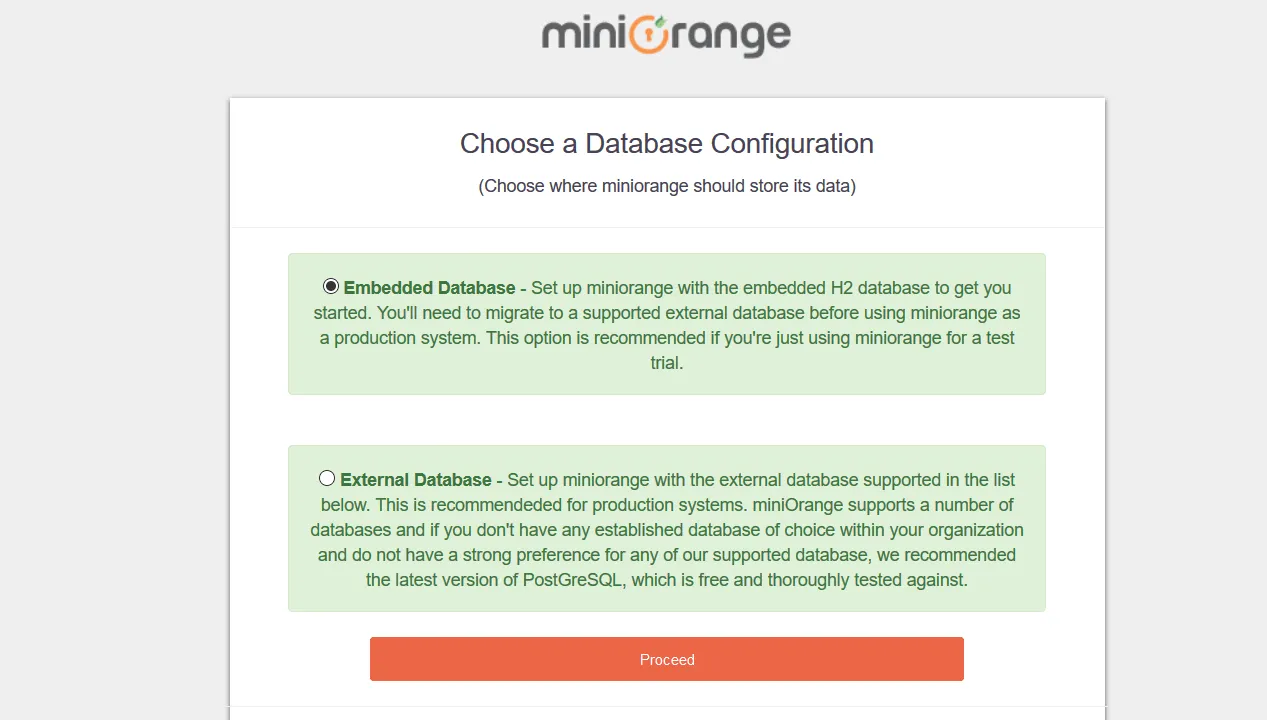
- Set up miniOrange with the embedded H2 database to get you started. You’ll need to migrate to a supported external database before using miniOrange as a production system. This option is recommended if you’re just using miniOrange for a test trial. The database folder is created inside the miniorange-sso-connector folder named data.
Note
In case if you are stuck in permission issues, you can run commands specific to your OS to proceed or you can follow the instructions given on pop-up.
| Windows |
icacls “path upto miniorange-sso-connector-kit ” /remove:d Users /grant:r Users:(OI)(CI)F /T |
| Linux |
chmod -R 775 “path upto miniorange-sso-connector-kit” |
- If you don't have enough privileges to run above commands, in that case either you can follow instructions from pop-up or can contact us.
- Once database is created successfully, you will be redirected to the admin set up page where you will configure admin account for Identity Provider.
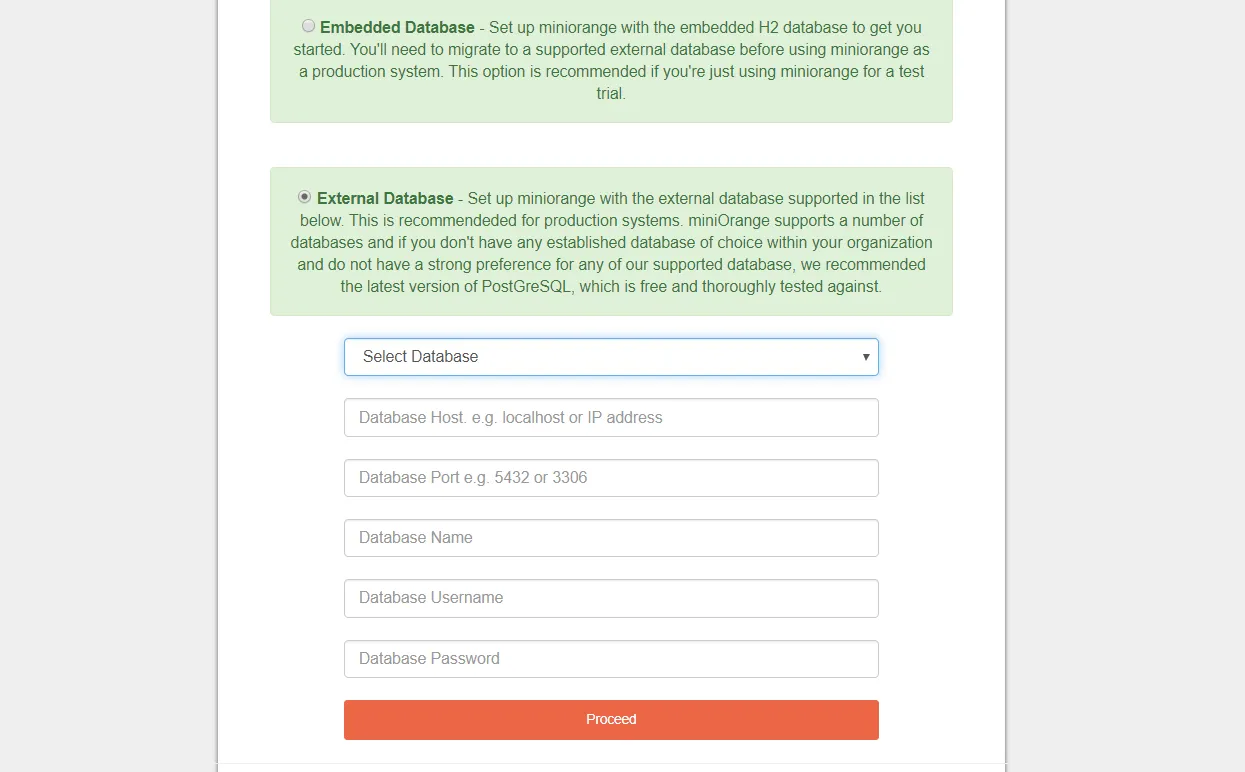
- Set up miniOrange with the external database supported in the list below. This is recommended for production systems. miniOrange supports a number of databases and if you don’t have an established database of choice within your organization and do not have a strong preference for any of our supported databases, we recommend the PostgreSQL, which is free and thoroughly tested against.
- You can refer to the below document to see supported versions of MySQL, MS SQL and PostgreSQL – click here. Note: If you already have a database setup which is not in the list below. You can contact us to add support for that database.
- Create an empty database in your database server – PostgreSQL/MySQL/MS SQL. Once done, start filling the form shown below –
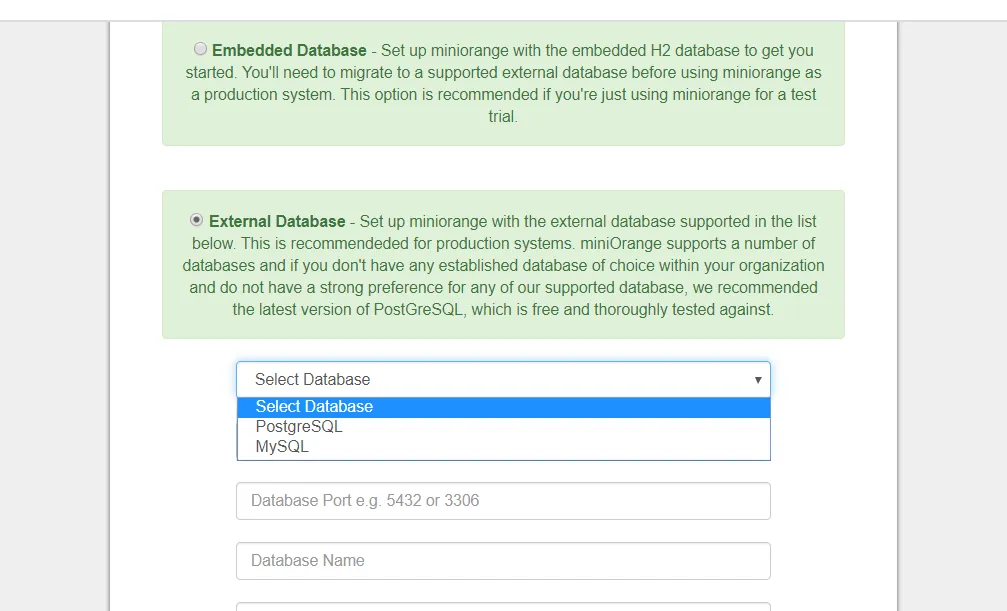
- Enter Database Host – localhost or IP address.
- Enter Database Port :
PostGres – 5432
MySQL – 3306
- Enter the Database Name created in your database server.
- Enter username and password of your database server for the connection.
- Once database is created successfully, you will be redirected to the admin set up page where you will
configure admin account for Identity Provider.
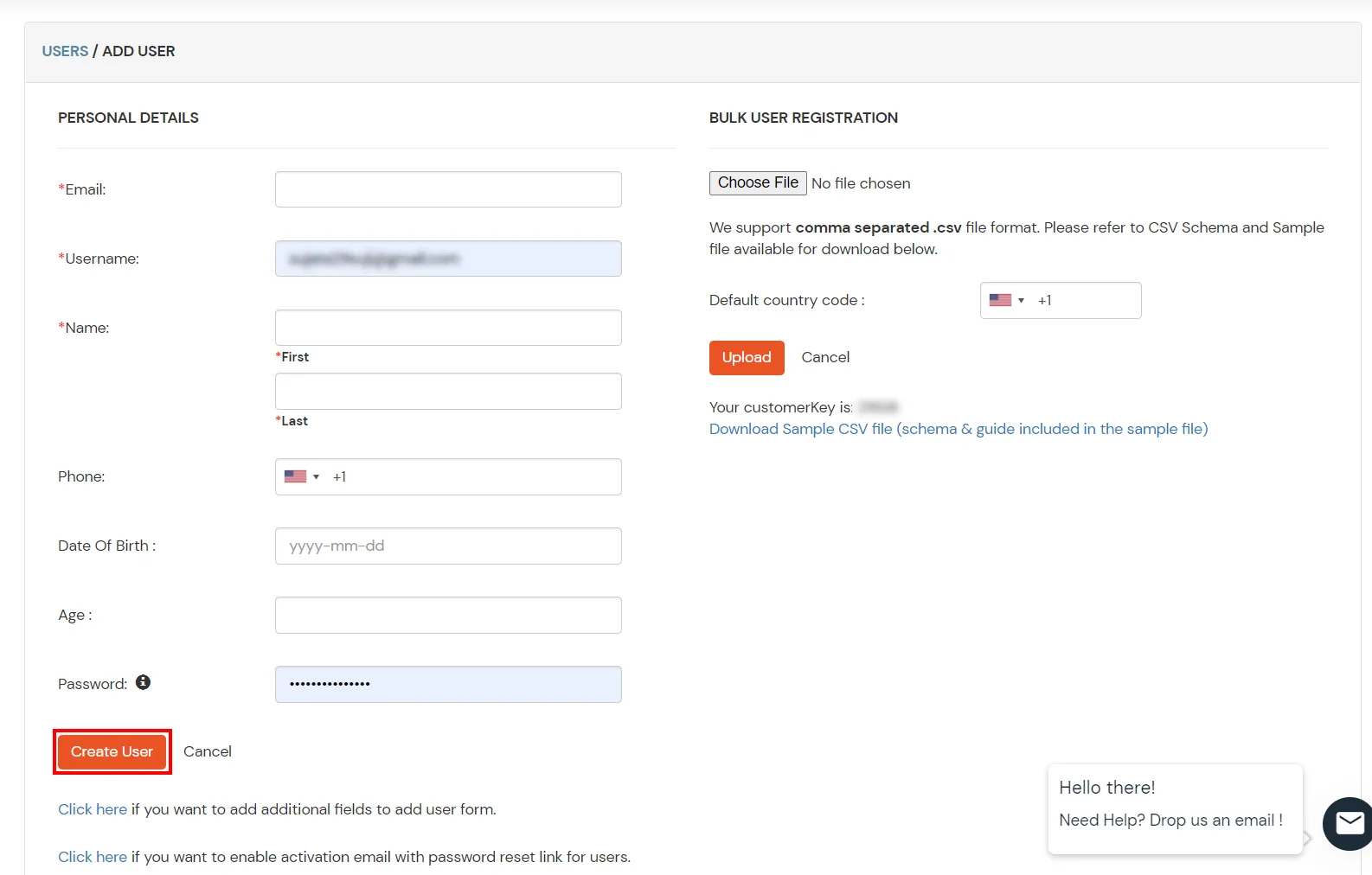
1.2. Setup Admin Account
- Setup your Admin Account. Enter a Username and Password for your admin account.
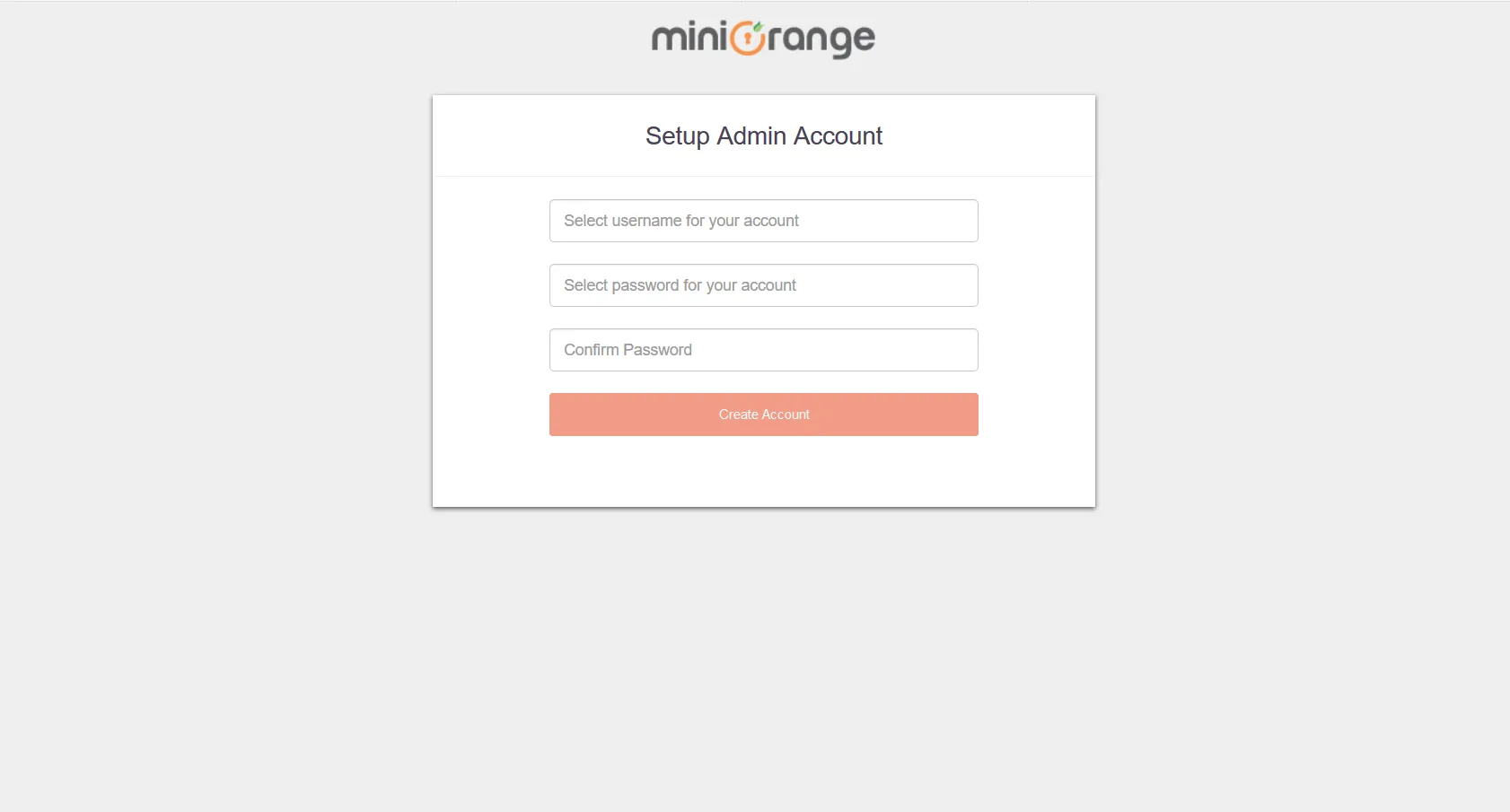
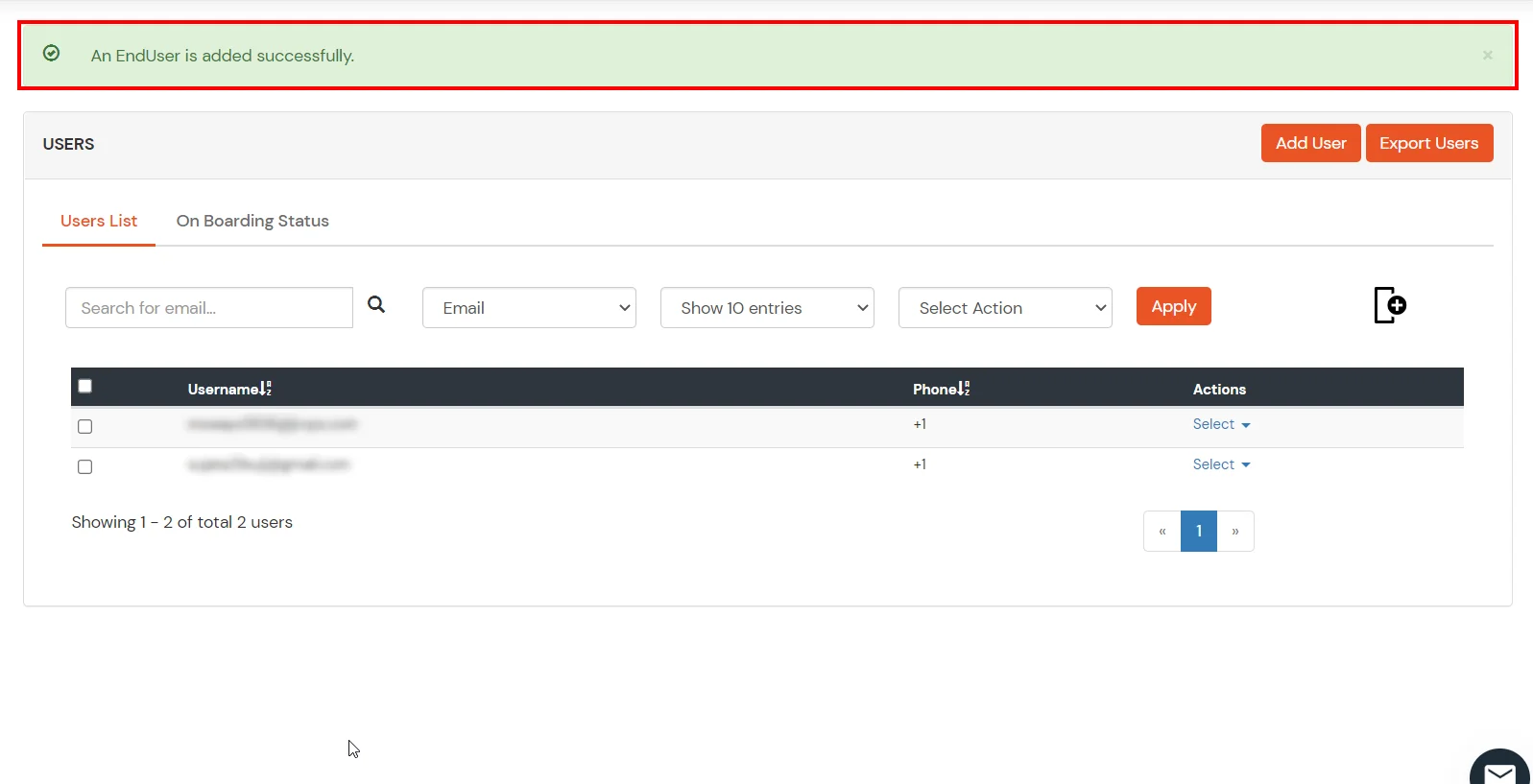
- Once your admin account is created, you will be auto logged in to the dashboard screen.
2. Configure Oracle BI with miniOrange SSO Connector
- Set up Oracle BI according to the prerequisites in the Security Guide according to your version of BI. You can access the Security Guide on this link.
3. Test SSO Configuration
- Access your Oracle BI instance on the proxy URL. You should be redirected to your configured Identity Source for authentication.

- After successful authentication, you should be redirected to your Oracle BI homepage
4. Configure Your User Directory (Optional)
miniOrange provides user authentication from various external sources, which can be Directories (like ADFS, Microsoft Active Directory, Azure AD, OpenLDAP, Google, AWS Cognito etc), Identity Providers (like Okta, Shibboleth, Ping, OneLogin, KeyCloak), Databases (like MySQL, Maria DB, PostgreSQL) and many more. You can configure your existing directory/user store or add users in miniOrange.
- Click on Identity Providers >> Add Identity Provider in the left menu of the dashboard.
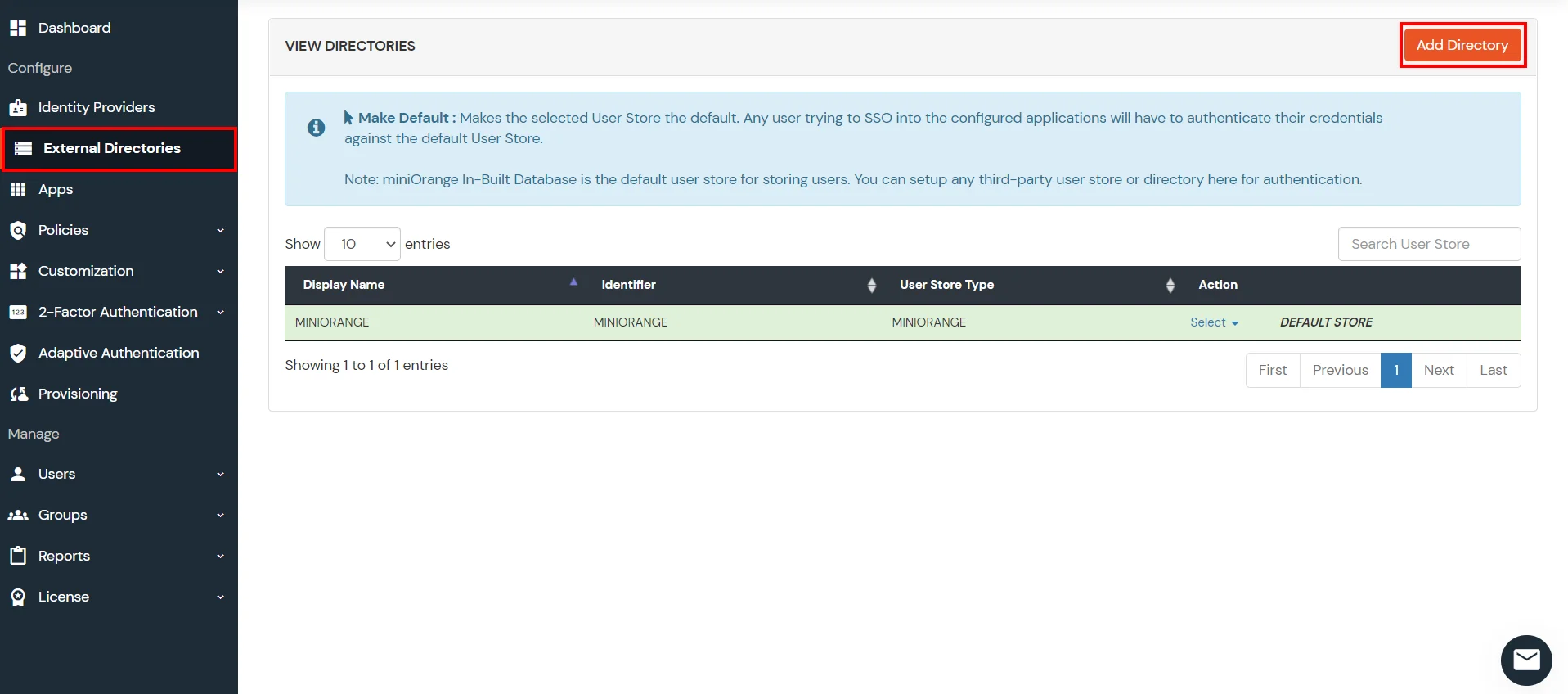
- In Choose Identity Provider, select AD/LDAP Directories from the dropdown.
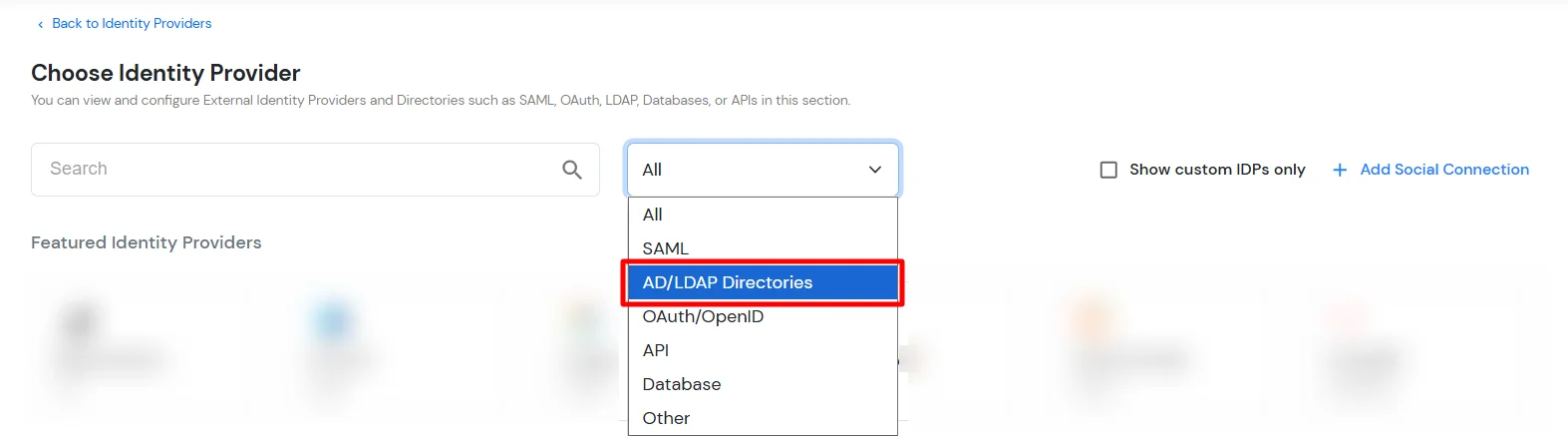
- Then search for AD/LDAP and click it.
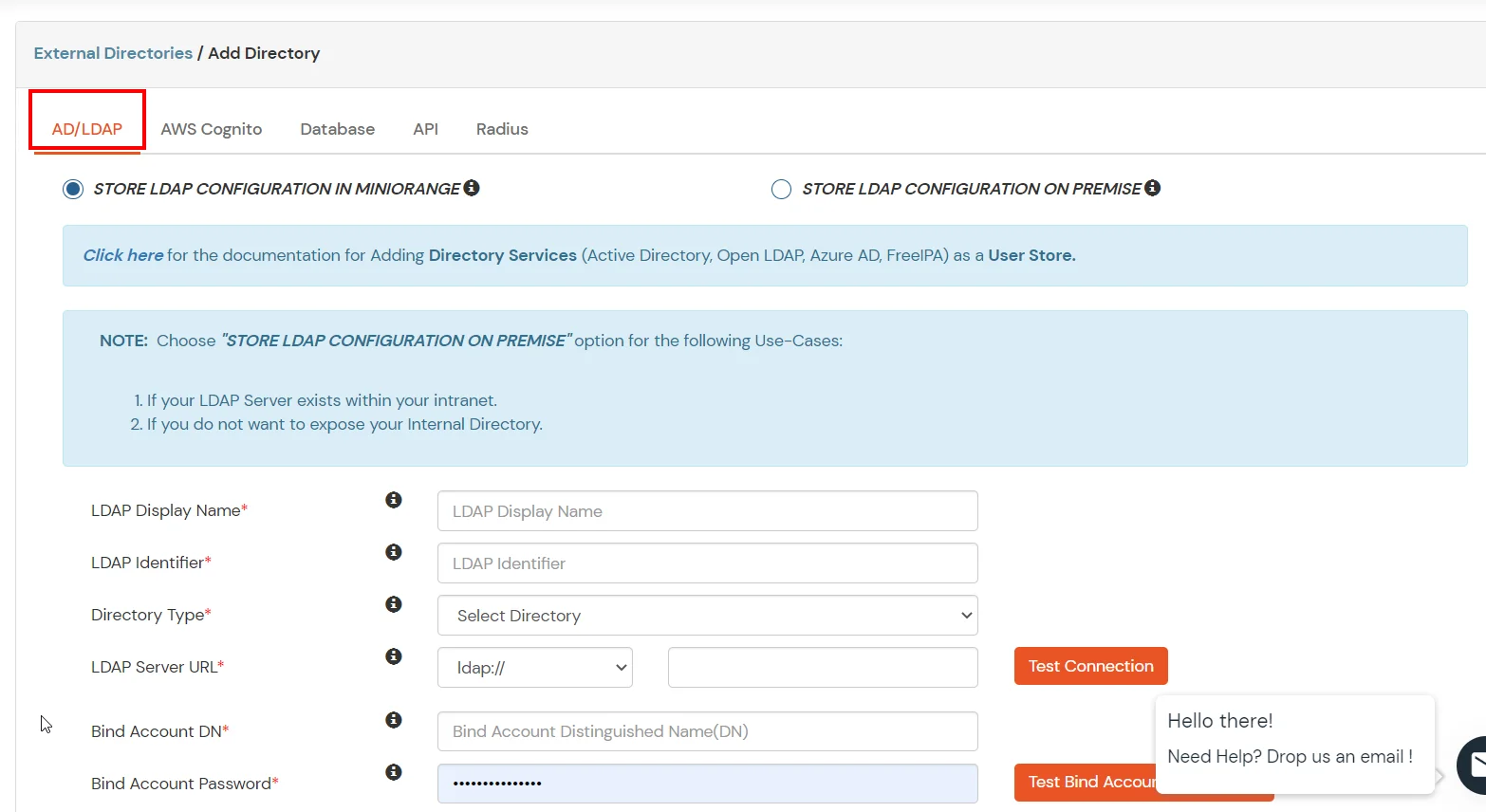
- STORE LDAP CONFIGURATION IN MINIORANGE: Choose this option if you want to keep your configuration in miniOrange. If the active directory is behind a firewall, you will need to open the firewall to allow incoming requests to your AD.
- STORE LDAP CONFIGURATION ON PREMISE: Choose this option if you want to keep your configuration in your premise and only allow access to AD inside premises. You will have to download and install miniOrange gateway on your premise.
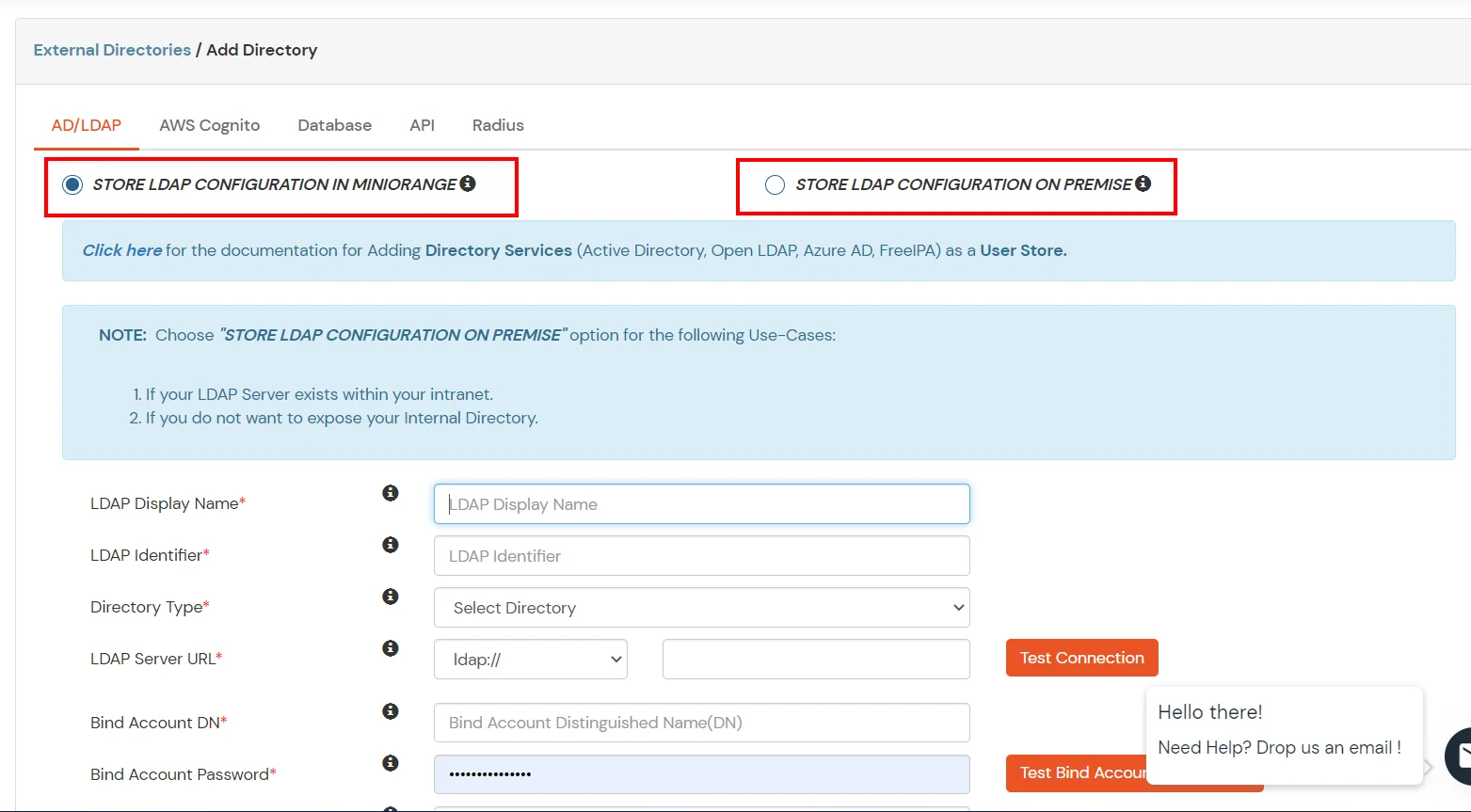
- Enter LDAP Display Name and LDAP Identifier name.
- Select Directory Type as Active Directory.
- Enter the LDAP Server URL or IP Address against the LDAP Server URL field.
- Click on the Test Connection button to verify if you have made a successful connection with your LDAP server.
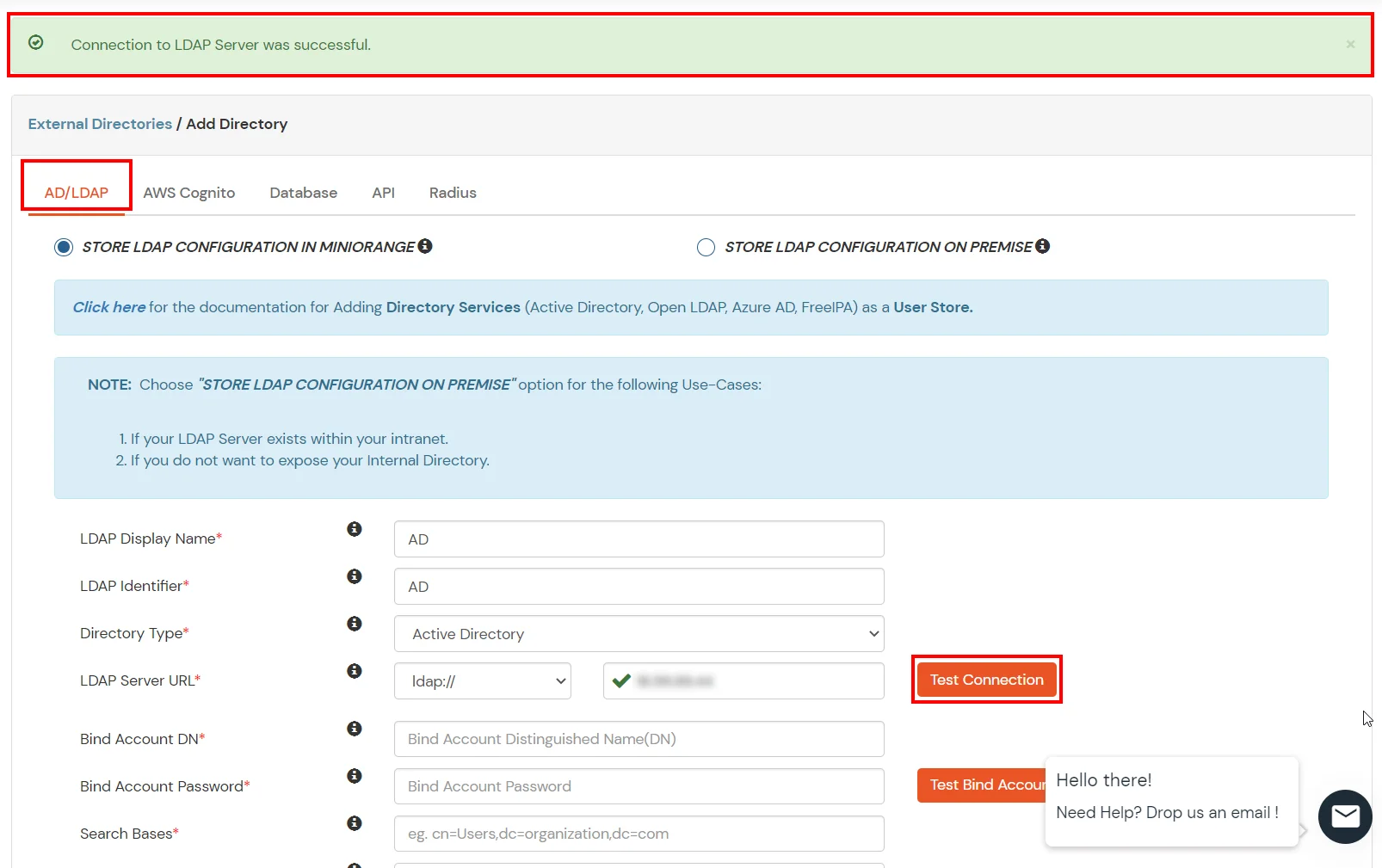
- In Active Directory, go to the properties of user containers/OU's and search for the Distinguished Name attribute. The bind account should have minimum required read privileges in Active Directory to allow directory lookups. If the use case involves provisioning (such as creating, updating, or deleting users or groups), the account must also be granted appropriate write permissions.
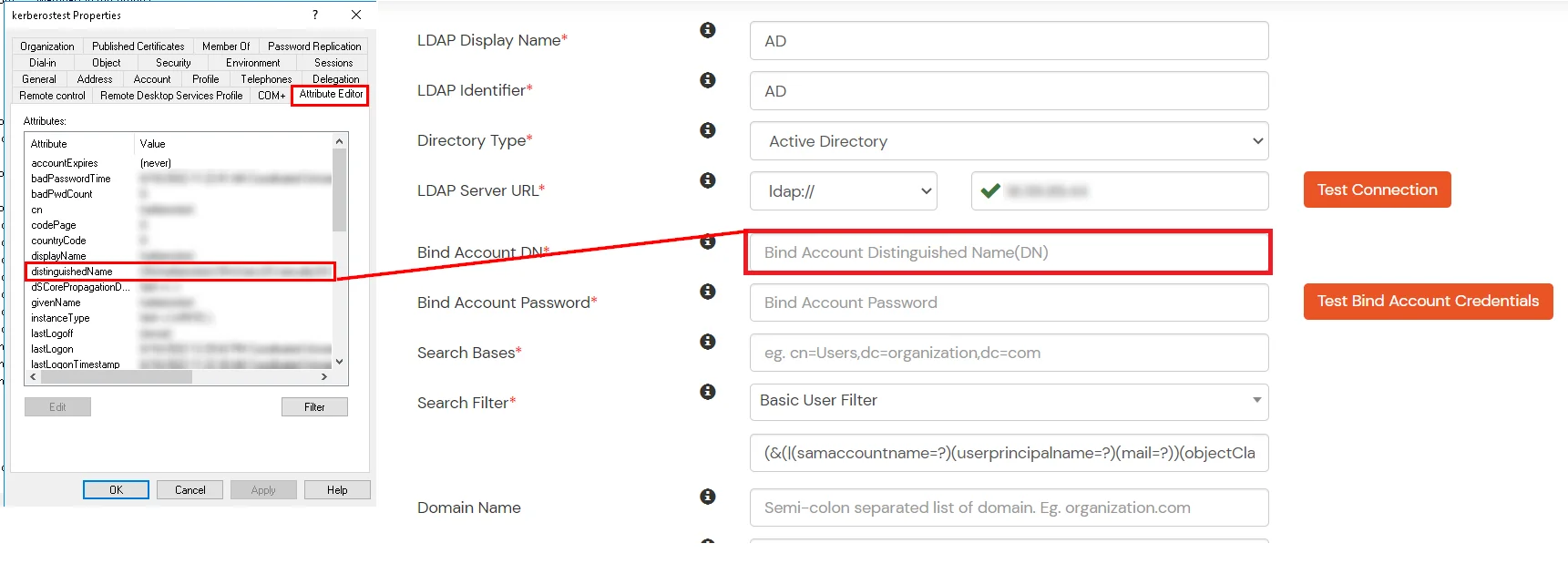
- Enter the valid Bind account Password.
- Click on the Test Bind Account Credentials button to verify your LDAP Bind credentials for LDAP connection.
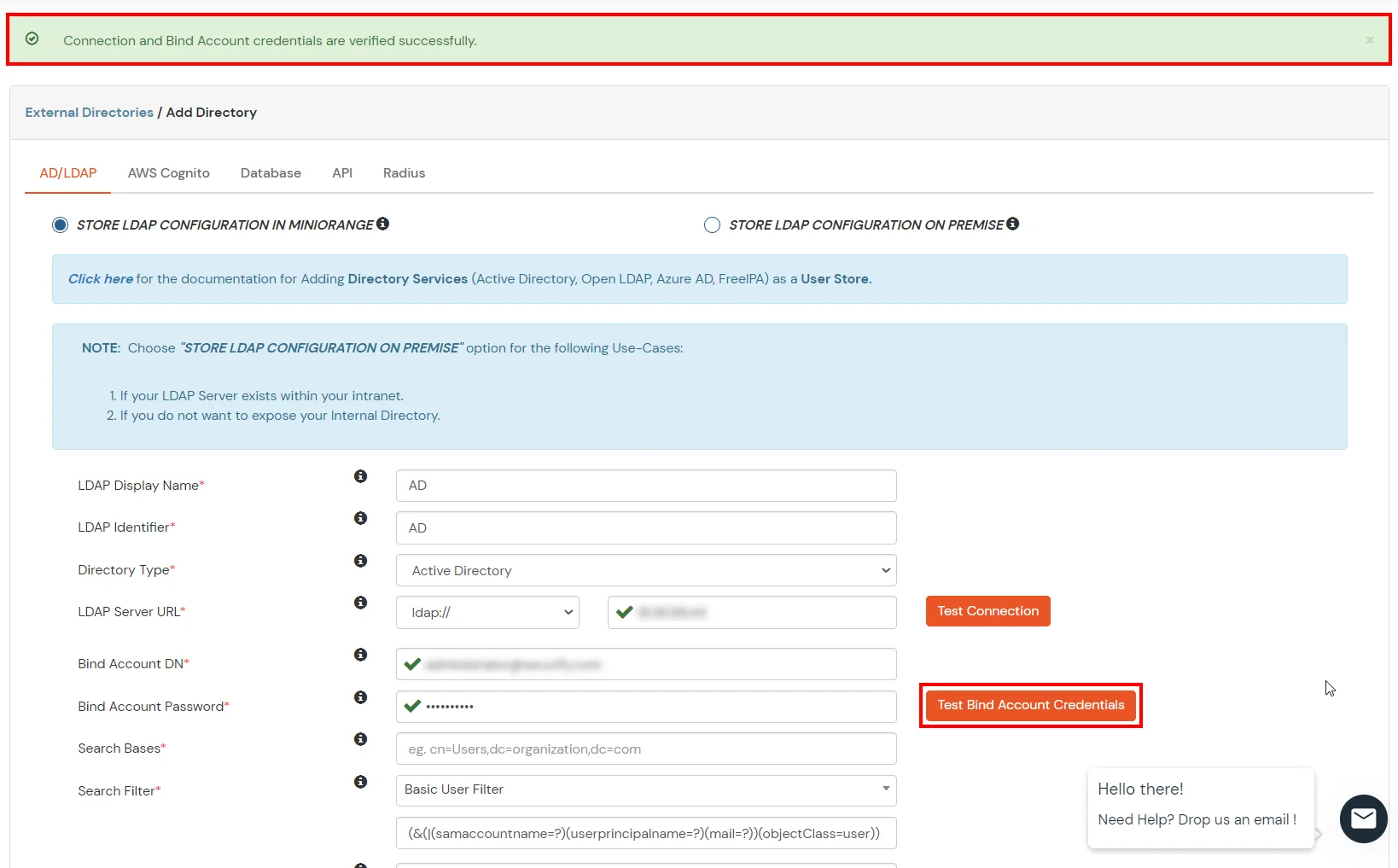
- Search Base is the location in the directory where the search for a user begins. You will get this from the same place you got your Distinguished name.
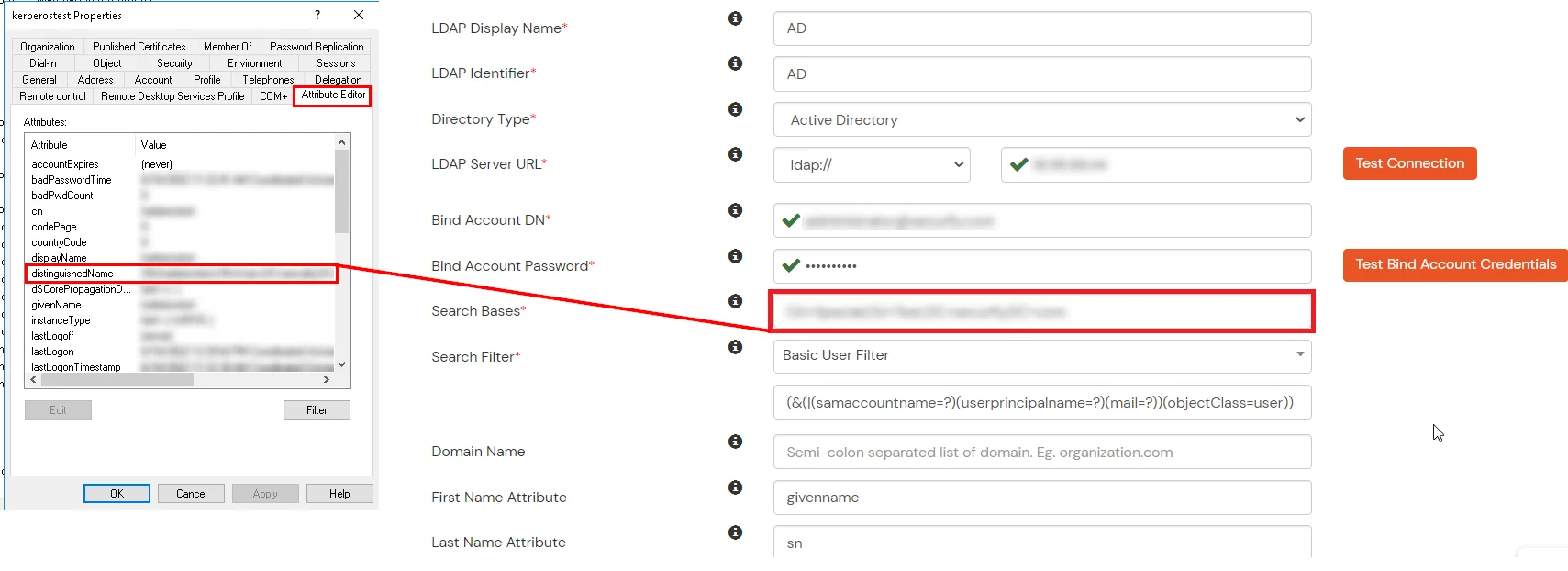
- Select a suitable Search filter from the drop-down menu. If you use User in Single Group Filter or User in Multiple Group Filter, replace the <group-dn> in the search filter with the distinguished name of the group in which your users are present. To use custom Search Filter select "Write your Custom Filter" option and customize it accordingly.
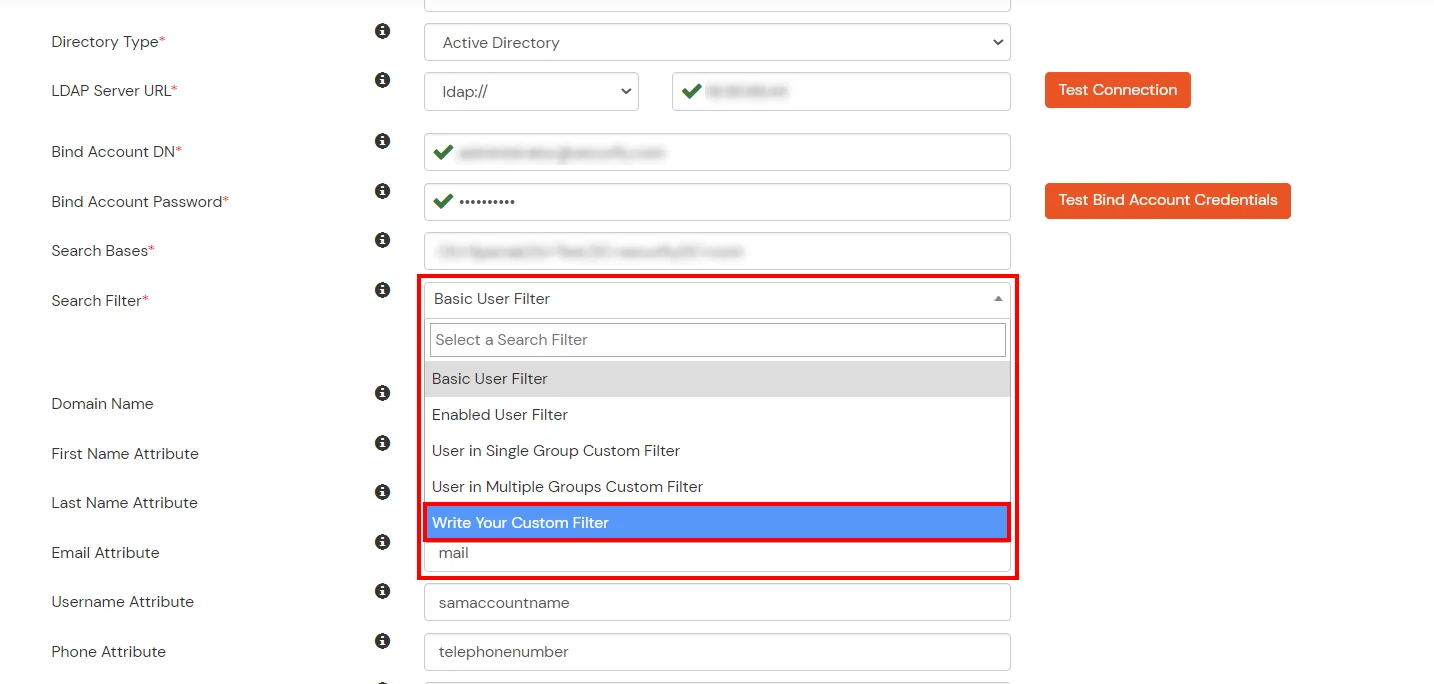
- Click on the Next button, or go to the Login Options tab.
- You can also configure following options while setting up AD. Enable Activate LDAP in order to authenticate users from AD/LDAP. Click on the Next button to add user store.
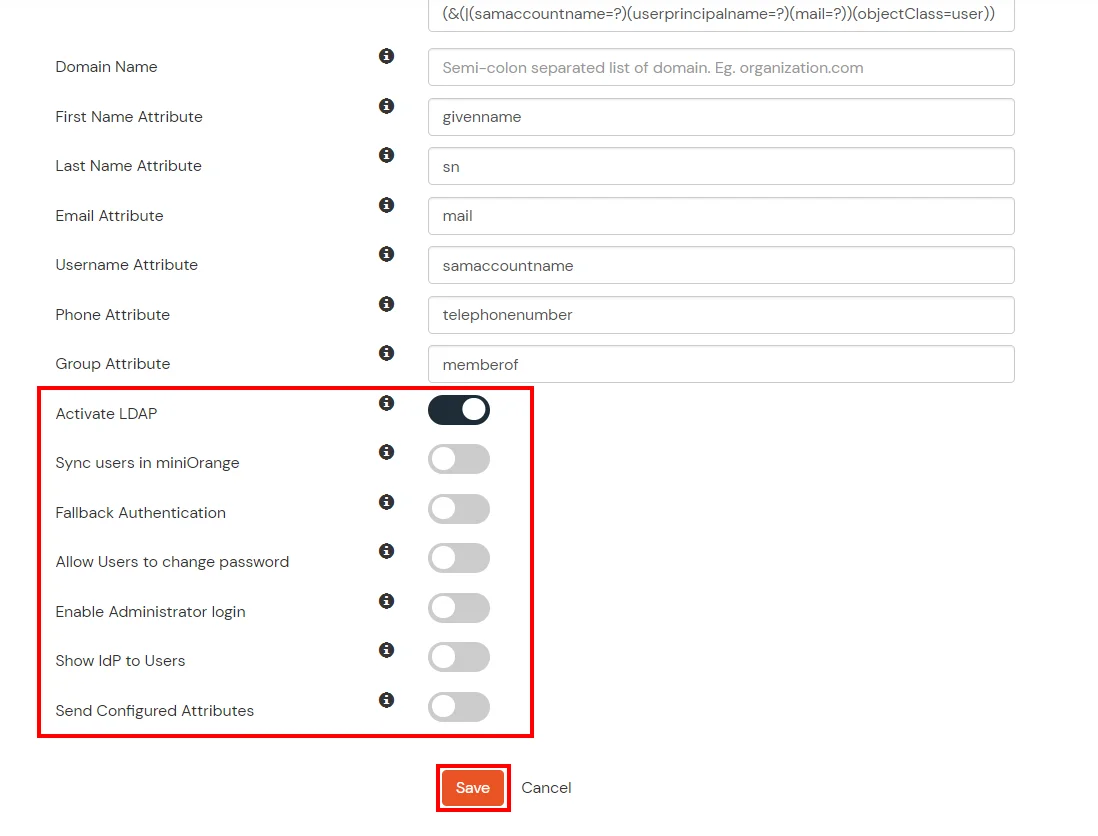
Here's the list of the attributes and what it does when we enable it. You can enable/disable accordingly.
| Attribute |
Description |
| Activate LDAP |
All user authentications will be done with LDAP credentials if you Activate it |
| Fallback Authentication |
If LDAP credentials fail then user will be authenticated through miniOrange |
| Enable administrator login |
On enabling this, your miniOrange Administrator login authenticates using your LDAP server |
| Show IdP to users |
If you enable this option, this IdP will be visible to users |
| Sync users in miniOrange |
Users will be created in miniOrange after authentication with LDAP |
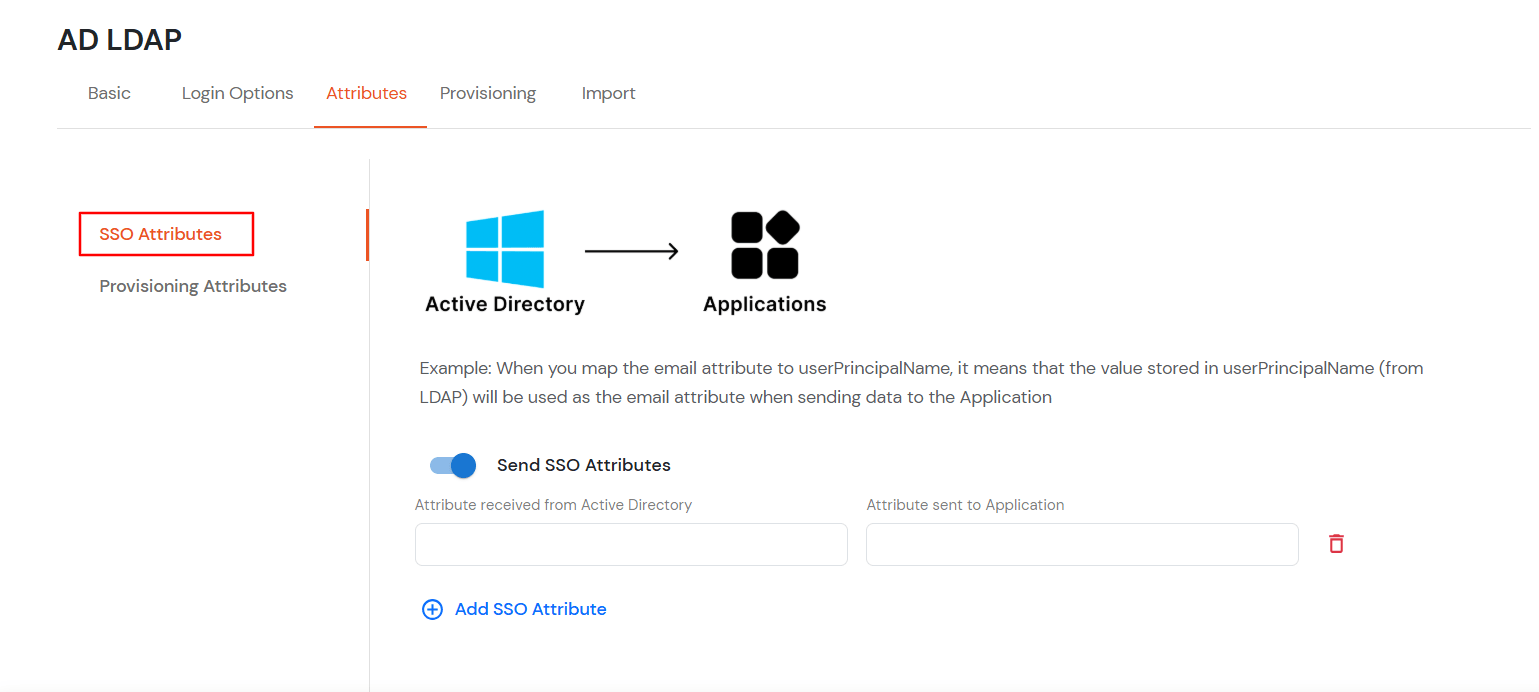
- Click on the Next button, or go to the Attributes tab.
Attributes Mapping from AD
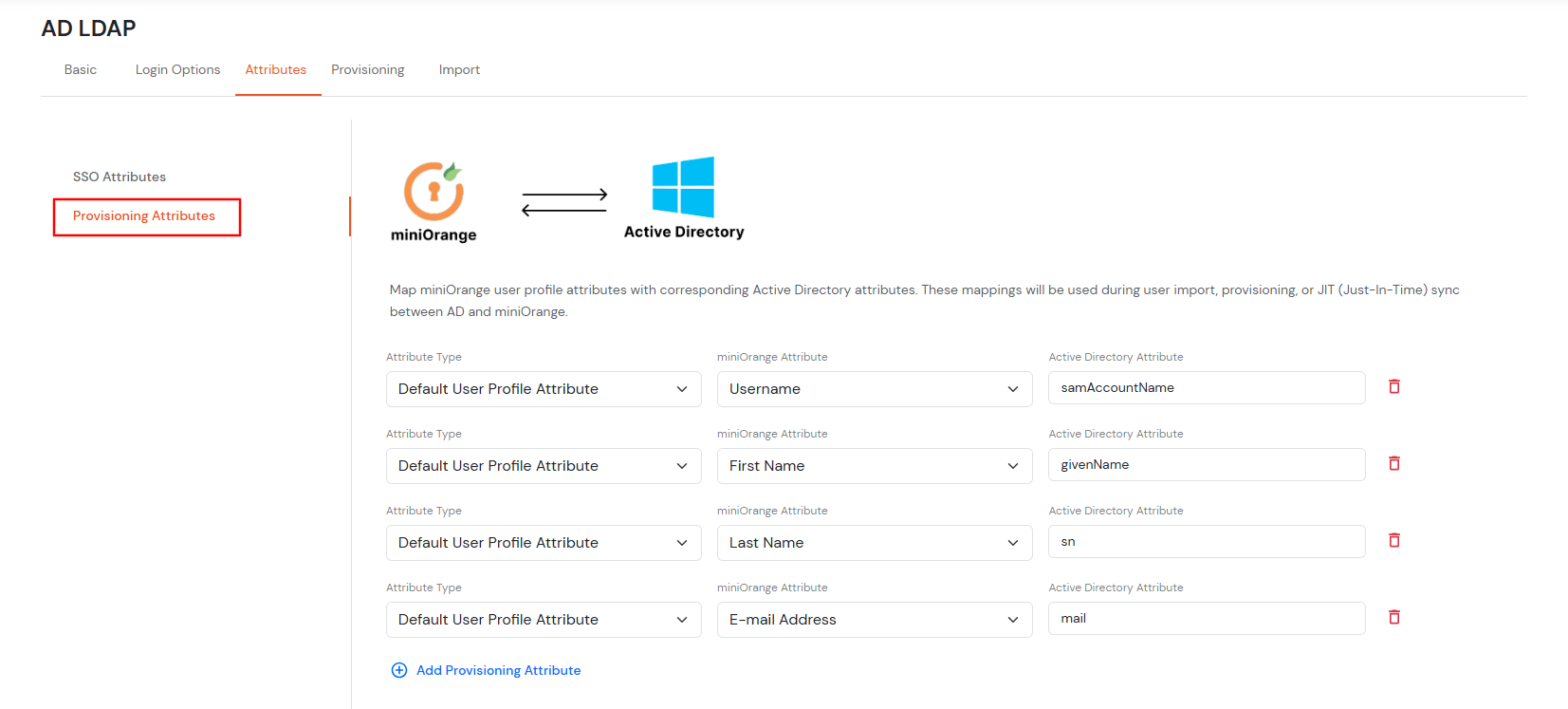
User Import and Provisioning from AD
- If you want to set up provisioning, click here for detailed information. We will skip this step for now.
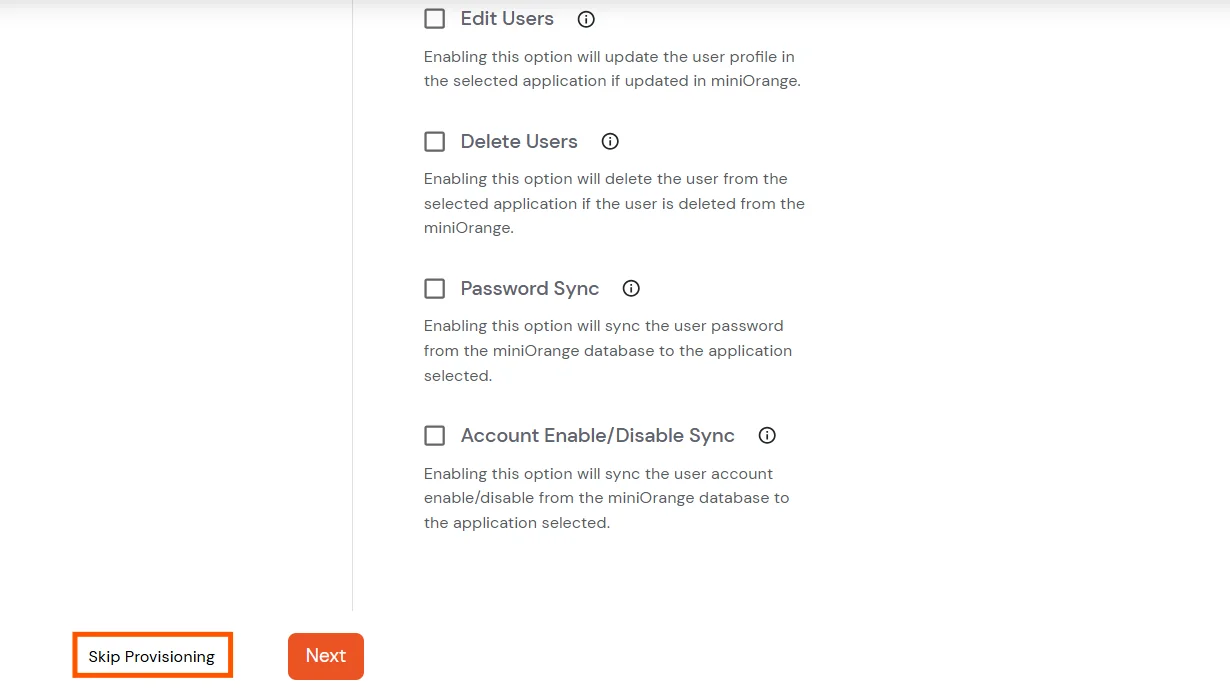
Test Connections
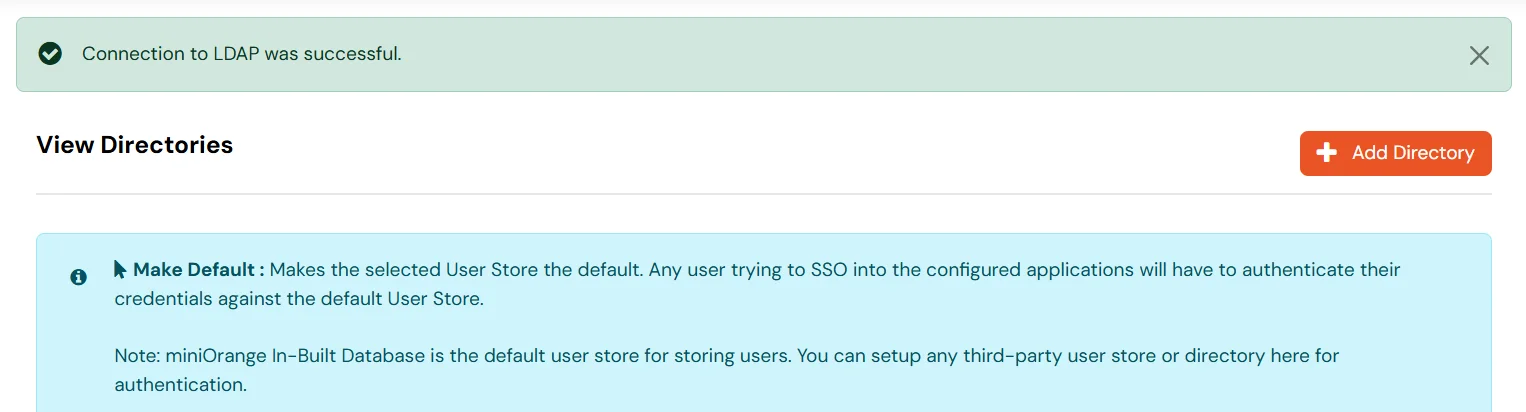
- You will see a list of directories under Identity Providers. From the dropdown, select AD/LDAP Directories, search for your configured directory, click the three dots next to it, and select Test Connection.
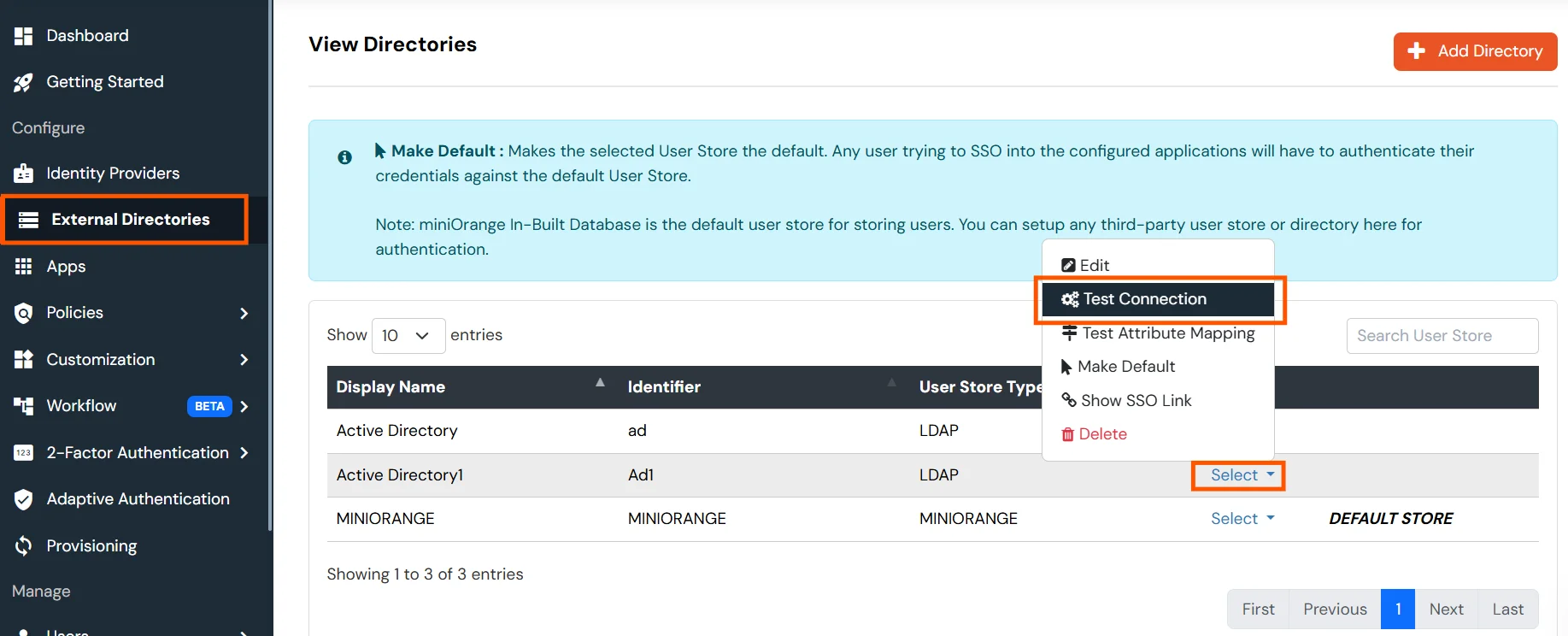
- A pop-up appears prompting you to enter a username and password to verify your LDAP configuration.
- On Successful connection with LDAP Server, a success message is shown.
Test Attribute Mapping
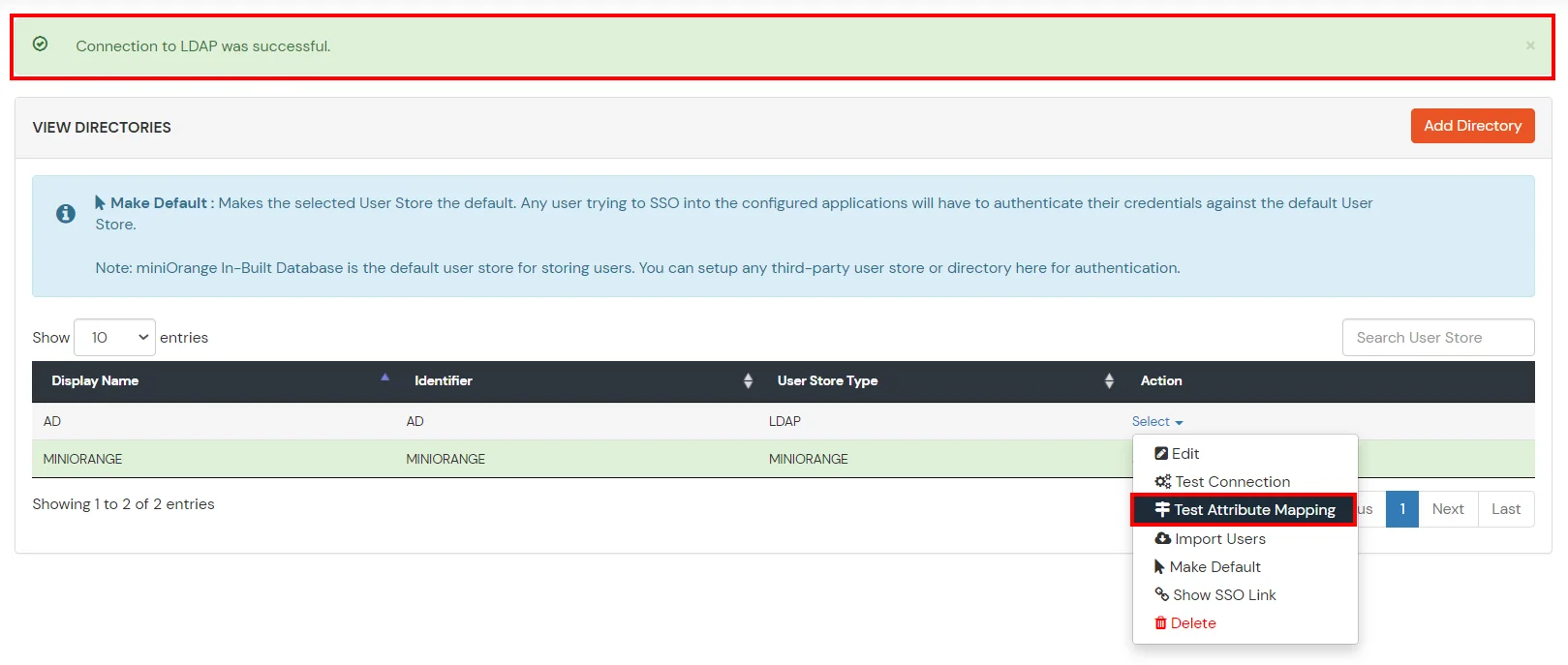
- You will see a list of directories under Identity Providers. From the dropdown, select AD/LDAP Directories, search for your configured directory, click the three dots next to it, and select Test Attribute Mapping.
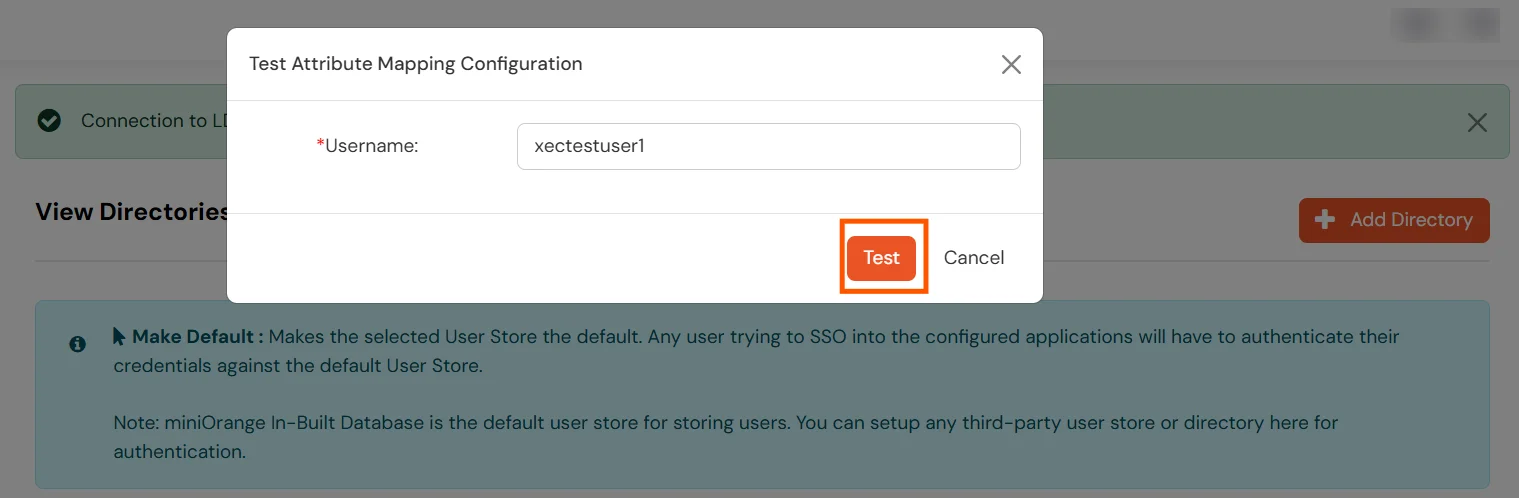
- A pop‑up appears to enter a username and click Test.
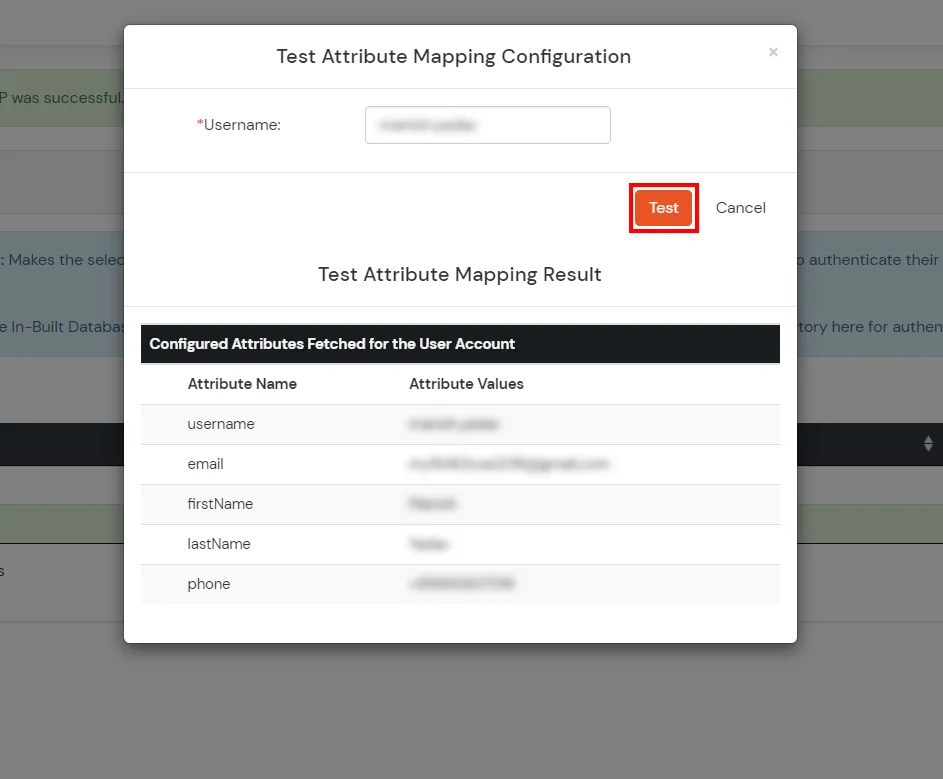
- The Test Attribute Mapping Result will be displayed.
Set up AD as External Directory configuration is complete.
Note: Refer our guide to setup LDAP on windows server.
miniOrange integrates with various external user sources such as directories, identity providers, and etc.
5. Run miniOrange SSO Connector over SSL (Optional)
Before moving forward, you need to make two changes related to samesite cookie. Starting with version 80,
Google Chrome will change the default value for the SameSite cookie parameter to Lax.
Therefore, changes are required and SameSite parameter has to be set to NONE.
To do changes, follow the path: miniorange-sso-connector >> moas >> WEB-INF >> classes. In this folder search for the
file spring-context-onpemise and open it in editor. Search for bean id="customCookie". you
will see a bean with name,samesite and secure properties. Update value of samesite from LAX to
NONE and of secure to true.
This document provides the steps to setup miniOrange SSO Connector over SSL.
5.1. Generate a Keystore
- Open a command prompt or terminal. And go to <Path to JAVA_HOME/bin> path and enter the
command given below.
keytool -genkey -alias miniorangessoconnector -keyalg RSA -keystore miniorangessoconnector.jks
- If you get a permission error (mostly on a windows machine) in this step.Then change the location
in command prompt or terminal to Desktop or any other location of your choice. See image in Step 2.
- Enter your convenient password and remember it.(If the password you entered didn’t work then keep
the password as “changeit” ).
5.2. Generate SSL Certificate
- After Pressing the Return key it will prompt for a password for . Hit Return to
continue.
(Note: firstname and lastname needs to be the server DNS name/hostname of the
server)
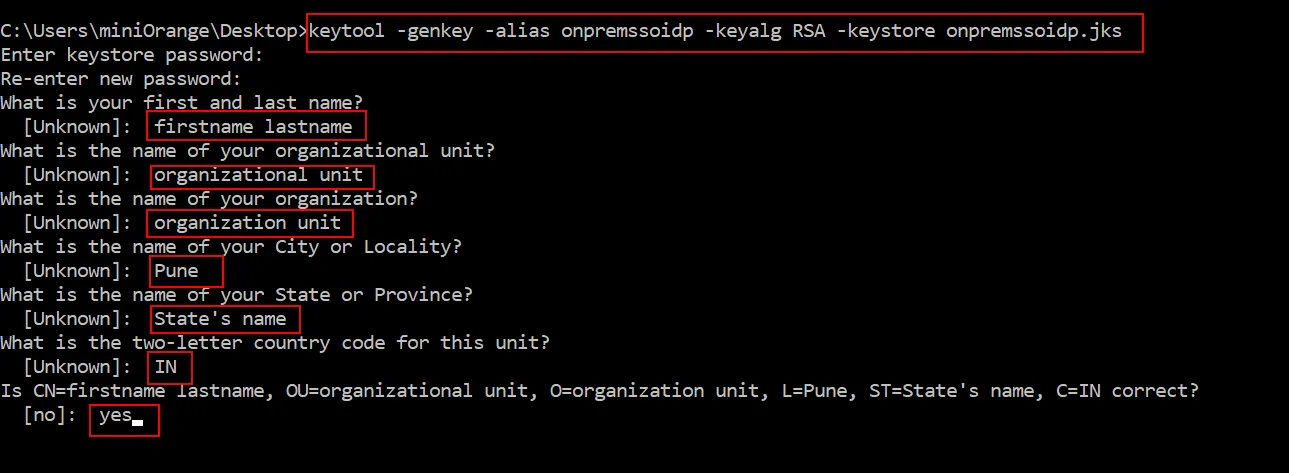
- SSL self-signed certificate is generated at the given location.
5.3. Configure Tomcat with above-generated Keystore
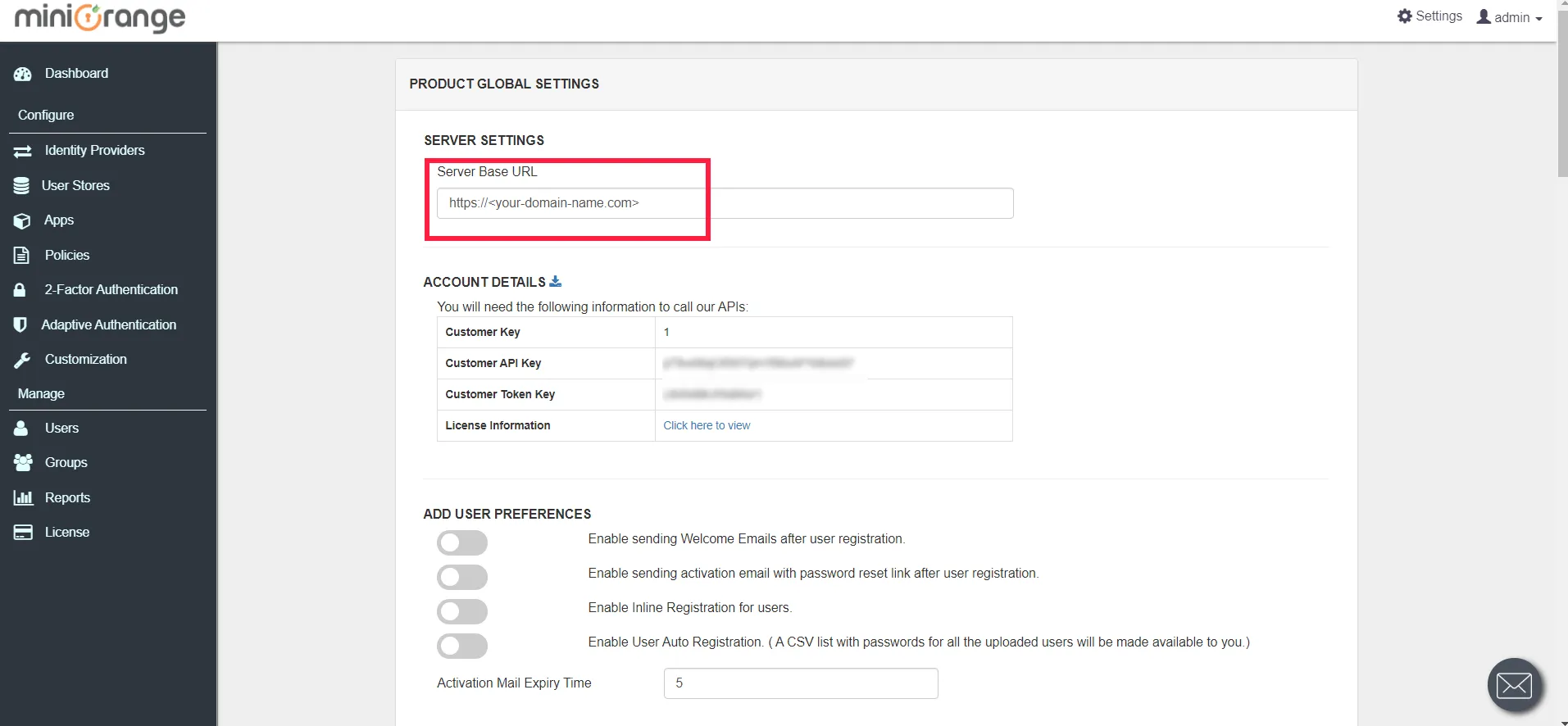
5.4: Modify the Server Base URL in General Product Settings in the miniOrange SSO Connector
- You should now be able to access the deployed miniOrange SSO Connector over HTTPS.
- From miniOrange admin dashboard, go to Settings >> Product settings (present on top right).
- Enter the Server base URL as shown in the image below.
6. Run Tomcat as a Service for miniOrange SSO Connector (Optional)
- For Windows:
- Install Tomcat as Windows Service using a Windows
Installer.
- Navigate to Tomcat Package that was provided by us and copy over the moas folder to the newly
installed Tomcat as a service directory root.
- Navigate to Tomcat As a Service Directory Root\conf and edit the server.xml file.
- Search for <Host name="localhost" appBase="webapps"
unpackWARs="true" autoDeploy="true"> in the file.
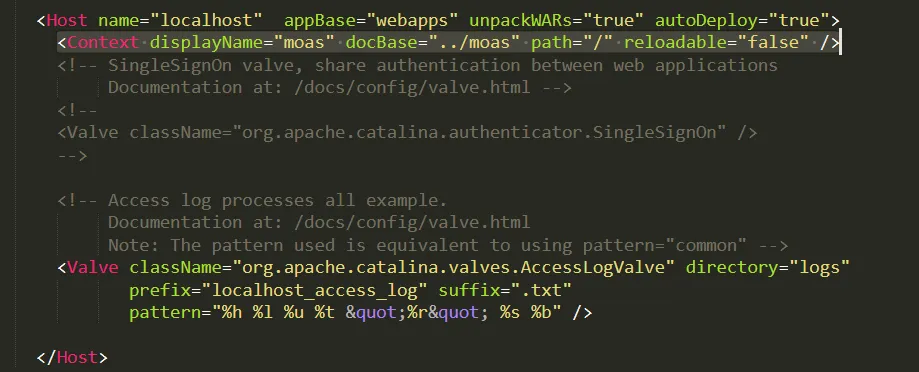
- Add this line: <Context displayName="moas" docBase="../moas" path="/" reloadable="false" />
just below the line you searched for
- Now you can navigate to the windows services panel and start the Tomcat service.
External References
Note
Oracle and Java are registered trademarks of Oracle and/or its affiliates. miniOrange is a separate entity.