Hello there!
Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×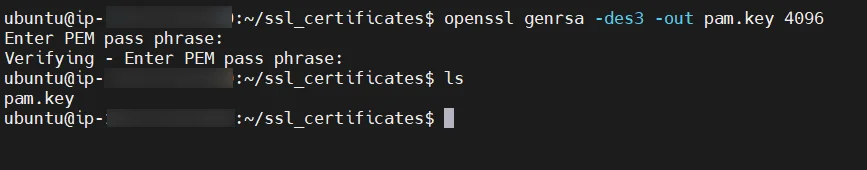
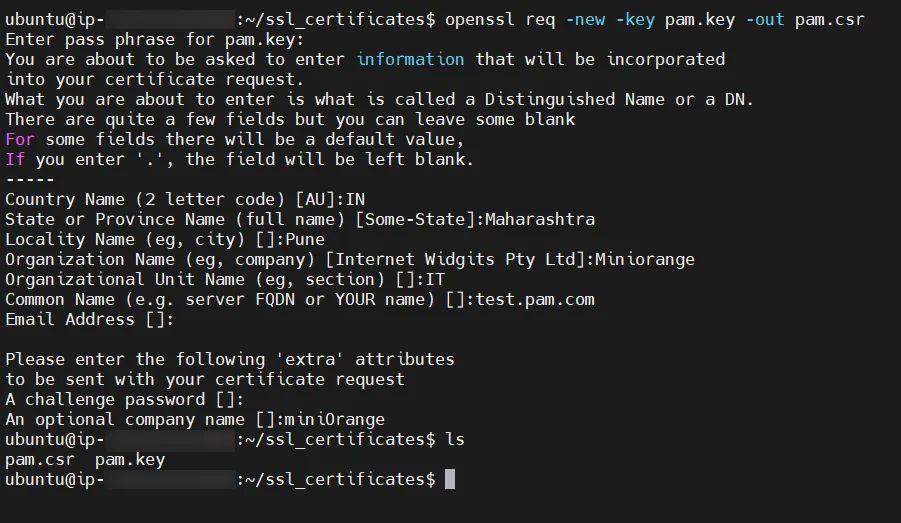
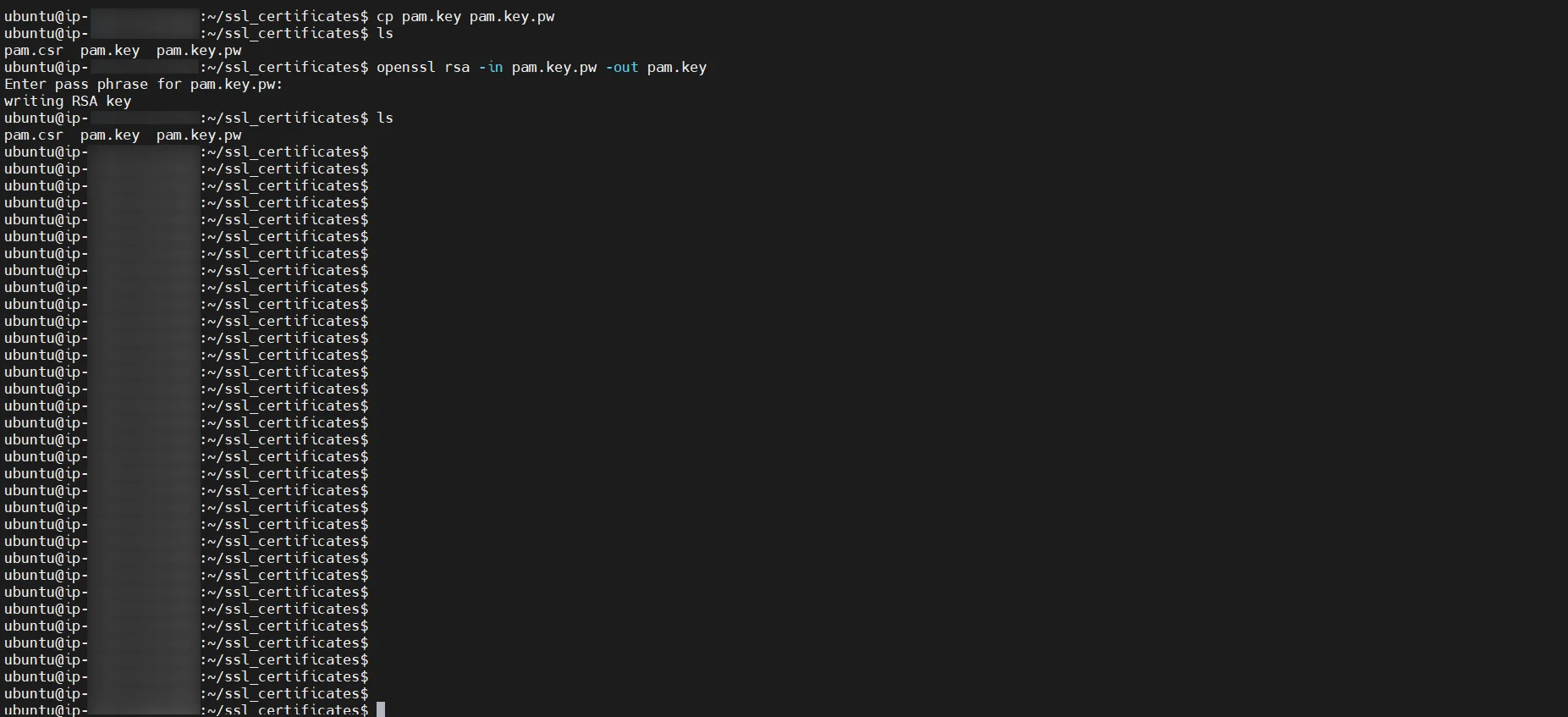
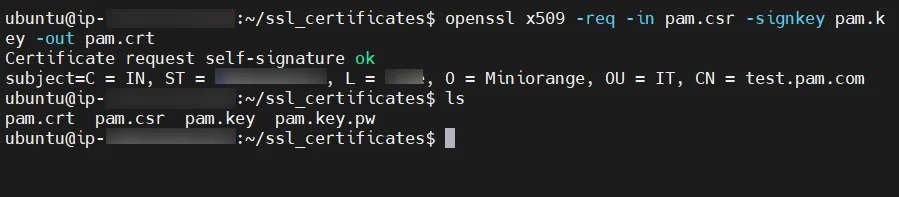
server {
listen 80 default_server;
listen [::]:80 default_server;
server_name _;
client_max_body_size 100M;
listen 443 ssl;
server_name test.pam.com;
ssl_certificate /etc/nginx/ssl/pam.crt;
ssl_certificate_key /etc/nginx/ssl/pam.key;
ssl_session_timeout 5m;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2 TLSv1.3;
ssl_ciphers HIGH:!aNULL:!MD5;
location / {
root /var/www/html;
index index.html;
try_files $uri /index.html;
}
location /apps {
rewrite ^/apps(.*) $1 break;
proxy_pass http://unix:/run/mopam.sock;
proxy_http_version 1.1;proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_set_header Host $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
location /openid {
proxy_pass http://unix:/run/oauth2client.sock;
proxy_set_header Host $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
location /audits {
proxy_pass http://unix:/run/audits.sock;
proxy_set_header Host $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
location /apps/static/ {
alias /home/ubuntu/pam/mopam/static/;
}
location /apps/media/ {
alias /home/ubuntu/pam/mopam/media/;
}
location /openid/static/ {
alias /home/ubuntu/pam/oauth2client/static/;
}
location /audits/static/ {
alias /home/ubuntu/pam/audits/static/;
}
}
Now restart nginx using sudo systemctl restart nginx.service